- with readers working within the Technology industries
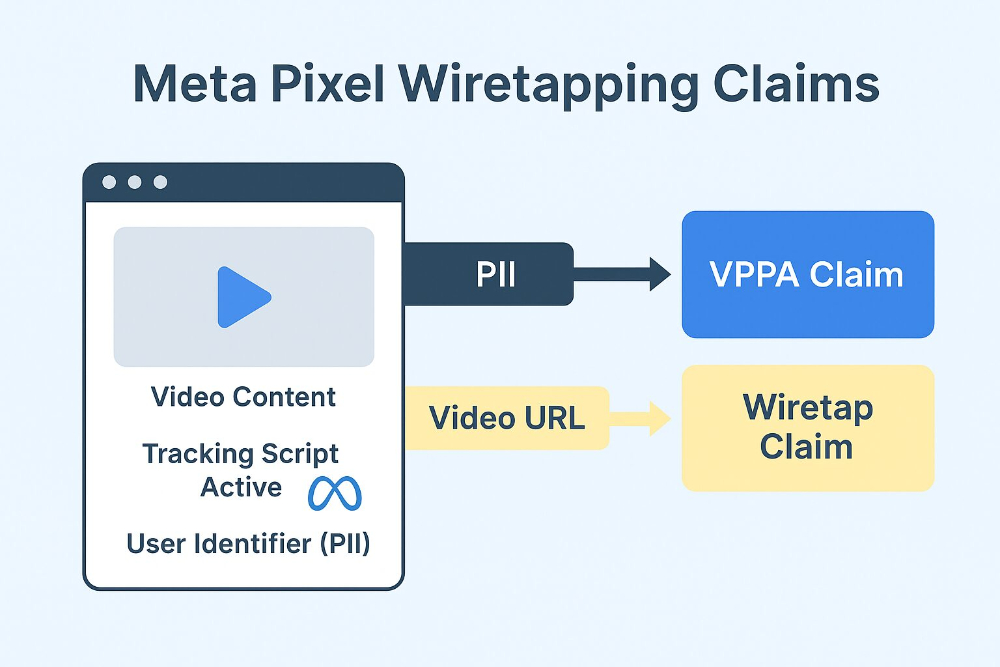
Privacy litigation has shifted from what you collect to how that data moves. Meta Pixel, session replay, and similar trackers now expose companies to parallel claims under the Video Privacy Protection Act (VPPA) and Meta Pixel wiretapping theories. Plaintiffs pair threat letters with arbitration threats, citing Terms of Use violations, and rely on identical facts: embedded video content plus third-party analytics.
Old statutes, modern surveillance theory. The VPPA, born in the VCR era, now governs autoplay clips. Wiretap laws designed for landlines are repurposed to target script-based telemetry. In both, plaintiffs argue that sharing user behavior with platforms like Meta amounts to illegal interception or disclosure.
Legal theories diverge. Tactics don't. Firms move fast, scale broadly, and anchor their claims in packet captures. Most companies never audit.
This briefing breaks down how VPPA claims and Meta Pixel wiretapping lawsuits overlap, where they diverge, and how your team can reduce legal exposure, whether you're facing a threat letter, arbitration demand, or class action complaint.
VPPA in 90 Seconds
Congress enacted the Video Privacy Protection Act in 1988 after a newspaper exposed Robert Bork's video rental history during his Supreme Court nomination. The statute prohibits any "videotape service provider" from knowingly disclosing a "consumer's" personally identifiable information tied to video-viewing behavior.
Plaintiffs now target modern websites using third-party trackers on video pages. When Meta Pixel or session replay scripts capture hashed emails, user IDs, or cookies and pair them with video playback, they claim a VPPA violation. The law's language may date to the VCR era, but courts are applying it to tracking scripts and autoplay previews.
No full video library required. Embedded clips, autoplay snippets, and marketing reels all trigger scrutiny. If a third party receives both identifiers and viewing data, plaintiffs argue that it constitutes unlawful disclosure.
Most companies assume VPPA doesn't apply. Courts increasingly disagree, stretching the statute's analog definitions to cover digital tracking infrastructures.
The Plaintiffs' Playbook
VPPA litigation runs on a mass-production model. Firms recycle canned complaints, tweaking names, URLs, and exhibits while preserving identical allegations. The goal: scale claims across as many defendants as possible with minimal upfront cost.
The filings follow typical firms and patterns seen across the privacy class-action space. Boutique firms anchor their practices around VPPA, CIPA, BIPA, and wiretap laws. Large contingency-fee shops have bolted pixel and session replay claims onto broader consumer dockets. Many deploy technical consultants or marketing vendors to scan sites, flag trackers, and trigger legal action.
Since 2022, volume has spiked. Lawsuits now cluster around Meta Pixel, data broker flows, and adtech infrastructure not because the technology is novel, but because courts are letting old statutes stretch to fit modern telemetry. Embedded video, pixel scripts, and third-party analytics drive the claims.
Wiretap/Pixel Cases: The Parallel Wave
Plaintiffs have repurposed state and federal wiretap statutes, including the California Invasion of Privacy Act (CIPA) and the Massachusetts Wiretap Act, as weapons against web tracking. They argue that tools like Meta Pixel, session replay, and chat monitoring code "intercept" digital communications, treating telemetry like an illegal wiretap.
These cases rely on the same demand-letter-first tactic used in VPPA litigation. Plaintiffs' firms often send aggressive letters outlining alleged violations and hinting at class-wide exposure. The objective is to push companies into fast settlements before any public filing. If the letter doesn't lead to payment, it's quickly followed by a lawsuit structured to survive early dismissal.
Bundled claims raise the stakes. Many complaints allege both VPPA and wiretap violations based on identical facts: that Meta Pixel disclosed video history and communication content. Bundling compounds statutory exposure and complicates defense, forcing companies to fight on multiple legal fronts at once.
How the Meta Pixel (and Similar Tools) Work
Tracking tools like Meta Pixel, Hotjar, and FullStory capture user behavior in real time. They log URLs, event metadata, and user-linked identifiers; clicks, scrolls, and session IDs. When deployed on pages with embedded video, they do more than mark visits. They record content viewed, alongside traceable identifiers.
Once captured, that data flows out. Meta Pixel routes information to Meta's analytics endpoints, where it powers ad targeting and behavioral profiling. Other trackers send similar payloads to third-party dashboards or processing platforms. Plaintiffs argue this external transmission, especially when tied to video views, violates the VPPA and wiretap statutes.
The core claim turns on linkage. Logged-in status, hashed emails, and unique IDs become bridges between anonymized behavior and identifiable individuals. Even if companies don't see the mapped identity, plaintiffs assert that disclosing it to a third party without meaningful notice or consent triggers statutory liability.
Implementation failures amplify exposure. Firing pixels on video pages, skipping consent gating, or relying on generic privacy policies creates legal entry points. Small oversights in martech setups once irrelevant now drive high-stakes litigation.
Key Similarities Between VPPA and Wiretap Pixel Claims
VPPA and wiretap pixel claims operate under different statutes, but deploy the same strategy. Plaintiffs weaponize outdated laws against modern tracking tools, framing ordinary analytics as covert surveillance. The legal playbook hinges on broad statutory language stretched to cover pixels, scripts, and digital identifiers never envisioned by the original drafters.
In both claim types, plaintiffs cast Meta Pixel and session replay tools as surreptitious interception/disclosure mechanisms. These trackers, they argue, silently capture user behavior and transmit it to outsiders, without real consent. When placed on video pages or logged-in sessions, plaintiffs portray them as hidden data conduits.
The litigation flow mirrors itself: threat letter first, aggressive settlement push second. Complaints feature vague allegations backed by technical exhibits. The aim isn't trial it's leverage. Most defendants settle before discovery because the cost of class litigation dwarfs the price of silence.
Both tactics depend on technical forensics. Plaintiffs introduce packet captures, browser audits, and expert declarations to map data flows from the user session to the third-party endpoint. These forensic narratives are designed to survive motions to dismiss and compel early resolution.
Critical Differences You Must Understand
VPPA and wiretap pixel claims often share facts, but diverge sharply in statutory mechanics. Each hinges on distinct definitions, burdens of proof, and procedural posture. Defense strategy demands precision.
VPPA claims revolve around three elements: whether the defendant qualifies as a "video tape service provider," whether the plaintiff is a "consumer," and whether the company knowingly disclosed "personally identifiable information" tied to video activity. Courts split on thresholds. Some hold that embedding a video player triggers provider status. Others require subscriptions or curated video libraries.
Wiretap claims turn on the interception of communication contents without consent. Defendants frequently invoke the party exception, arguing that vendors like Meta or FullStory act as agents, not third-party eavesdroppers. Consent laws create tactical opportunities: some states demand two-party consent; others allow one-party consent, enabling cookie banners or privacy policies to neutralize exposure.
The most decisive distinction is jurisdiction. VPPA is federal and applies uniformly. Wiretap laws vary by state, each with its own consent rules, damage multipliers, and pleading standards. This variability shapes case strategy, venue, and motion practice. It often determines whether claims survive or collapse at the pleading stage.
Defense Strategy Overview
Defending against VPPA and wiretap pixel claims requires a multi-layered approach that blends early legal challenges, technical clarification, and procedural leverage. These cases are often designed to settle quickly, but companies that choose to fight can reduce exposure or defeat claims outright with the right strategy.
9.1 Early Motion Practice
The first step is often a motion to dismiss based on statutory scope. Defendants may argue that they are not a "videotape service provider," that the plaintiff does not qualify as a "consumer," or that no personally identifiable information or video title was disclosed. These arguments target the threshold requirements of the VPPA and can lead to early dismissal if courts agree that the statute doesn't apply.
For wiretap claims, defendants frequently argue that there was no "intercept," that the vendor involved is an agent or party to the communication, that the data collected does not qualify as the "contents of communication," and that consent was obtained through a privacy policy or cookie banner. Many of these issues hinge on how the tracking tools were implemented and disclosed to users.
Where Terms of Use are properly structured, companies may also invoke arbitration clauses and class action waivers. Enforcing these provisions early can shift the case out of public court and reduce class-wide risk.
Finally, companies may raise standing and injury attacks, arguing that the plaintiff lacks Article III standing or cannot demonstrate a concrete injury. Courts have issued mixed rulings on whether statutory damages alone are enough, making this a key area for motion practice.
9.2 Technical & Factual Defenses
Many cases collapse once the technical facts come into focus. Defendants should work quickly to narrow what the Pixel collected, using logs, configuration data, and network traces. Plaintiffs often assume data was shared without knowing exactly what was left on the page.
It's also important to demonstrate consent flows, tag manager rules, and any post-incident remediation taken to limit or prevent data sharing. Evidence that the company made good-faith efforts to gate tracking scripts or limit collection can help defeat claims of knowing disclosure.
In VPPA cases, defendants may also show a lack of linkage between IDs and specific video titles a critical requirement for liability. If the data shared can't be tied to identifiable users and specific viewing behavior, the claim may not survive.
9.3 Procedural Tools
In addition to attacking the claims substantively, procedural defenses can shift the litigation landscape. Companies should move to compel individual arbitration wherever valid agreements exist and oppose class certification by pointing to individualized consent, usage patterns, or Terms of Use enforcement.
For wiretap claims, it's especially important to challenge nationwide classes under state wiretap laws. These statutes vary significantly, and courts are often reluctant to certify classes that span conflicting legal regimes.
Settlement Dynamics
For many companies, the decision to settle comes down to a cost-benefit calculation: the defense cost vs statutory damages risk. Even when liability is unclear, the financial burden of defending against a class action, especially one involving technical experts, discovery, and motion practice, can quickly outweigh the cost of resolution. Statutory damages under the VPPA or state wiretap laws may seem small on a per-user basis, but they scale rapidly in nationwide class actions.
Although typical ranges are confidential, public examples exist that show settlements in the six- to seven-figure range, depending on class size, data collected, and litigation stage. Early settlements tend to be lower, while companies that wait until after class certification or summary judgment often face higher exposure.
When settling, it's critical to focus on structuring settlement to minimize follow-on suits. This includes defining the release scope carefully to cover all potential claims and class members. Remedial steps, such as turning off pixels on video pages, updating cookie disclosures, or revising privacy policies, may also be part of the agreement. In some cases, companies must also issue notice to users, which can trigger additional scrutiny or negative press if not handled strategically.
Settling isn't always the wrong move, but it should be done with a clear view of downstream risk, including the possibility of copycat claims from other firms watching the docket.
Immediate Response Checklist for In-House Teams
Responding quickly and strategically can make the difference between early resolution and prolonged exposure. Whether you've received a threat letter or anticipate one, the following steps help legal, marketing, and IT teams align around risk mitigation and defense.
Start by preserving evidence, including code versions, tag manager configurations, and server logs that show how tracking tools were deployed. Plaintiffs often rely on technical reports and browser audits, so maintaining internal records is essential for challenging their claims.
Next, audit your site to identify where pixels or scripts fire, with special attention to video pages or authenticated user flows. Many lawsuits hinge on whether tracking occurred in these environments and whether users were identifiable at the time.
Then, map data flows to understand what identifiers leave your domain. This includes session cookies, email hashes, unique IDs, and IP addresses. Knowing what was shared and with whom helps determine if the facts support a VPPA or wiretap claim.
In parallel, review your Terms of Use and Privacy Policy for key enforcement language. Look for valid consent frameworks, arbitration provisions, and class waiver language. These documents are often the first line of defense and can shape early motion practice.
Also, coordinate communications across teams, especially legal, marketing, IT, and external vendors. Misalignment here can lead to inconsistent responses, overlooked risk, or unintentional admissions.
Finally, make a strategic call: decide whether to fight on the merits or pursue early resolution. Not every case is worth litigating, but not every demand deserves a check either. Understanding the facts, the exposure, and the leverage will guide your path forward.
Compliance/Risk Mitigation Going Forward
Regardless of whether your company has already received a threat letter, now is the time to tighten compliance practices around user tracking and third-party scripts. Plaintiffs are scanning websites at scale, looking for easy targets. Proactive changes can reduce legal risk and support your defense if claims arise.
Start by implementing a CMP or cookie consent tool with real gating for tracking tags. Consent must be meaningful; simply disclosing tracking in a privacy policy may not be enough. Gating tools ensure that pixels and session replay scripts don't fire until the user actively agrees, which can undercut claims of unauthorized interception or disclosure.
Next, turn off pixels on sensitive pages, including videos, health or financial content, and authenticated user flows. These are the areas where courts have shown the most concern. Avoid firing third-party scripts where personally identifiable information or regulated content is involved, unless you've confirmed that consent and data flows are secure.
Where possible, use server-side tagging with data minimization. This setup gives you greater control over what data leaves your environment and allows you to scrub or hash identifiers before they reach third-party platforms. It also makes it easier to demonstrate technical safeguards if litigation arises.
Maintain a data flow inventory and conduct DPIAs for adtech tools. Documenting what data is collected, where it goes, and which vendors are involved can help you spot risk before plaintiffs do and serve as critical evidence if you're challenged under VPPA or wiretap statutes.
Finally, update your Terms of Use and Privacy Policy to support defenses, including consent, arbitration, and class action waivers. These documents should align with your technical implementation and serve as enforceable legal tools, not boilerplate placeholders.
Next Steps: Assess Your Risk with Traverse Legal
Traverse Legal is a national law firm focused on tech, IP, and privacy litigation. We have deep experience responding to VPPA and Meta Pixel wiretapping claims, advising both startups and enterprise teams on how to assess exposure, defend against litigation, and harden compliance.
We offer a free triage call to help your team evaluate the facts, understand the legal theories at play, and choose the right path forward. For companies already facing a threat letter or lawsuit, our rapid audit package includes a pixel and analytics code review, paired with a custom defense memo.
Our team also supports Terms of Use enforcement, including arbitration clauses and class action waiver optimization, critical tools in early motion practice and long-term litigation strategy.
We blend legal strategy with technical fluency so your response is grounded in both the case law and the code.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

