Cyber security risk, tied with today's burning environmental and supply chain issues are the top threat to organisation growth over the next three years.
Building trust with your customers, partners and stakeholders is the ultimate business enabler in the digital era where risk and regulations have to be embedded in the transformation journey to ensure growth and high performance. Providing online services through conscious decisions to respect the environment and society by implementing robust ESG (Environmental, Social and Governance) frameworks shows responsibility and encourages customers to choose your products instead of competitors.
Alignment or compliance with any leading ISMS (Information Security Management System) generates trust in the market for both customers and business partners. It also proves that your organisation, and its employees take data security seriously, have the right governance in place and are continually monitoring for better performance, efficiency, and compliance both internally and for their external providers.
 It is a
misconception to think that Gaming companies only derive value in
aligning their organisation to the comprehensive characteristics of
internationally recognised information security standards such as
ISO/IEC 27001 or NIST purely for regulatory compliance.
It is a
misconception to think that Gaming companies only derive value in
aligning their organisation to the comprehensive characteristics of
internationally recognised information security standards such as
ISO/IEC 27001 or NIST purely for regulatory compliance.
The truth is that protecting reputation and information is of paramount importance for all companies, and being trusted is a key element of business success.
Complying to today's regulations, laws and data privacy requirements is a burden for many Gaming companies, in particular those who do not have a strategic approach to information security. By following an ISMS framework, all of your organisation will be working strategically to improve the security posture and be aware of what threats exist and what actions to take if malicious activity or cybercrime is detected. By following such an approach, Gaming companies can be more proactive, know where their critical assets and information reside, and be constantly monitoring their providers, subcontractors, and assets for compliance.
Segregation of duties and defining the correct roles and responsibilities for your Platform and IT systems are important in order to provide the right level of access to the infrastructure and data. Roles and responsibilities have to be defined, documented and evolved throughout the life of the organisation and of course implemented correctly. An ISMS provides the necessary insight to structure the roles and provide resiliency in case of threats to the employees (such as a pandemic) to help your company continue working. Access control is important especially with cloud-based operating environments to provide operational permissions only to specific infrastructure or data.
Keeping up to date with the always evolving threats is a headache and Information security policies need to provide rules and guidelines to your employees to build and protect the company infrastructure. By adhering to a strategic ISMS, your policies and procedures will be appropriately aligned to provide best coverage from attacks and minimise risks to an acceptable level.
Having appropriate policies defined is a good starting point,
but it is not enough.  Your employees must know what
the Information Security Policy and procedures are, what the rules
of the organisation are, what are their roles in the proper
execution, what to do in case of a security breach or cyber-attack.
Awareness training will drive your employees to
keep themselves updated and be able to identify malicious attacks,
stop them and recover services or data to keep delivering the
services.
Your employees must know what
the Information Security Policy and procedures are, what the rules
of the organisation are, what are their roles in the proper
execution, what to do in case of a security breach or cyber-attack.
Awareness training will drive your employees to
keep themselves updated and be able to identify malicious attacks,
stop them and recover services or data to keep delivering the
services.
Recovering from a malicious attack or data corruption requires appropriate Incident Response, Business Continuity (BCP) and Disaster Recovery (DR) plans. Once a system or data is compromised there's no time to play around and your Operations Team must already know what to do and how to do it efficiently. BCP and DR testing have to be carried out periodically, keeping records of success, failures, and lessons learned during the exercise. An ISMS provides a strategic approach to having your Gaming Platform resilient to attacks and having procedures and human resources available to handle adverse conditions and keep working with least disruption. Resiliency is not just on the technology aspect, but also on the human resources and knowledge sharing, which is required to make the systems failover to another site or recover from backups in case of major disaster.
 Changes are always
happening to your Platform and infrastructure either to provide new
products or to improve current services for better user experience,
however these have to be carried out without disruption and without
introducing security vulnerabilities in the systems. An ISMS will
help you have the appropriate documentation in place and be in a
position to deploy changes when required with appropriate approvals
both from internal stakeholders and the Authorities.
Changes are always
happening to your Platform and infrastructure either to provide new
products or to improve current services for better user experience,
however these have to be carried out without disruption and without
introducing security vulnerabilities in the systems. An ISMS will
help you have the appropriate documentation in place and be in a
position to deploy changes when required with appropriate approvals
both from internal stakeholders and the Authorities.
Third party suppliers and partners are an integral part of how the Gaming industry ecosystems operate. Having the right contracts, security requirements and security reviews in place help you to understand what risks these suppliers and partners bring to your business and continuously monitor their service levels. Third party suppliers and partners must also comply with Gaming requirements and have appropriate protection, redundancy, incident management and business continuity plans in place to continue offering their services to you, even when under attack.
Are you just complying with regulations, or are you being proactive and using information security management frameworks to ensure alignment to industry best practices? How important is the business to you? Having an ISMS in place helps you not just comply with the minimum regulations but provide protection, detection and recovery mechanisms to keep your business working even when under attack.
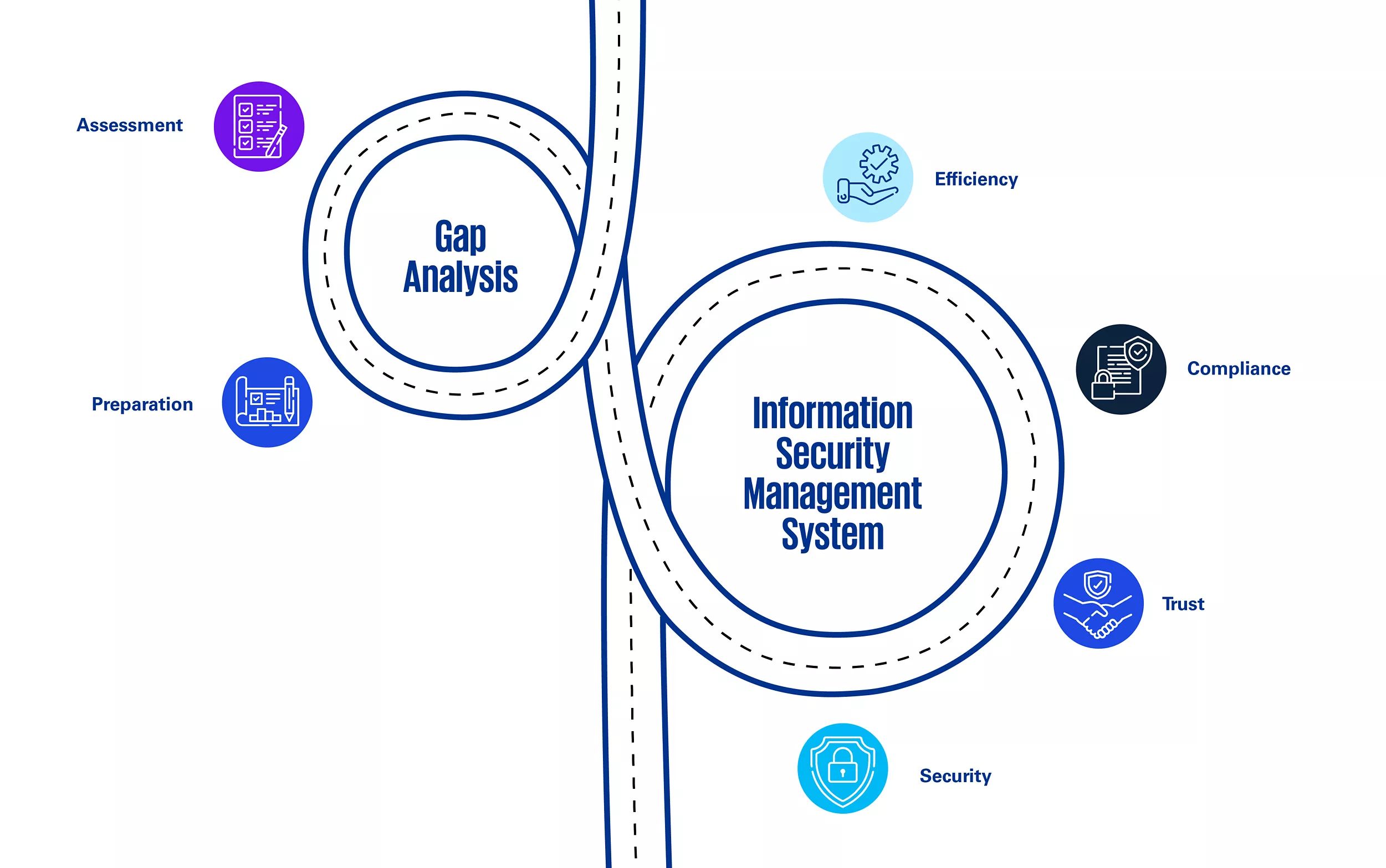
Gap Analysis or Implementation Assessment
Performing a Gap Analysis or Implementation Assessment against the best practices and internationally recognised information security management system standards supports your understanding of the areas that require attention, potential necessary changes to policies, procedures, and work practices.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.



