- with readers working within the Retail & Leisure industries
Cross-border transfer of personal information (hereinafter referred to as "PI"1 and the cross-border transfer of PI as "PI export") is a daily occurrence and business necessity for many companies operated in China, especially for multinational companies and domestic companies using ERP software provided by foreign operators with servers located abroad. With the continuous release of supporting rules of the Personal Information Protection Law ("PIPL") in terms of restrictions on PI export in China, PI export compliance is attracting increasing attention.
This series consists of four articles. The first article will introduce the development and framework of China's restrictions on PI export, and the next three articles will respectively introduce the three PI export mechanisms provided by the PIPL in detail, namely the compulsory notification mechanism (Security Assessment) and two self-management mechanisms (Standard Contract & Certification).
The is the second of the four articles and will review the PI export mechanism of Security Assessment under the Chinese PIPL from the perspective of local practitioners.
Security Assessment is a graduated mechanism based on the nature of the PI handler and the quantity of PI involved. So far, the mechanism has become relatively mature. On the one hand, the Security Assessment Measures for Data Export (《数据出境安全评估办法》in Chinese, "Security Assessment Measures") and the Notification Guideline for Security Assessment of Data Export (First Edition) (《数据出境安全评估申报指南(第一版)》in Chinese, "Security Assessment Guideline") have been in force for more than 6 months, and the grace period provided by the Security Assessment Measures has expired (i.e., until Feb. 28, 2023). On the other hand, many entities have submitted filings to local provincial cyberspace administrations ("CA"), among whom a few have passed the assessment conducted by the CAC.
- Who is caught by the Security Assessment?
For PI export, Security Assessment is only mandatory for the following PI handler who:
- has been identified as a CIIO;
- has processed PI2 of more than 1 million individuals;
- has exported PI of more than 100,000 individuals accumulatively since January 1 of the preceding year; or
- has exported sensitive PI3 of more than 10,000 individuals accumulatively since January 1 of the preceding year.
According to the literal meaning of the Security Assessment Measures, we understand that the PI handler is the basis of calculation to determine whether certain thresholds are satisfied. Therefore, entities that acting as PI handlers within the Group company shall calculate their volume of processed PI separately.
Moreover, since the criteria of the Security Assessment Measures include variables, PI handlers falling below the abovementioned thresholds shall constantly monitor the volume of PI they export, particularly in the latter part of the year (e.g., Q4) as this determines whether they are likely to be caught within the threshold listed above.
- What materials are required for Security Assessment?
According to the Security Assessment Measures and the Security Assessment Guideline, the following materials are required:
- application form filled in based on the template provided by the Security Assessment Guideline;
- cross-border data transfer self-assessment report drafted based on the template provided by the Security Assessment Guideline;
- legal documents to be concluded between the PI handler and the overseas recipient containing the mandatory contents from six aspects provided by the Security Assessment Measures; and
- other materials required for Security Assessment provided by
the Security Assessment Guideline, such as the identity
documents of the PI handler, and by the case handler.
- What is the procedure of the Security Assessment?
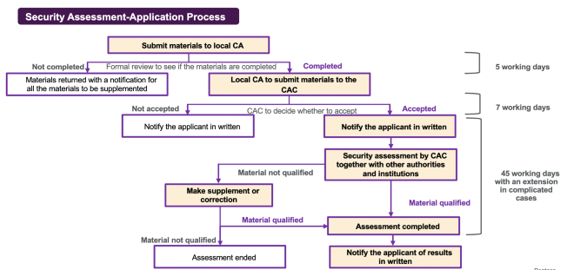
Security Assessment shall be applied to the CAC through the local CA at the provincial level. As illustrated in the following flow chart, it normally takes 57 working days for one Security Assessment. However, if the PI handler has any objection to the assessment result, it can apply to the CAC for re-assessment within 15 working days upon receiving the assessment result, and the re-assessment result shall be the final decision.
- Which authority will review the Security Assessment application?
Although the materials shall be submitted to the provincial CA for completeness review, it is the national cyberspace administration authority, i.e., the CAC, who organizes the relevant departments of the State Council, the cyberspace administration concerned at the provincial level and specialized agencies to carry out the substantive review.
- How long does it take for one Security Assessment?
In general, one complete Security Assessment should take no more than 57 working days (excluding the time spent on self-assessment which usually takes 3-6 months depending on various circumstances). However, if the situation is complicated or supplementary or corrected materials are needed, the assessment may be extended.
As Security Assessment is focused on the assessment of the risks to national security, public interests, or the legitimate rights and interests of individuals or organizations that may be caused by the activity of the PI export, the following factors will affect the result of Security Assessment:
- the legality, legitimacy and necessity of the purpose, scope, and method of the PI export;
- the impact of the data security protection policies and regulations and the cybersecurity environment of the country or region where the overseas recipient is located on the security of data to be provided abroad, and whether the data protection level of the overseas recipient meets the requirements of the laws and administrative regulations of the People's Republic of China and mandatory national standards;
- the size, scope, types and sensitivity of the PI to be provided abroad, and the risks that the PI may be tampered with, destroyed, divulged, lost, transferred, illegally obtained or illegally used during and after the PI is provided abroad;
- whether data security and PI rights and interests can be fully and effectively guaranteed;
- whether the legal documents to be concluded by the PI handler and the overseas recipient have fully agreed on the responsibilities and obligations of data security protection;
- compliance with Chinese laws, administrative regulations and departmental rules; and
- other matters that the CAC considers necessary to assess.
- How long is Security Assessment valid?
The validity period of the result of the cross-border data transfer Security Assessment is 2 years, calculated from the date of issuance of the assessment result.
- When is re-application triggered?
The following circumstances will trigger the re-application:
- when the validity period (2 years) has expired;
- when the activities of cross-border transfer has changed (for example, the purpose, method, scope and type of PI provided overseas, and the purpose and method of PI processing by overseas recipients has changed, affecting the security of cross-border data transferred, or the overseas storage period of PI has changed);
- when the security of the PI provided abroad is affected due to changes in the data security protection policies or regulations or the cybersecurity environment of the country or region where the overseas recipient is located, any other force majeure event, or any change in the actual control of the PI handler or the overseas recipient, or any change in the legal documents between the PI handler and the overseas recipient; and
- when any other circumstance affecting the security of the PI provided abroad arises.
Footnoes
1 Under the PIPL, PI is defined as any kind of information, electronically or otherwise recorded, related to an identified or identifiable natural person within PRC, excluding anonymized information that cannot be used to identify a specific natural person and is not reversible after anonymization.
2 Under PIPL, PI is defined as any kind of information, electronically or otherwise recorded, related to an identified or identifiable natural person within PRC, excluding anonymized information that cannot be used to identify a specific natural person and is not reversible after anonymization.
3 Under PIPL, sensitive PI is PI that if disclosed or illegally used, may cause harm to the security or dignity of natural persons, including information on biometric characteristics, religious beliefs, specific identity, medical health, financial accounts, individual location tracking, any PI of a minor under the age of 14, etc.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.



