- in Asia
- within Antitrust/Competition Law topic(s)
- with readers working within the Retail & Leisure industries
Defense contractors need to embed new cybersecurity requirements throughout their supply chain. Fast.
The Pentagon's ambitious missile-defense project makes clear that its industrial base will need to align with its revamped cybersecurity policy that, as of November 10, will underpin its contract requirements.
The department's original guidance envisaged barely 1% of contractors having to meet the most stringent level of the three-tiered process commonly known as CMMC 2.0 because of the sensitivity of the data they would handle. Enter the U.S.'s proposed Golden Dome missile-defense system, and now hundreds of competing firms must meet the top-tier clearances to win a place on the multi-faceted program.
The bulk of the U.S. defense industrial base won't need so-called Level 3 compliance, but they will be required to adopt some elements of the new rules. Golden Dome's lure only adds to the urgent need for defense companies to scrub their supply chains and ensure compliance.
AlixPartners is working with clients to embed CMMC 2.0 as a business imperative and a competitive advantage. The business case for pursuing adoption has never been stronger. The Pentagon's push for enhanced data protection also provides a test bed for the expected rollout across contracts overseen by other U.S. government departments.
"CMMC 2.0 is a program, not a project," said Erica Antos, Mercury Systems' Chief Information Security Officer, on awebinar hosted by AlixPartners.
Know your place
The imminent arrival of the CMMC 2.0 framework requires contractors working with controlled unclassified information (CUI) or federal contract information (FCI) to meet one of three levels of compliance based on the sensitivity of the data being handled.
- Level 1:Companies handling FCI include 17 requirements with annual self-assessment and affirmation.
- Level 2:Companies face two options determined by CUI contract requirements at the time of solicitation:
-
- Self-assessment 110 controls under NIST SP800-171r2 submitted every three years into SPRS with annual self-affirmation.
- C3PAO-assessed 110 controls under NIST SP800-171r2 assessed every three years and submitted to SPRS with annual self-affirmation.
- Level 3:Companies are assessed with 110 controls under NIST SP800-171r2 and 24 selected controls under NIST SP800-172, submitted to eMASS every three years with annual affirmation.
When deemed applicable by contracting officers, the new contract requirements become effective on November 10, after the 60-day response period for Level 1 and 2 self-assessments.
Phase 2 begins 12 months later, when Level 2 C3PAO certification is required, as applicable. Phase 3 begins 24 months after Phase 1 launch and includes Level 3 DIBCAC certification, as applicable. Finally, Phase 4 will start 36 months after Phase 1 for all solicitations and contracts with the appropriate CMMC 2.0 level, as applicable.
Vendors who do not meet the required CMMC 2.0 standards will not be eligible for contract awards, task orders, or delivery orders. This policy can also be applied retroactively to existing contract vehicles.
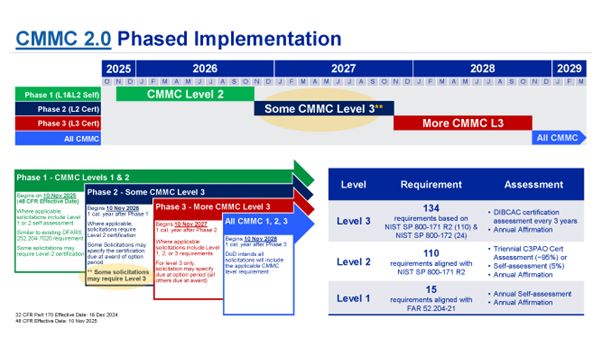
Source: Aerospace Industries Association
Scoping the supply chain
Primes are already embedding the new landscape in their contract negotiations, and hundreds of subcontractors have already met the initial requirements. That leaves many thousands more to navigate the compliance journey.
AlixPartners has the tools to support clients in embedding CMMC 2.0 as a critical element of a comprehensive cybersecurity strategy across the supply chain. This includes supporting prime contractors in verifying the compliance status of subcontractors at any given point and scoping the needs of suppliers to conform.
Many companies lack a clear picture of where each subcontractor stands regarding CMMC 2.0 requirements. They need formal assessments to assess their readiness and manage potential risks. We have developed a three-pronged approach applicable from small businesses to large enterprises:
- Planning and preparation: Defining the scope and timeline for CMMC 2.0 certification and ensuring an effective plan is in place.
- Holistic solutions: Partnering with experts, including cloud engineers for enclave design, and subject matter specialists for legal and contract support to deliver a complete end-to-end solution.
- Implementation and assessment prep: Designing and implementing security controls, building a strong evidence portfolio, and supporting rehearsal for assessments.
Subcontractors should be categorized by the sensitivity of the information they handle. Those accessing CUI require more scrutiny to ensure they meet Level 2 standards, while those using FCI must meet Level 1.
CMMC 2.0 compliance must be embedded in subcontractor agreements, with flow-down clauses to define the required level alongside timelines for achieving compliance and audit rights.
Many subcontractors will need support, and primes should explore
alternative sources to avoid non-compliance becoming a bottleneck.
A collaborative approach preserves valuable relationships while
strengthening your supply chain's overall
security.
Legal risks
AlixPartners discerns value in not simply approaching these as compliance requirements. Revised policies—if prudently followed—can lead to better business outcomes. Delays can and do lead to bad business outcomes, exemplified by some recent enforcement actions by the Department of Justice (DoJ).
Cambridge, MA-based MORSE Corp., and its 180 employees, were typical of much of the defense industrial base, a small business providing AI-enabled solutions for the Pentagon and the intelligence community.
Following a whistleblower lawsuit, the firm agreed to pay $4.6 million in March to resolve allegations that it violated the False Claims Act (FCA) by failing to comply with cybersecurity requirements in its contracts with the Army and Air Force. According to the DoJ settlement, MORSE knew for almost a year that its submitted security controls scores were too high.
The MORSE settlement came six months after Penn State agreed to pay $1.25 million to resolve an FCA case with the DoJ regarding cybersecurity compliance. The settlement resulted from allegations that Penn State failed to adequately protect CUI and FCI.
"Breaches are incredibly expensive; hundreds of millions of
dollars for medium-sized companies," Coalfire Federal CMMC
Vice President Amy Williams said on the AlixPartners webinar.
Act fast
Senior leaders across organizations need a partner to adequately fast-track the journey to CMMC compliance. Assessing where you need to be and how long the journey will take is one challenge. Creating a roadmap to turn this moment into a competitive advantage in a fast-moving industry will, in the end, separate the winners from the losers.
This means many will now need to secure approval from the limited but growing pool of third-party assessors, which remains a key bottleneck for companies to navigate. Importantly, the cost of and access to compliance certification will become a competitive tool.
Determining the scope of the assessment and preparing for C3PAO/DCMA DIBCAC audits is a crucial step in assessing the costs and benefits of compliance. Firms must determine the data impact and ensure that only the FCI and CUI data necessary for compliance is addressable. This will also determine what downstream controls are required of supply chain vendors.
Only a fraction of the defense industrial base will require the Level 3 compliance associated with Golden Dome and the most sensitive programs. But applying the principles of CMMC 2.0 provides an opportunity for the entire defense ecosystem to meet the appropriate requirements, strengthen operations, and build trust with customers by differentiating their offerings.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.



