Every year, BakerHostetler collects, analyzes and compares key metrics on the incident response matters we handled in the prior year. The Data Security Incident Response (DSIR) Report presents key findings and trends, along with insights to assist companies in improving their cybersecurity measures, incident response plans and information governance practices.
Our 2025 DSIR Report includes data on the more than 1,250 incidents we helped clients manage in 2024. Below we've highlighted some key findings from the data – the heart of the report.
Network Intrusions
Network intrusions are once again the most prevalent type of incident our clients experience – representing nearly half (47 percent) of all the matters we handled last year.
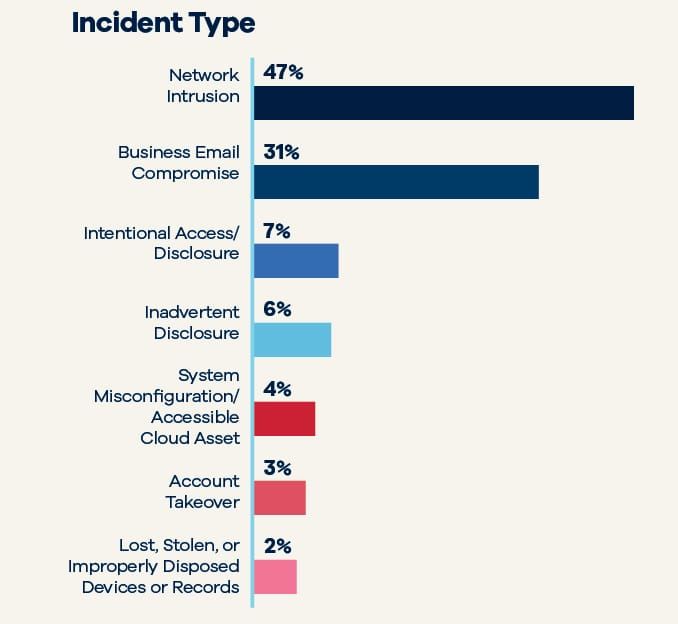
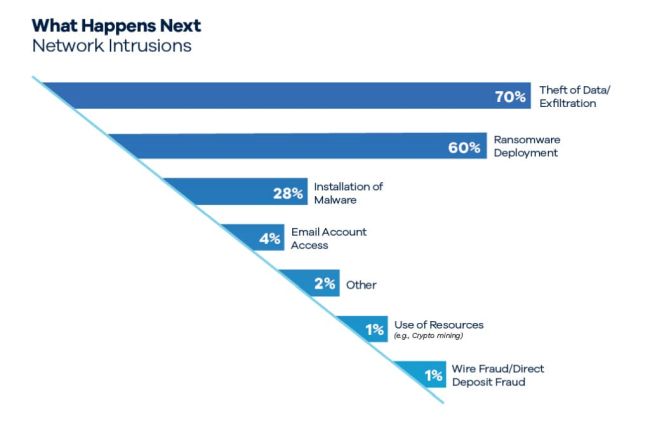
Notably, in terms of prevalence, ransomware deployment and data theft swapped places compared with the prior year. In 2023, 72 percent of the network intrusion matters involved ransomware and 57 percent involved theft of data. In 2024, however, 70 percent of network intrusions involved data theft while 60 percent involved ransomware. This trend is not surprising – we are seeing more threat actors skip the encryption step altogether and only exfiltrate data.
Even though more clients paid a ransom in 2024 (36 percent) than in 2023 (27 percent), the average ransom paid in 2024 decreased by almost $250,000 (after removing a large outlier payment).
Another encouraging trend is that the percentage of matters involving theft of data leading to notice to individuals decreased from 76 percent in 2023 to 62 percent in 2024. Clients are implementing tools and policies to reduce the amount of files containing personal information, such as Social Security numbers, stored in file shares – the most common place where threat actors find and steal data in a network intrusion.
Forensic Investigations
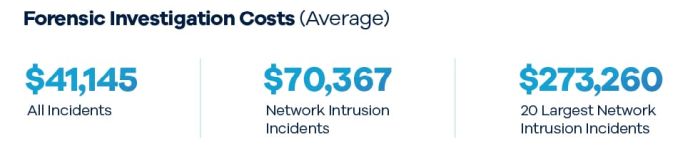
Costs of forensic investigations continue to drop. The year 2024 marked a three-year low and a 30 percent reduction, with the average cost for all incidents coming to $41,145 and the average cost for network intrusions coming to $70,367. Multiple factors are working together to continue driving this trend: 1) use of EDR (endpoint detection and response) and triage collection tools, leading to quicker investigations; 2) use of a SIEM (security information and event management system) and increased cloud usage and virtualization, making it easier to access and share host and network logs to support the investigation; 3) a more mature industry, with more forensic firms, leading to increased competition and innovation; and 4) efficiencies driving business email compromise investigation costs down.
Social Engineering
As organizations' cybersecurity programs become more mature, their technical controls and tools work to prevent or mitigate most attacks. But threat actors are leveraging social engineering techniques to get around these controls, exploiting human nature to manipulate a person into providing data or access to a device or system. We are seeing an increase in incidents where social engineering was the initial entry method (e.g., the threat actor calling the help desk to reset someone's credentials, thereby gaining access to that person's account) as well as attacks where the threat actor socially engineers an employee to convince them to allow the threat actor to remotely access their device (e.g., the threat actor calls an employee pretending to be someone from the IT department who needs to remotely access the employee's device to fix an issue). These tactics are contributing to the increase in data exfiltration and a decrease in the use of malware during network intrusion matters (which is also due to threat actors more frequently using the tools found within the organization's own environment to carry out an attack).
Having security controls such as MFA can reduce the likelihood of a successful attack, but security awareness training is still key. The most effective defense against social engineering is an aware, skeptical, well-trained, and battle-tested human working in conjunction with strong technical safeguards.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

