- within Technology topic(s)
- in United States
- with readers working within the Accounting & Consultancy, Media & Information and Retail & Leisure industries
- within Technology, Privacy, Government and Public Sector topic(s)
————Takeaways————
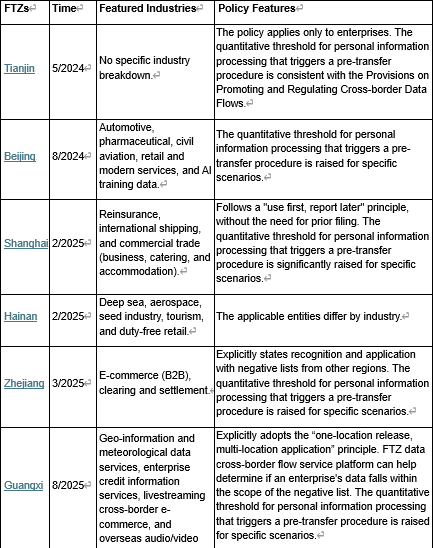
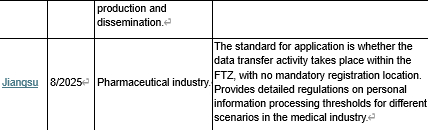
- As of August, a total of seven Chinese provinces have established a cross-border data transfer management system for their free trade zones, following the release of negative lists for data export management by both Jiangsu and Guangxi. These data catalogs cover a wide range of cutting-edge industries, including automotive, healthcare, and artificial intelligence, as well as local specialty sectors like e-commerce, deep-sea, and the seed industry.
- The Supreme People's Court has released its first set of guiding cases on judicial protection of data rights. By clarifying the scope of rights for both data processors and data subjects, these cases provide a clear framework for legal compliance, thereby protecting the stable development of data-driven businesses. For example, the Personal Information Protection Law lists the necessity of processing personal information for the conclusion or performance of a contract as one of the statutory exceptions where no consent from the data subject is required. Through these cases, the Supreme People's Court has clarified that collecting personal information for automated personalized content recommendation via an app is not considered "necessary" in this context, while collecting user credit information for a "buy now, pay later" service can be.
- On September 1, the Measures for the Labeling of Artificial Intelligence Generated Synthetic Content officially took effect. This new regulation requires AI content generation service providers and online platforms to take appropriate measures to label AIGC content.
————Regulative Highlights————
China's FTZ Data Transfer Framework Expands as Jiangsu and Guangxi Release Negative Lists
The negative lists for data cross-border transfer management in Free Trade Zones (FTZs) are an important supplement to China's existing pre-transfer compliance system, which primarily relies on security assessments, personal information protection certifications, and standard contracts for cross-border personal information transfers. The 2024 Provisions on Promoting and Regulating Cross-border Data Flows empower FTZs to create their own negative data lists within the national data classification and grading framework. Data not on the list can be freely transferred overseas. With the release of the 2025 China (Guangxi) Free Trade Zone Data Cross-border Transfer Management List (Negative List) on August 4, followed by the Trial Measures for the Management of Data Cross-border Transfer Negative List in the China (Jiangsu) Free Trade Zone and the 2025 China (Jiangsu) Free Trade Zone Data Cross-border Transfer Management List (Negative List) on August 13, a total of seven negative lists are now in effect across China, including those from Beijing, Tianjin, Shanghai, Zhejiang, and Hainan.
This collection of six guiding cases provides clear guidance on key issues such as data ownership determination, the utilization of data products, personal information protection, and the delivery of online platform accounts. The goal is to standardize judicial decisions for similar cases. The cases are as follows:
- A tech company v. a cultural media company on a case of unfair competition: The court ruled that a data set created from short videos, user comments, and user information is considered a form of business interest that receives protection under the Anti-Unfair Competition Law. The defendant was ordered to pay the short-video platform RMB 5 million in damages for illegally scraping and repurposing 50,392 videos.
- An internet information technology company v. an information technology company on a case of unfair competition: This case established that when a user consents, it's considered lawful for a platform to obtain, store, and use that user's data from a linked platform. That linked platform cannot claim its competitive interests were harmed because of this practice.
- A steel company v. an e-commerce company on a case of tort liability: The court determined that collecting product price information from different companies within an industry (via public accounts, WeChat groups, phone calls, or sales contracts) to compile a price index is lawful data processing and does not violate the rights of the companies whose data was used.
- Luo v. a tech company on a case of privacy and personal information protection: The court found that an app's collection of user profiling information for automated decision-making and content recommendation is not considered "necessary for the conclusion or performance of a contract to which the individual is a party." Therefore, forcing users to agree to this collection infringes on their personal information rights.
- Huang v. a credit management company on a case of personal information protection: In contrast, the court ruled that a "buy now, pay later" feature, which requires activating a credit service, is considered "necessary for the conclusion or performance of a contract to which the individual is a party." Consequently, the collection of personal information related to a user's credit or risk status by the credit service provider does not violate personal information rights.
A cultural media company v. You on a case of enforcement: In judicial enforcement procedure, when enforcing the transfer of an online platform account and password, the real-name authentication information must also be legally changed. If the defendant refuses to comply, the plaintiff can apply to the enforcement court for a notice of assistance to compel the online platform to make the necessary changes.
————Important Data————
On August 1, the Data Security Institute of the China Industrial Control Systems Cyber Emergency Response Team released the full text of three industry standards: Guidelines for Identifying Important Industrial Data, Requirements for Industrial Enterprise Data Security Protection, and Specifications for Industrial Data Security Risk Assessment. These three standards were already officially implemented on April 1, February 1, and August 1, 2025, respectively.
————Artificial Intelligence————
On September 1, 2025, the Measures for the Labeling of Artificial Intelligence Generated Synthetic Content officially came into effect. This regulation mandates that all AI-generated service providers and online platforms must take appropriate measures to label AI generated content (AIGC). To ensure the smooth implementation of these measures, the Cybersecurity Standardization Technical Committee released six practical guidelines on August 28. These guidelines specify methods for implicitly labeling AI-generated synthetic text, images, audio, and video content within file metadata, as well as a framework for detecting such content.
————Standard Management————
On August 4, 2025, the State Administration for Market Regulation and the Standardization Administration of China released the No.19 National Standard Announcement of 2025, which officially published seven national cybersecurity standards: Cybersecurity Technology - Public Key Infrastructure Certificate Management Protocol, Public Key Infrastructure - Minimum Interoperability Specification for PKI Components, Public Key Infrastructure - Timestamping Protocol, Information Security Risk Management Guidelines, Cloud Computing Service Security Capability Assessment Methods, Cybersecurity Operations and Maintenance Implementation Guidelines, and the Security Framework for AI Computing Platforms.
On August 15, the Cybersecurity Standardization Technical Committee announced the draft of two new national standard systems: the National Standard System for Data Security (2025 Edition) and the National Standard System for Personal Information Protection (2025 Edition). On the foundation of data classification and grading protection, the Data Security Standard System aims to establish a data-centered all lifecycle protection framework, covering the collection, storage, use, processing, transmission, provision, public disclosure, and deletion of data. The Personal Information Protection System will build on this system, centering on protecting personal information rights and interests by covering related subjects like organizations, products, services, systems, technologies, and management. This system will also encompass all personal information processing activities. The deadline for public feedback was August 29.
On August 27, the Committee announced its intention to formulate the national standard Cybersecurity Technology - Open Third-Party Resource Authorization Protocol. This standard is intended for developing identity authentication and authorization services across different security domains on the internet, and the deadline for public feedback is October 26.
————Internet Compliance————
On August 4, 2025, the Cyber Security Association of China released a list of five apps that have completed optimization and improvement for personal information collection and usage. The association guided the operators of these five apps—from mail and express delivery, used car trading, and travel services—to focus on resolving issues like collecting excessive personal information, over-invoking sensitive permissions, and making permissions settings and account cancellation inconvenient.
On August 21, the Shanghai Communications Administration issued a notice regarding the delisting of 58 apps for infringing on user rights. Of the 162 apps publicized in July 2025 for user rights infringements, 58 failed to implement the required rectifications by the deadline. As a result, the Shanghai Communications Administration ordered the delisting of these 58 apps from all major app stores nationwide.
————Data System————
On August 14, the State Council Information Office held a press conference on "High-Quality Completion of the 14th Five-Year Plan." During the event, Liu Liehong, Commissioner of the National Data Administration, noted that China introduced 21 policies last year for the development and utilization of public data resources. This year, the country plans to roll out more than 10 additional policies to improve its foundational data systems, including those related to data property rights.
On August 15, the Lingang Special Area of the China (Shanghai) Pilot Free Trade Zone released its plan for building an International Data Processing Hub. The plan emphasizes strengthening data cooperation with regions like Hong Kong SAR, Europe, and Southeast Asia. It also highlights the requirements to align with international rules such as the Digital Economy Partnership Agreement (DEPA) and the Comprehensive and Progressive Agreement for Trans-Pacific Partnership (CPTPP). The plan aims to improve an innovative management system that includes pre-event access, in-process self-management, and post-event exemption from liability, along with a robust data security management mechanism.
————Worldwide News————
On August 6, South Korea released the Guidelines for Personal Data Processing in the Development and Application of Generative AI. The guidelines divide the complete lifecycle of generative AI development and use into four stages: goal setting, strategy formulation, learning and development, and application management. They systematically propose minimum security measures for each stage. Additionally, for issues with high practical uncertainty, such as whether user data can be used to train AI, the guidelines offer specific solutions based on policies and previous cases from the Personal Information Protection Commission.
On August 8, Australian Information Commissioner (AIC) has filed civil penalty proceedings in the Federal Court against Singtel Optus Pty Limited and Optus Systems Pty Limited (together, Optus), Australia's second-largest telecommunications provider. According to the AIC's allegations, between October 17, 2019, and September 20, 2022, Optus failed to take reasonable steps to protect the personal information of approximately 9.5 million of its users. This failure led to a massive data breach and exposure in September 2022, with some personal information even being posted on the dark web. Under Australia's Privacy Act at the time of the incident, each data breach could have resulted in a maximum penalty of AUD 2.22 million.
On August 12, an Australian Federal Court issued a landmark ruling, finding that Apple and Google engaged in anti-competitive behavior by restricting app distribution channels and mandating the use of their own payment systems, which effectively weakened market competition. This decision marks a partial victory for Epic Games, the developer of Fortnite, in its years-long global antitrust lawsuit against the tech giants. Epic Games stated, "this is a victory for Australian developers and players," and that Fortnite and Epic Games Store would soon launch in the iOS platform in Australia. Both Apple and Google said they would evaluate their next steps after receiving the full judgment. The case remains subject to appeal.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


