- in Australia
- with readers working within the Banking & Credit industries
- within Government and Public Sector topic(s)
- in Australia
- within Government, Public Sector, Privacy and Immigration topic(s)
- with Senior Company Executives, HR and Finance and Tax Executives
- with readers working within the Banking & Credit industries
AUSTRAC has published two National Risk Assessments about the extent of money laundering and terrorism financing ("ML/TF") in Australia and how these events affect businesses in various industries. They have been published to assist reporting entities develop more effective systems and controls to address the ML/TF risks posed to their businesses and maintain a robust anti-money laundering and counter-terrorism financing ("AML/CTF") program.
How to make use of the National Risk Assessments?
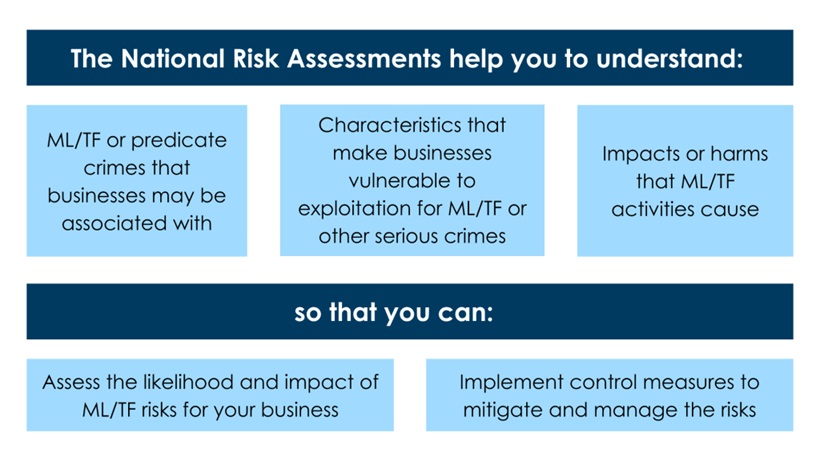
As part of their AML/CTF Program, reporting entities are required to conduct a ML/TF risk assessment to determine the measures the business implements to manage the ML/TF risks that have been identified. ML/TF risk refers to the risk that a business may be exploited for ML/TF and other serious crimes. This involves two questions:
- Likelihood – What is the chance of an event happening that may cause the business to be exploited for ML/TF and other serious crimes?
- Impact – What is the degree of damage or loss that may result if the event occurs?
To help reporting entities answer both questions, AUSTRAC's National Risk Assessments provide insights about:
- Threats – the nature and extent of ML/TF and other predicate crimes associated with businesses;
- Vulnerabilities – the characteristics of businesses that make them attractive for ML/TF purposes; and
- Consequences – the impacts or harms that ML/TF activities may cause.
Threats: What ML/TF or predicate crimes may a business be associated with?
Note: a predicate crime is any offence that generates proceeds of crime which can then be laundered. For example, the production and sale of illicit drugs is an illegal activity that creates proceeds for criminals to launder.

Methods used by criminals to exploit businesses
Generally, money laundering criminals can misuse businesses to:
- Spend illicit funds – Criminals may use illicit funds to purchase assets such as luxury goods, bullion and real estate. The funds may also be converted to cash or digital currencies (which offer more anonymity) and then spent.
- Move illicit funds – Criminals may use mule accounts to obscure the transaction chain or channels that offer rapid transfers (e.g. remittance providers) to move funds quickly (especially to overseas).
- Facilitate a criminal activity – Criminals may misuse intermediaries, such as lawyers and accountants, to set up business structures to conceal their illicit activity and execute criminal transactions.
Example
A criminal purchased stolen identity information from darknet
marketplaces. The criminal used the false identities to open bank
accounts. The criminal used a phishing website to mimic a
superannuation fund and harvested members' usernames and
passwords. The criminal then accessed members' accounts,
withdrew superannuation funds and deposited them into the
fraudulent bank accounts. The criminal then transferred some funds
to a person located overseas. The offshore individual purchased and
on-sold luxury goods, then remitted proceeds back to the criminal
in Australia through digital currencies.
Which businesses were used to facilitate this chain of
events?
- Bank processing the transaction for purchasing stolen information from the darknet
- Bank involved in the opening of the fraudulent accounts
- Superannuation fund
- Bank/remittance provider involved in international funds transfer to and from overseas
- Luxury goods retailer
- Digital currency exchange provider
In relation to terrorism financing, criminals can misuse businesses to raise funds and move funds for:
- Recruitment activities
- Radicalisation and spreading propaganda
- Payment of membership fees
- Purchase of tactical gear
- Attack planning
- Travel and people and weapons smuggling for terrorist organisations
The National Risk Assessment found that terrorism financing activities in Australia:
- are difficult to detect;
- are mostly small scale and of a low value;
- are mostly self-funded or supported by fundraising;
- take the form of funds or digital currency transfers to overseas (rather than incoming);
- are disguised as funds for legitimate humanitarian or charitable causes which are later diverted to support terrorism; and
- may also involve direct funds or digital currency transfers to violent extremist groups or actors.
Vulnerabilities: What characteristics may make a business attractive for ML/TF purposes?

ML/TF risk factors
- Dealing with cash
- Illicit cash can be easily mingled and obscured with legitimate earnings.
- Cash can be easily smuggled and exported by people and through cargo and mail channels.
- Cash can be quickly converted to digital currencies or other assets.
- Cash can be broken down into structured deposits and withdrawals to avoid reporting requirements.
- Dealing with digital currencies
- Digital currency transactions are quick, cheap, irreversible and often done pseudonymously.
- Transactions may be conducted offshore, over-the-counter (OTC) or peer-to-peer (P2P) which are not subject to regulatory oversight.
- Mixing and tumbling also increase anonymity.
- Dealing in high-value assets and goods
- Examples: luxury goods, real estate, bullion and precious metals, wealth and financial assets, investment products
- Illicit funds may be used to purchase assets under the guise of legitimate purchases or investments.
- Using delivery methods which are fast (near-instant),
affordable, easy to use, allow anonymity or lengthen the delivery
chain
- Examples: ATMs, internet/phone banking, websites, mobile applications, offsetting, providing services to third parties or agents, money mules
- Transacting overseas
- International transactions may be linked to foreign jurisdictions with weak AML/CTF regimes or regulatory oversight, as well as jurisdictions that carry a high ML/TF risk.
- Dealing with complex or opaque structures
- Criminals often use complex legal or corporate structures to conceal the true beneficial ownership and control of assets.
- Examples: shell companies, trusts, de-facto and shadow/straw directors, nominee shareholders
Case studies
- The AFP identified a money laundering organisation which operated as a criminal remittance and banking service. The organisation had a sophisticated informal value transfer system in place to make funds available overseas, exploiting digital currency trading, domestic and foreign shell companies, and multiple offshore bank accounts held with various institutions. This system allowed the organisation to effectively operate as an underground bank with global reach, managing credits and debits internally and setting its own exchange rates.
- A bullion dealer's bank account received more than $200,000 in cash over two days. Law enforcement discovered that the person making the deposits was incarcerated at the time of the transactions, leading them to believe that a money mule had made the deposits using the account holder's details.
- An Australian company received nearly $12 million in domestic and international transfers over the course of 3 months. The funds were obtained through investment scams and appeared to finance transfers to online trading platforms offering CFDs in digital currency, forex and shares. Some of the online trading platforms are linked to financial secrecy jurisdictions and tax havens.
Where to from here?
The National Risk Assessments provide an overview of the ML/TF risks at the national level. They are helpful to ensure reporting entities' understanding of the ML/TF faced by their businesses are in line with AUSTRAC's assessment of the ML/TF risks.
AUSTRAC also has guidance on ML/TF risks for specific sectors (see 'Further Reading' below). These will help you to better understand and evaluate the ML/TF risks specific to your individual business, so you can implement appropriate control measures to manage and mitigate those ML/TF risks.
Further Reading
- Money Laundering in Australia National Risk Assessment 2024
- Terrorism Financing in Australia National Risk Assessment 2024
- Proliferation Financing in Australia National Risk Assessment 2022
- AUSTRAC Webinars for Sector-Specific Risk Assessment 2024
- AUSTRAC Risk Assessments for Various Sectors
- AUSTRAC Guidance on ML/TF Risk Assessment
- AUSTRAC Guidance on Implementing a Risk Management Process
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

