- within Corporate/Commercial Law topic(s)
- in European Union
- with readers working within the Retail & Leisure industries
- within Corporate/Commercial Law, Transport and Employment and HR topic(s)
I. Introduction
In recent years, following a period of explosive growth, China's internet industry has gradually entered a stage of stock competition. Driven by intense internal performance metrics and the lure of substantial financial gain, cases of employees exploiting their positions, system vulnerabilities, or management deficiencies to commit crimes to seek illicit profits have become increasingly common. Such incidents not only inflict significant economic losses on companies but also severely erode corporate culture and business credibility. For internet enterprises, establishing a compliance framework capable of effectively identifying, preventing, and addressing internal criminal risks has shifted from being an "option" to a "necessity."
Against this backdrop, this article aims to analyze the most common criminal charges and emerging trends in cases involving internet companies and to provide professional suggestions for corporate criminal risk mitigation. It is intended as a reference for readers, particularly practitioners within the internet industry.
II. Current Status and Trends of Criminal Cases Involving Internet Companies
A. Multiple Internet Companies Issue "Anti-Corruption Announcements"
To strengthen the internal governance of corruption and fraud, several leading internet companies have established dedicated oversight bodies, such as Anti-Corruption Investigation Departments, Corporate Discipline and Ethics Committees, or Internal Control and Compliance Divisions. Upon identifying employee misconduct through these channels and reporting mechanisms, companies typically publicize the details through "Anti-Corruption Announcements" to demonstrate their zero-tolerance stance.
In January 2025, a prominent internet company publicly disclosed its anti-corruption governance results for 2024. The report indicated that the company had investigated over 100 integrity policy violations during the reporting period, leading to the dismissal of more than 100 employees involved. Of these, over 20 individuals suspected of criminal offenses were referred to judicial authorities for investigation. The report also detailed the handling of several serious cases involving commercial bribery and misappropriation of company funds.
In June 2025, a leading e-commerce group's 2024 ESG report disclosed that the company had completed internal investigations into 221 corruption cases during the reporting cycle, comprising 191 cases of commercial bribery and 30 cases of misappropriation; it also addressed 12 conflict-of-interest incidents. Furthermore, 20 employee corruption cases (including those referred in previous years) that the company had referred to judicial authorities were concluded within this period.
In September 2025, a renowned internet technology company, through its Ethics and Discipline Committee, announced the outcomes of employee disciplinary actions for the second quarter of that year. The announcement stated that 100 employees had been dismissed for serious violations of company policies. Among them, 18 were publicly named due to suspected criminal activity or intentional harm to company interests; an additional eight individuals, suspected of criminal offenses, had been transferred by the company to judicial authorities.
These announcements from leading internet companies indicate that the domestic internet industry faces significant risks of internal fraud and criminal conduct, with corruption cases occurring frequently. Some implicated personnel have been transferred to judicial authorities on suspicion of criminal offenses. Simultaneously, "Anti-Corruption Announcements" have become a crucial method for companies to respond to public concerns and showcase their commitment to compliance governance.
B. Distribution of Corruption Case Charges Involving Internet Companies from 2020 to 2024: – A Study Based on Judicial Data from Haidian District Court
In May 2025, the Beijing Haidian District People's Court, in conjunction with the Internet Society of China, released the White Paper on Corruption Crimes Committed by Internal Personnel of Internet Companies1, disclosing trial data and trend analysis for related cases within its jurisdiction over the previous five years.
The White Paper data reveals that the internet industry has become a high-incidence area and key risk zone for internal corruption crimes. From 2020 to 2024, Haidian District Court concluded 350 cases of corruption crimes involving non-state functionaries, of which 127 cases involved internal personnel of internet companies, accounting for 36.28% of the total. The total amount involved reached approximately RMB 305 million.
In terms of specific charges, corrupt practices within internet companies primarily manifested in the following forms:
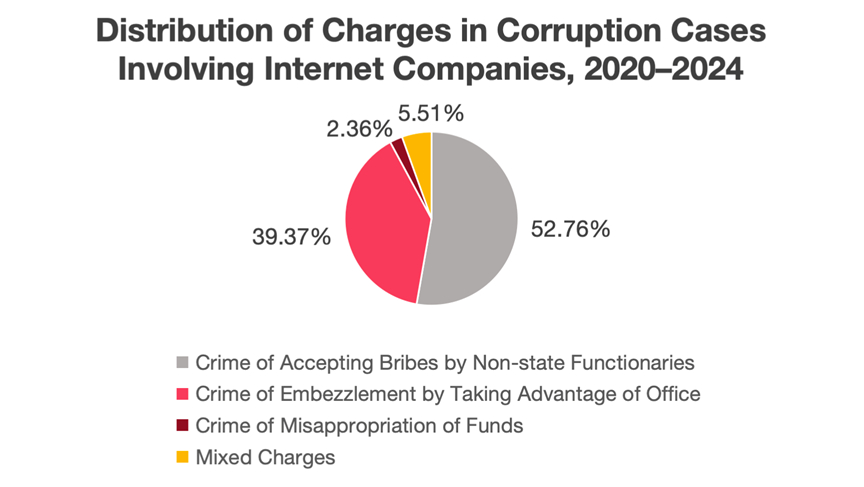
Judicial data from the Haidian District Court over the past five years clearly indicates that internal corruption crimes in internet companies not only represent a high proportion of cases and involve substantial sums but also exhibit distinct characteristics, being predominantly bribery by non-state functionaries and misappropriation. These figures highlight the prominent contradiction between new forms of rent-seeking power under the platform economy model and lagging internal governance.
C. Emerging Crime Pattern: "Platform Power Rent-Seeking"
With the deepening development of the "Internet Plus" model, corrupt practices within internet companies have acquired new characteristics marked by deep integration with technology, rendering criminal methods more diverse and concealed. Beyond traditional forms of bribery and misappropriation, the exploitation of unique internet platform resources for "power rent-seeking" has become a breeding ground for new types of crime.
In the realm of bribery, aside from traditional practices like accepting kickbacks, a growing number of cases involve the abuse of platform operational privileges to secure concealed benefits for others. This includes providing improper assistance in areas such as traffic allocation, search ranking, account permission management, and content recommendation, in return for illicit gains. In the "Case of Guo for Accepting Bribes by Non-state Functionaries"2 , Guo, an e-commerce live-stream operations employee at an internet company, exploited his duties in live-stream management and account maintenance. Under the pretext of loans, home purchases, or car acquisitions, he solicited or illegally accepted property from several e-commerce hosts under his supervision, providing them with favors such as expediting account reinstatement and prioritized "whitelisting".
In cases of misappropriation, beyond misappropriating company assets through traditional methods like fabricating expenses or siphoning funds, perpetrators now also employ novel tactics such as creating fictitious transactions, tampering with data, and fraudulently obtaining subsidies or coupons. These methods directly exploit platform rules and technical vulnerabilities for illegal profit. Owing to their technical sophistication and stealth, such schemes often evade detection by conventional auditing methods. For instance, in the "Case of Li for Duty-Related Embezzlement "3 , the defendant Li, during his tenure in the e-commerce department of an internet social platform company, utilized his position to facilitate false transactions on the company's platform through a third-party company controlled by Zhang, thereby defrauding the victim company of subsidies totaling over RMB 1.5 million.
III. Analysis of Commonly Occurring Offenses
As previously mentioned, corruption risks within internet companies exhibit trends of high frequency and concealment, primarily involving the crimes of Accepting Bribes by Non-state Functionaries, Duty-Related Embezzlement, and Misappropriation of Funds. These criminal acts increasingly demonstrate distinct industry characteristics in judicial practice. Drawing on typical cases, this article briefly analyzes the criteria for identifying and the manifestations of common offenses in the anti-corruption domain of internet enterprises.
A. Crime of Accepting Bribes by Non-state Functionaries
According to Article 163 of the Criminal Law, the Crime of Accepting Bribes by Non-state Functionaries is defined as follows: it refers to an act where a staff member of a company, enterprise, or any other entity, by taking advantage of their duties, either 1) demands or illegally accepts money or property from another person to seek benefits for that person; or 2) in the course of economic exchanges, violates state provisions by accepting rebates or service charges in various forms and taking them for their own personal ownership, provided that the amount involved is relatively large. The core of this crime lies in the act of a non-state functionary leveraging their position for benefit exchange, infringing upon the normal management activities of the company/enterprise and the order of fair competition.
Within internet companies, this crime may manifest in various forms, such as accepting kickbacks from suppliers, demanding bribes from partners by exploiting traffic allocation authority, or seeking illegal gains through unauthorized data access or algorithm manipulation. If these acts constitute a crime, offenders shall be punished based on the amount involved and the severity of the circumstances, facing penalties ranging from criminal detention to fixed-term imprisonment to life imprisonment, along with fines.
Typical Case: In the case of "Liu et al. for Acceptance of Bribes by Non-state Functionaries"4 tried by the Shanghai Qingpu District People's Court, the defendant Liu, while serving as Senior Director of the Big Data R&D Center (later the Big Data and New Technology R&D Center) from November 2017, exploited his positional authority in recommending and selecting IT service suppliers to secure improper benefits for Company B by helping it obtain project orders. He repeatedly accepted bribes totaling over RMB 6.67 million from Luo, the actual operator of Company B, who acted in collusion with Wang and others. The court ruled that Liu had committed the crime of Accepting Bribes by Non-state Functionaries, sentencing him to four years' imprisonment and a fine of RMB 500,000.
Analysis: In this case, defendant Liu, serving as a Senior Director of the company's Big Data Center, held authority over supplier referrals and decision-making. His act of exploiting this position to secure project orders for Company B and accepting substantial benefits fulfills the constitutive elements of "illegally accepting any money or property from any other person and seeks benefits for any other person by taking advantage of duty". This conduct severely undermined the fair competition environment and management order within the IT procurement field. In internet companies, technical decision-making roles often directly control substantial procurement and collaboration resources, rendering such positions high-risk areas for the Crime of Acceptance of Bribes by Non-State Functionaries.
B. Crime of Duty-Related Embezzlement
According to Article 271 of the Criminal Law, the Crime of Duty-Related Embezzlement is defined as follows: it refers to an act where an employee of any company, enterprise or any other organization unlawfully takes possession of the money or property of the organization by taking advantage of duty, provided that the amount involved is relatively large. The core of this crime lies in the perpetrator exploiting the convenient conditions afforded by their position within the organization to unlawfully appropriate property that rightfully belongs to the organization, thereby infringing upon the organization's ownership rights over such property.
Within internet companies, potential manifestations of this crime include falsifying records to embezzle company funds; exploiting access privileges to steal or resell company virtual assets or platform subsidies; or tampering with backend data to misappropriate company funds. Where such acts constitute crimes, offenders will face penalties ranging from criminal detention to fixed-term imprisonment or even life imprisonment, along with fines, based on the amount embezzled and the severity of the circumstances.
Typical Case: In the case of "Zhang for Crime of Duty-Related Embezzlement"5 concluded by the Shanghai Xuhui District People's Court, the defendant Zhang joined a Shanghai-based technology company as a Direct Sales Manager in January 2018. Between December 2019 and August 2021, he exploited his position in direct client development by falsely designating the direct client "Adam" as a channel client. Through a company in Shanghai where his girlfriend, Zuo, was employed, he thereby siphoned off over RMB 600,000 in rebates that the technology company had intended for agents. The court found Zhang guilty of Duty-Related Embezzlement and sentenced him to ten months' imprisonment, suspended for one year, and a fine of RMB 8,000.
Analysis: In this case, the defendant Zhang exploited his position as a Direct Sales Manager by creating a fictitious channel agent and fabricating transaction layers. He thereby illegally diverted sales profits, which should have accrued directly to the company, by channeling them into non-existent "channel rebates." The essence of his actions constituted the illegal appropriation of the company's property, thereby satisfying all elements of the crime of Duty-Related Embezzlement. This case exposes potential internal control weaknesses within internet companies, particularly in sales channel management, agent qualification verification, and the disbursement of incentive funds.
C. Crime of Misappropriation of Funds
According to Article 272 of the Criminal Law, the Crime of Misappropriation of Funds is defined as follows: it refers to an act where an employee of any company, enterprise or any other organization, by taking advantage of duty, misappropriates the funds of the organization for personal use or for lending to others, if the amount is relatively large and the funds are not repaid after three months, or if the amount is relatively large and the funds are used for profit-making activities or illegal activities even though the period is less than three months. The core of this crime lies in the perpetrator's unauthorized placement of organizational funds under personal control, thereby infringing upon the organization's rights to possession, use, and beneficial interest in such funds.
Within internet companies, this crime may manifest in several forms, including diverting marketing funds for personal investment or wealth management purposes; lending company advances intended for cooperative projects to third parties for their temporary liquidity needs; or making short-term personal use of platform revenue. Where such an act constitutes a crime, the punishment is determined by the amount misappropriated, the duration of the misappropriation, and the purpose for which the funds were used—ranges from fixed-term imprisonment to criminal detention.
Typical Case: In the case of "Zhao for Crime of Misappropriation of Funds"6 concluded by the Beijing Haidian District People's Court, the defendant Zhao served as an operations staff member in the BPO Business Department of a Beijing technology company commencing in May 2019. In this role, he was responsible for cash settlement and used a personal bank card to handle company operational funds. Between August and October 2022, Zhao exploited this position to embezzle over RMB 1.2 million belonging to the victim company from this bank card for personal use and failed to repay it for more than three months. The court ruled that Zhao committed the crime of Misappropriation of Funds, sentencing him to one year imprisonment, suspended for one year and six months.
Analysis: In this case, defendant Zhao exploited his position to misappropriate over RMB 1.2 million of company funds for personal use, failing to return the amount for more than three months. This conduct satisfied the key statutory elements of misappropriation of funds: "a relatively large amount" and "failure to return for over three months." A critical point is that the defendant, who was responsible for the company's cash settlement operations, used his personal bank account to hold company funds for operational convenience. This practice exposed significant flaws in the company's fund management system. The case serves as a critical warning to all enterprises: they must strictly implement the principle of separating public and private funds to prevent large company sums from being placed under unsupervised personal control.
D. Crime of Infringing upon Trade Secrets
According to Article 219 of the Criminal Law, the Crime of Infringing upon Trade Secrets is defined as follows: it refers to (1) obtaining a right holder's trade secrets by theft, bribery, fraud, coercion, electronic intrusion or other improper means; (2) disclosing, using or permitting others to use a right holder's trade secrets obtained by the means mentioned in the preceding item; or (3) violating the confidentiality obligation or the right holder's demand for keeping trade secrets, disclosing, using or permitting others to use the trade secrets he has controlled, if the circumstances are serious. The core of this crime lies in the infringement upon the right holder's exclusive rights to trade secrets through improper means, thereby damaging the market competition order.
Within internet companies, potential manifestations of this crime include copying source code, algorithm models, or key technical documents before leaving employment; illegally providing customer lists or core operational data to competitors; or disclosing sensitive business strategies or project plans in breach of confidentiality agreements. If the act constitutes a crime, the punishment ranges from fixed-term imprisonment to criminal detention and may also include the imposition of a fine.
Typical Case: In the case of "Wu et al. for Crime of Infringing upon Trade Secrets, Crime of Infringement of Copyright"7 tried by the Beijing Haidian District People's Court, the defendant Wu, while serving as a Senior Development Manager at a Zhuhai software company in 2010, violated his confidentiality agreement. In exchange for other game engines from defendant Li, Wu unlawfully transmitted the source code for the company's copyrighted online game "Sword World" to Li via QQ email. Between June and October 2011, Li arranged for the compilation of the illicitly obtained source code into the server-terminal program for the game "Qing Yuan Jian Xia". He then conspired with the defendants Sun and Song to rent overseas servers, privately set up the game infrastructure, and create and operate a website for "Qing Yuan Jian Xia". They solicited customers to register and log in to this private server game website as players or members, profiting by collecting recharge fees through in-game top-up features via third-party payment platforms. The court ruled that Wu committed the crime of Infringing upon Trade Secrets, sentencing him to two years imprisonment and a fine of RMB 200,000.
Analysis: In this case, defendant Wu, a senior manager at a software development company, knowingly breached his confidentiality obligations by disclosing core company software source code to others for personal gain. This act satisfied the constitutive element of "violating the confidentiality obligation and disclosing the trade secrets he has controlled." His actions infringed upon the right holder's technical secrets, which ultimately led to the source code being used to operate unauthorized game servers. This severely disrupted the legitimate game market's operational order and resulted in significant economic losses. The case underscores the high risk of trade secret leakage in key technical positions, such as R&D and operations, within internet companies. Consequently, beyond executing confidentiality agreements, enterprises should enhance the tiered and categorized management of digital assets like source code, improve operational log auditing, and systematically block leakage channels through a combination of technical and managerial measures.
IV. Corporate Risk Control and Compliance Response Suggestions
Given the current prevalence of internal corruption cases within internet companies, enterprises should shift from reactive investigations to proactive prevention and control, establishing a systematic compliance risk management framework integrating "policies, technology, and investigations" to effectively identify, prevent, and address internal criminal risks.
A. Strengthening the Internal Compliance Framework
Companies should formulate and continuously refine internal regulations such as the Anti-Corruption and Business Conduct Guidelines, clearly defining behavioral boundaries and accountability for violations to ensure all operations are conducted according to established rules. Concurrently, regular compliance training and awareness programs should be organized for employees at all levels. Beyond covering senior management and key positions in procurement, operations, and sales, these initiatives should extend to all frontline roles to comprehensively prevent corruption "explosions" at the grassroots level of the organization. Companies may also integrate compliance performance into their performance evaluation systems to strengthen employees' compliance awareness. Furthermore, independent and confidential reporting channels must be established, accompanied by robust whistleblower protection and incentive mechanisms to effectively encourage internal oversight and eliminate employees' concerns about reporting misconduct.
B. Enhance Technical Prevention and Control Measures
Enterprises should establish strict hierarchical permission management and access audit mechanisms. Implement the principle of least privilege and dynamic adjustments for core data, financial systems, and backend operations to ensure all actions are traceable and auditable. Simultaneously, leverage financial process automation and big data analytics to establish risk rules and anomaly detection models for transaction logs, expense claims, and supplier payments. This enables automatic identification and real-time alerts for suspicious or related-party transactions. Additionally, enhance background checks on partners and suppliers while conducting dynamic evaluations of their performance to mitigate fraud risks arising from external collaborations.
C. Optimize the Internal Investigation System
Enterprises should establish internal investigation teams comprising members from multiple departments such as compliance, legal affairs, internal audit, and information security to ensure investigations are conducted professionally, compliantly, and efficiently. During investigations, emphasis should be placed on comprehensively and systematically collecting and preserving evidence, encompassing not only electronic data but also written documents, physical evidence, and testimonial evidence. For electronic evidence, specialized tools should be used to perform complete extraction and backup, with detailed documentation of the evidence collection process and key operational information. This ensures the authenticity, integrity, and continuity of evidence, meeting the review requirements of judicial authorities. After obtaining preliminary evidence, cases should be promptly transferred to public security organs or other judicial authorities in accordance with the law, and the company should actively cooperate with subsequent investigative work. This achieves effective coordination between internal risk management and external judicial procedures.
V. Conclusion
Internal criminal risk prevention and control within internet companies constitutes a long-term and systematic management endeavor. Currently, crimes such as Accepting Bribes by Non-state Functionaries, Duty-Related Embezzlement, Misappropriation of Funds and Infringing upon Trade Secrets remain prevalent, with perpetrators continually evolving their methods to exhibit new characteristics of concealment and technological sophistication. Companies should systematically build compliance frameworks across multiple dimensions—including institutional development, technological safeguards, and investigative response—to embed risk prevention within business processes. This enables effective coordination among preemptive prevention, real-time control, and post-incident resolution. Only by establishing routine compliance management mechanisms can enterprises effectively mitigate criminal risks within complex and dynamic commercial and legal environments, thereby ensuring healthy and stable development.
Footnotes
1 See https://mp.weixin.qq.com/s/5xF9VnzTrUGCP2z30OI_IA?scene=25&sessionid=#wechat_redirect
2 See https://mp.weixin.qq.com/s/BnilwHP48vJs7Hm6uwJ2Pg
3 See https://mp.weixin.qq.com/s/5xF9VnzTrUGCP2z30OI_IA?scene=25&sessionid=#wechat_redirect
4 See Criminal Judgment No. 820, First Instance, (2022) of the Shanghai Qingpu District People's Court.
5 See Criminal Judgment No. 857, First Instance, (2023) of the Shanghai Xuhui District People's Court.
6 See https://mp.weixin.qq.com/s/W1LEAvuPXbCBnk_NAVn_nQ
7 See Criminal Judgment No. 3240, First Instance, (2012) of the Beijing Haidian District People's Court; Criminal Ruling No. 5321, Final Instance, (2012) of the Supreme People's Court.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


