- within Government and Public Sector topic(s)
- in United States
- within Government and Public Sector topic(s)
- in United States
- with readers working within the Oil & Gas and Construction & Engineering industries
- within Intellectual Property, Immigration and Family and Matrimonial topic(s)
The wait is finally over, and U.S. Department of Defense (DoD) contractors need to be prepared. On September 10, 2025, DoD posted afinal rulethat will officially make Cybersecurity Maturity Model Certification (CMMC) a reality for many contractors starting November 10, 2025. The program is designed to address longstanding contractor cybersecurity vulnerabilities that have led to losses of sensitive government information and financial harm to the government. In full effect, the CMMC will apply to over 300,000 entities across a wide range of industries, from construction to healthcare and beyond, with few, if any, exceptions.
CMMC Program Overview
The CMMC program, developed over several years, is designed to protect DoD's information security systems and intellectual property. The program will apply to DoD contractors, outside of solely commercial off-the-shelf items (COTS), whose information systems store government-controlled unclassified information (CUI) and Federal Contract Information (FCI). To secure federal contracts, contractors must comply with specific cybersecurity requirements and undergo various types of assessments. Originally introduced inSeptember 2020and followed by rigorous reviews, criticism, and significant amendments, the CMMC program is now approaching the final stages of implementation. You can see previous Cozen O'Connor coverage of the issuehere.
As a quick reminder, the CMMC framework incorporates information security standards established by the National Institute of Standards and Technology (NIST) in their Special Publications (SP), specifically NIST SP 800-171 Rev. 2,Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, and a subset of the requirements from NIST SP 800-172,Enhanced Security Requirements for Protecting Controlled Unclassified Information: A Supplement to NIST Special Publication 800-171. Using these standards as a guide, contractors must undergo varying levels of assessments, based on the sensitivity of information, to demonstrate that their information systems handling CUI and FCI meet NIST's practices and technical requirements.
CMMC creates a three-tier certification model of compliance – Levels 1 through 3 – based on the type and sensitivity of information. Contractors with Level 1 certification are authorized to handle FCI; Level 2 – CUI; and Level 3 – sensitive CUI, as designated by the DoD.
The CMMC program has been implemented through two final rules. The first, finalized inOctober 2024, established the framework, procedures, and assessment mechanics for CMMC certifications. The second rule, issued on September 10, 2025, outlines and revises DFARS clauses to be included in contracts as directed by the process set forth in the October 2024 rule. Additionally, the September 10 CMMC clause rule addresses policies, contract clauses, and provisions for implementing the October 2024 framework.
The September 10 CMMC clause rule includes a contractual clause DFARS 252.204-7021,Contractor Compliance with the Cybersecurity Maturity Model Certification Level Requirements, as well as a new provision DFARS 252.204-7025 Notice of Cybersecurity Maturity Model Certification Level Requirements. The former clause is prescribed for use in solicitations and contracts that require the contractor to have a specific CMMC level. The latter requires contractors to include in their proposals current CMMC status, an affirmation of ongoing compliance, and unique identifiers for each system used to process FCI or CUI.
Summary of the Updates to the September 10 Final Rule
The September 10 final rule implements a variety of updates and revisions described in greater detail below in theSpecific September 10 Rule Updatesdiscussion. Most importantly, the new rule amends the Defense Federal Acquisition Regulation Supplement (DFARS) to begin CMMC program implementation on November 10, 2025. The rule also clarifies definitions and the scope of what is, and is not, covered under the CMMC program. The new version of a phase-in process is described. Some essential boundaries and relationships between the government, prime contractors, and subcontractors are also clarified. Finally, the rule eliminates one of the reporting requirements.
Specific September 10 Rule Updates
As a preliminary matter, theSeptember 10 ruleprovided additional clarity on certain questions presented during the public comment period. Some of the most notable changes are outlined below.
A. Definitional Updates – DFARS 204.7501
Definitional changes are reflected in DFARS 204.7501. The most impactful changes include the following:
- The definition ofcurrentwas revised to mean that a contractor's cybersecurity status remains unchanged since achieving a particular CMMC status and is fully compliant with CMMC standards (per32 CFR part 170).
- Plan of Action and Milestones(POA&M), which is a term that is widely used through the program, is added based on a definition from32 CFR part 170. This term refers to a document that identifies assessment tasks to be completed, including required resources to accomplish elements and milestones in meeting the plan.
- The termDoD unique identifierwas updated toCMMC unique identifier(UID),which refers to a ten-character alphanumeric code assigned to each contractor's CMMC assessment and recorded inSupplier Performance Risk System (SPRS)for every contractor information system involved in handling controlled data.
- CMMC statusdefinitions are introduced to help
contracting officers interpret assessment results in SPRS when
evaluating a contractor's cybersecurity posture. This is
critical, because, depending on the status of CMMC, the contractors
may or may not be eligible for awards. The program also defines the
following terms:
- Conditional CMMC status, which allows contractors pursuing CMMC Levels 2 and 3 to have temporary conditional status for up to 180 days while closing out POA&M. The final status is only granted once all outstanding POA&Ms are completed.
- Final CMMC Statusis the final level of compliance with CMMC that a contractor achieves after closing out on POA&Ms.
- Affirmation of continuous compliancemeans confirming in SPRS that each contractor system used to handle government data (FCI or CUI) continues to meet the cybersecurity requirements throughout the life of the contract (per32 CFR part 170). This procedure is completed annually for each one of the UIDs within the organization.
- Applicability:FCI and CUI only. The September 10 final rule also clarified that CMMC requirements only apply to CUI and FCI, removing the broader and undefined termdatafrom the original draft to narrow the applicability scope.
B.Rules of the Road for Contracting Officers – No CMMC = No Award (DFARS 204.7503 & 204.7502)
The rule updates DFARS 204.7503 by requiring contracting officers to include CMMC level specified by the program office and to verify contractor status on SPRS. DFARS 204.7503 forbids contract awards to offerors who lack a necessary CMMC status. Contractors are also required to provide CMMC UID for each of the contractor information systems used in the performance of the contract. These procedures are triggered when CMMC clause DFARS 252.204-7021 is included in solicitations.
While this requirement may be anxiety-inducing, DFARS 204.7502 does offer a 180-day grace period for Levels 2 and 3 compliance, allowing contractors to secure an award with a conditional CMMC status and finalize their certification after successfully closing out valid POA&Ms. Unfortunately, for Level 1, a final CMMC level status is necessary for an award. Contractors should be aware of this flexibility for Level 2 & 3 compliance, but we still recommend prompt action for contractors who believe they would be subject to CMMC, regardless of the necessary level.
C.Clause Prescription(DFARS 204.7504)
- Timelines:The September 10 final rule provides guidance on the
application CMMC clause at DFARS 204.7504 to contracts in the
coming years. While the rule does not immediately make all of the
CMMC requirements mandatory, it does provide a phased
implementation schedule with key dates, with each phase introducing
progressively more stringent requirements. The new rule establishes
a three-year timeline to fully implement CMMC program.
- In the first phase, starting on November 10, 2025, only select contracts will include CMMC requirements as determined by a program official. Thus, any new solicitations may include CMMC requirements for any CMMC level. Current and existing contracts with DoD are not subject to this initial rollout phase.
- After three years from the rule's effective date, the clause will apply to all contracts involving CUI or FCI, and contracting officers will be required to check SPRS contractor status and withhold award of any contract, task order, or delivery order from offerors that do not have a current or otherwise eligible CMMC status.
One area that remains unclear is how the four-phase approach described in32 CFR 170.3dovetails with implementation guidance in the September 10 final rule. We expect that DoD will adopt the above-mentioned new discretionary model for the next three years, but questions remain in this area. Notably, the final rule states that it will be up to the program managers to decide whether to apply CMMC requirements for the first three years. After that,the CMMC requirements must be includedif program managers determinethat the contractor information systemwill process, store, or use CUI or FCI.
While it is unclear whether the new rule would follow the original CMMC phase-in plan, contractors subject to Level 1 and 2 Self-Assessments should be proactively trying to fulfill compliance requirements. Regardless of an implementation approach, if the CMMC requirementis included, contractors subject to CMMC Levels 1 and 2 (Self) cannot receive an award without a final CMMC status and cannot obtain a conditionalstatus award. Levels 1 and 2 (Self) are also more likely to be included in new contracts and solicitations, because they are less resource-intensive, making them a logical starting point for implementation.
- Contracting Officer Guidance:One otherchange from the September
10 final rule is an update to the contract clause DFARS 204.7504to
add a fill-in field for the contracting officer to identify the
required CMMC level.This level will beidentifiedby the agencyin the
solicitation documents. The solicitation provision and contract
clause were updated as well to include the CMMC level required
bysolicitationand include the following four levels:
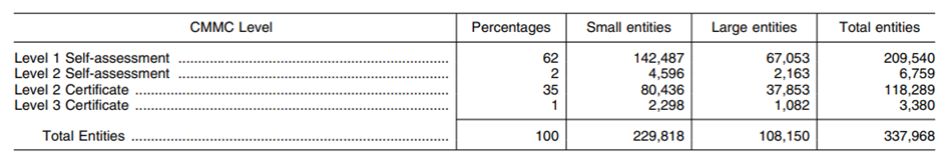
- CMMC Level 1 (Self)– The organization seeking assessment evaluates its own information system to obtain CMMC Level 1 status. The assessment focuses on the15requirements found in FAR 52.204-21. POA&M is not permitted for this level. DoD expects that, starting in year 4 of CMMC implementation, approximately 62% of awards will require a Level 1 self-assessment.
- CMMC Level 2 (Self)– The organization seeking assessment evaluates its own information system to obtain CMMC Level 2 status. This assessment includes110cybersecurity requirements from the NIST SP 800-171 standard, which are referenced in the DFARS 252.204-7012. DoD expects that, starting on year 4 of CMMC implementation, approximately 2% of awards will require a Level 2 self-assessment.
- CMMC Level 2 (C3PAO)– A contracting officer required assessment of an organization byThird Party Assessor Organization (C3PAO) to obtain CMMC Level 2 Status. This assessment includes110cybersecurity requirements from the NIST SP 800-171 standard, which are referenced in DFARS 252.204-7012. DoD expects that, starting in year 4 of CMMC implementation, approximately 35% of awards will require a Level 3 C3PAO assessment.
- CMMC Level 3 (DIBCAC)– Defense Contract Management (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) performs an evaluation for the organization seeking assessment to achieve Level 3 CMMC Status. This assessment includes110cybersecurity requirements from the NIST SP 800-171 standard, which are referenced in the DFARS 252.204-7012 regulation, and24selected NIST SP 800-172 controls. DoD expects that, starting in year 4 of CMMC implementation, approximately 1% of awards will require a Level 3 certification.
D.Reporting Requirements Updates
The program no longer requires reporting lapses in information security or changes in compliance with 32 CFR part 170 to the contracting officer, as originally contemplated by the proposed rule. The program made an adjustment due to a large number of public comments pointing out that this reporting requirement is duplicative of the DFARS 252.204-7012 requirement. The change explains that the existing DFARS requirement for notification of information security incidents and annual affirmation of continuous compliance is sufficient to protect DoD information. Keep in mind that while the CMMC program eliminated this requirement, it is still mandatory per DFARS 252.204-7012, and continuous compliance with this clause is expected.
E.Subcontractor CMMC Requirements – Primes on the Hook
The September 10 final rule also provides guidance on the prime and subcontractor relationship and flow down requirements.
- First, the rule clarifies that subcontractors that use prime contractor information systems that handle CUI and FCI are not subject to CMMC clause flow down requirements.
- Second, CMMC requirements will only be flowed down to subcontractors when they are expected to handle CUI or FCI information as a part of their work. The final rule also requires subcontractors to submit affirmation of continuous compliance and self-assessment results in SPRS.
- Finally, subcontractor compliance with CMMC requirements is now explicitly the responsibility of prime contractors. According to the final rule, prime contractors must ensure that their subcontractors are compliant with and flow down program requirements, since there is no privity of contractbetween the government and subcontractors. While there is no universal system for prime contractors to check compliance with the CMMC assessment requirements, the rule provides flexibility, allowing subcontractors to share screenshots of assessment results with prime contractors.
What Do Contractors Need to Do?
A.Get Ready Now!
While not all of the CMMC requirements are mandatory yet, failing to begin the CMMC process now, especially for Levels 2 and 3, may be the difference between securing a multimillion-dollar award and not. Even Level 1 contractors must move quickly to ensure compliance with requirements. In cases where contractors do not have Level 1 requirements completed and the contracting official determines a need for the assessment, the contractor would simply not be able to receive a contract award, because the POA&Ms 180 day grace period does not apply to them.
In addition, do not be lulled into complacency by the possibility of achieving Level 2 compliance through a self-assessment. The statistics published in the September 10 final rule show that most contractors (35% total compared to 2% for self-assessment) that need Level 2 CMMC will be required to have an assessment by 3PAOs, a process that can easily take 12 months or more. And whether a 3PAO assessment will be required is something that will be determined by agency contracting officers on a solicitation-by-solicitation basis, making it difficult to predict when such a third-party assessment will be required. The bottom line is that if on November 10 you are competing for a federal award needing CMMC Level 2 certification and you have not begun the process, you might find yourself in trouble.
If your organization has yet to begin taking steps to comply with the requirements of the CMMC program, now is a great time to start. Coordination with your key information technology personnel to review your organization's compliance with the NIST standards is a good place to start in order to develop an action plan on how to achieve the required security controls. Thinking about what systems are used as a part of your contracting process is crucial, because each contractor information system handling CUI and FCI would require a separate UID.
Moreover, subcontracting compliance monitoring should be an important piece of the puzzle and overall CMMC compliance process. Since the CMMC program places responsibility on prime contractors to ensure subcontractor compliance with program requirements, primes must carefully evaluate their partners' ability to comply and establish internal systems to streamline verification. Developing strong trusting relationships is absolutely crucial for the process, since prime contractors do not have access to subcontractors' SPRS scores and must rely on subcontractors to provide accurate information.
Additionally, contractors must consider how to manage CMMC compliance within their organization. Each organization needs to have anaffirming official, an official within the organization who must complete annual affirmations of continuous compliance. Overall, contractors must think about how to satisfy all CMMC requirements and come up with an internal process for efficiently delivering information to the right sources within stringent DoD timelines. The clock has begun ticking on these potentially hefty requirements.
B. False Claims Act Liability
Finally, it is important to keep in mind the oversight and enforcement mechanisms lurking in the background of CMMC compliance. In tandem with the development of the CMMC program, DoD has been making a strong push to protect federal information. Since the launch of the DOJ-Cyber Fraud initiative in 2021, numerous cases involving DoD data security clauses have been brought for misrepresenting compliance with the requirements. To put things into perspective, this year the DOJ achieved a settlement for falsely misrepresenting compliance with NIST SP 800-171, which is the same list of requirements set in the CMMC. The enhanced requirements for compliance under CMMC could have a significant impact on DoJ's case count due to the annual affirmation in SPRS and requirements to update any changes in the compliance status, potentially exposing a broader range of contractors to FCA liability.
CMMC is and has been a major undertaking, and with the publication of the September 10 final rule, the burden now shifts to the federal contractor population. It is crucial to get it right the first time to ensure continued involvement in the federal contracting world. But there is no need to go it alone. Cozen O'Connor's Government Contracts team can help.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


