- with readers working within the Metals & Mining industries
- within Media, Telecoms, IT and Entertainment topic(s)
This decision relates to an European patent application for a method for adjusting an aggressiveness level to use in behavior based heuristics malware detection. Here are the practical takeaways from the decision T 2386/16 (MALWARE DETECTION USING FILE PREVALENCE TO INFORM AGRESSIVENESS OF ... of 27.4.2021 of Technical Board of Appeal 3.5.01:
Key takeaways
The invention
The invention concerns behavior based heuristics malware detection. Instead of using a static approach, the invention suggests to have varying dynamic measures to be applied to a file dependent on how likely the file is considered to be infected. The more likely a file is to contain malware, the stronger will be the measures. The "aggressiveness level" of the malware detection is dynamically adjusted based on the "prevalence rate" of a file such that lower prevalence files are treated more aggressively than higher prevalence files.
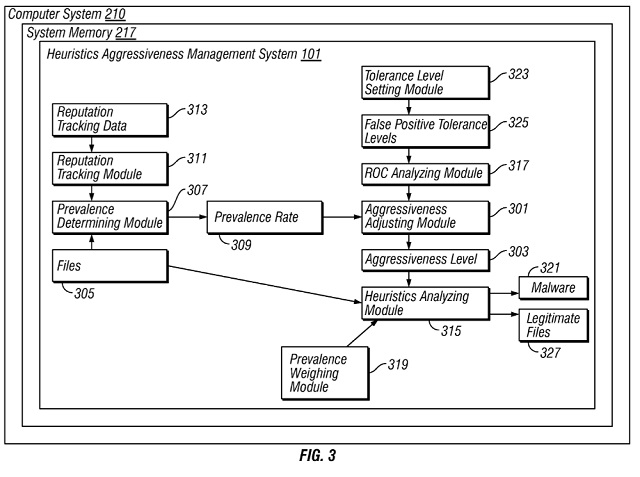
Fig. 3 of EP2494446
Here is how the invention was defined in claim 1:
Claim 1 (main request)
A computer implemented method for adjusting an aggressiveness level (303) to use in behavior based heuristics malware detection, based on target file prevalence rates, the method comprising the steps of:
determining, by a computer, a prevalence rate (309) of a file (305) subject to behavior based heuristics analysis to determine whether the file (305) comprises malware, wherein widely distributed files (305) have the highest prevalence rate (309), and singleton files (305), which have not seen by the computer before, have the lowest prevalence rate (309);
adjusting, by a computer (210), the aggressiveness level (303) with which to conduct the behavior based heuristics analysis on the file (305), responsive to the determined prevalence rate (309) of the file (305), comprising setting the aggressiveness level (303) to a higher level for files (305) having a lower prevalence rate (309), and to a lower level for files (305) having a higher prevalence rate (309), wherein the highest aggressiveness level (303) is set for singleton files (305);
applying, by a computer (210), behavior based heuristics analysis to the file (305), using the aggressiveness level (303) adjusted according to the prevalence rate (309) of the file (305); and
determining, by a computer (210), whether the file (305) comprises malware (321), based on the applied behavior based heuristics analysis.
Is it patentable?
D7 (US 2007/0079379 A1) was discussed as the closest prior art for claim 1.
Since the expressions "prevalence rate" and "aggressiveness level" do not have a specific technical meaning in the art and the claim does not provide its own definition, the Board has a broader interpretation of these expressions than argued by the appellant. Regarding the expression "prevalence rate":
During oral proceedings the appellant further argued that in contrast to the claimed invention D7 did not disclose an adjustment of the analysis of the file based on the prevalence rate. The Board does not agree, because D7 discloses the use of stricter scanning rules at later times of the outbreak (see last paragraph of point 2 above). D7 explicitly discloses a re-scanning step of messages with an adapted set of rules for a virus outbreak that are initially broad and of which the scope is later narrowed down (see paragraph 248 of D7). As a result, messages that matched the earlier rule set may not match the revised rules, and become known false positives. The approach in D7 attempts to release known false positives automatically in response to a rule update, without intervention. This corresponds to the present invention as described in paragraphs 25 and 26 of the description, which is covered by claim 1.
Regarding the expression "aggressiveness level":
D7 suggests varying measures for isolating files or stopping the execution of files such that they can be further analysed. The Board regards this as an aggressiveness level to be used in a behaviour based heuristics malware detection.
D7 discloses that when the virus score value is greater than or equal to a specified threshold, the message is stored in a quarantine queue without immediately delivering it to the recipient account (see [0045]). In addition, a variable quarantine time is suggested (see [0229]). A minimum quarantine delay is applied to messages that are less likely to contain a virus. Thus, the quarantine time is coupled to the probability that a message contains a virus. The Board considers this to be at least equivalent to the aggressiveness level in the context of claim 1.
At the end, the discussion was focused on the distinguishing feature "singleton files":
Claim 1 further specifies "singleton files", which have not been seen by the computer before and have the lowest prevalence rate. Those singleton files are treated with the highest aggressiveness level.
Such "singleton files" are not explicitly disclosed in D7. The Board is however not convinced that treating files having the lowest prevalence rate (singleton files) more aggressively involves an inventive step. In the Board's view, this does not necessarily improve the virus detection over D7, which already suggests that the aggressiveness level is coupled to the probability that a message contains a virus.
Defining singleton files as the files most likely to contain malware is considered to be a mere heuristic, which does not reliably provide a technical effect. Also D7 uses heuristics. Depending on probabilities and subjective experiences, the skilled person would consider many heuristic approaches to define such files within the general idea of applying the highest aggressiveness for files most likely to contain malware.
In view of this the Board considers the feature of treating singleton files the most aggressively to be an obvious choice for the skilled person.
Therefore, claim 1 was considered not to involve an inventive step. Since none of the auxiliary requests could overcome this objection, the appeal is dismissed.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.
[View Source]

