- within Antitrust/Competition Law, Technology and Real Estate and Construction topic(s)
- with Senior Company Executives, HR and Inhouse Counsel
- with readers working within the Law Firm industries
Despite a complex legislative history, the amendments to the Security of Critical Infrastructure Act 2018 (Cth) (SOCI Act) have now been finalised (subject to the ongoing development of a number of 'Rules', which play an important role in determining the application and also determining certain operational details of the SOCI Act).
Amongst other things, the SOCI Act's extended operation imposes three key obligations on entities responsible for critical infrastructure assets. Our previous article provides an overview of the legislative history of these reforms and some of the key provisions.
These amendments have wide-reaching implications for numerous sectors, and organisations that are subject to the SOCI Act have a number of immediate steps to take to ensure that they are ready to comply with the 'positive security obligations' (described below) as compliance becomes mandatory in the coming months.
Expanded sector and asset coverage
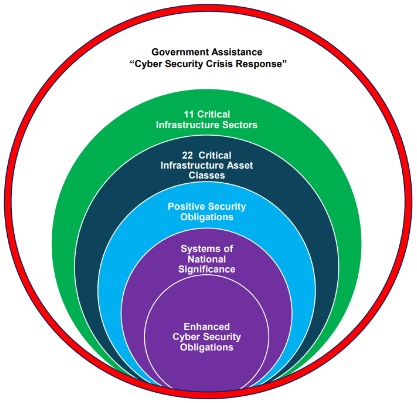
The sectors and asset classes that fall within the SOCI Act have been significantly expanded. Australia's critical infrastructure regime now encompasses 11 broadly framed sectors and 22 critical infrastructure asset classes. The sectors are:
- communications
- data storage or processing
- financial services and markets
- water and sewage
- energy
- health care and medical
- higher education and research
- food and grocery
- transport
- space technology
- defence industry
Generally, the definition of 'critical infrastructure assets' is determined by reference to specific infrastructure that is core to each sector. Most obligations apply to the 'responsible entity' which owns or operates the critical infrastructure asset. 'Direct interest holders' (those entities which hold an interest of at least 10% in a critical infrastructure asset or influence or control the asset) may also have obligations under the SOCI Act.
Source: Department of Home Affairs and the Cyber and Infrastructure
Security Centre.
Positive security obligations
Following the Security of Critical Infrastructure (Application) Rules (Application Rules) taking effect on 8 April 2022, two of the three positive security obligations now apply for certain of the newly included asset classes. Not all sectors or asset classes have had these obligations 'switched on'. Home Affairs has been in contact with entities in the asset classes about the Application Rules and their applicability to those entities, and we expect it will continue to do so with entities in the impacted sectors.
The third obligation to establish and comply with a risk management program will apply once the Risk Management Program Rules are registered. The Department of Home Affairs has released a policy document setting out the proposed Risk Management Program Rules. However, the final draft of these Rules has not been released. Once published, the draft Risk Management Program Rules will be subject to a mandatory consultation period of 28 days.
1. Report information to the Register of Critical Infrastructure Assets. Reporting entities (either a responsible entity or a direct interest holder) must provide interest, control and operational information to the Cyber and Infrastructure Security Centre. This register will not be publically available. Following the Application Rules taking effect, this obligation applies to a defined list of critical asset classes, but a six month 'grace period' means that compliance is not compulsory until 8 October 2022. Non-compliance can result in a maximum penalty of 50 penalty units (currently $11,100).
2. Mandatory cyber security incident notification requirements. The Application Rules also 'switched on' the mandatory cyber incident reporting obligations for certain critical asset classes, subject to a three month 'grace period'. From 8 July 2022, this obligation requires that:
- if an entity becomes aware of a cyber security incident that
has had, or is having,
a significant impact on the
availability of the asset, it must report this
event within 12 hours; and
- if an entity becomes aware that a cyber security incident has had, or is having, a relevant impact on the availability of the asset, it must report this event within 72 hours.
A 'significant impact' is one which has materially disrupted the availability of essential goods or services provided by the asset (or as otherwise specified in sector-specific rules, which have not yet been developed). A 'relevant impact' is any other impact on the availability, integrity, reliability or confidentiality of the asset. Non-compliance can result in a maximum penalty of 50 penalty units (currently $11,100).
3. Risk management program. The Risk Management Program Rules will 'switch on' the obligation for responsible entities to establish, maintain and comply with a risk management program that manages and mitigates prescribed risks associated with its critical infrastructure assets. It is anticipated that the Risk Management Program Rules will not apply to all asset classes (for example, if the Government forms the view that there would be regulatory overlap with other regimes applicable to the sector which already place obligations on the management of relevant risks). Once these Rules are enacted, there will be a six month grace period for compliance. A risk management program must:
- identify all hazards that present a material risk to the
availability, integrity, reliability and confidentiality of its
critical infrastructure asset;
- mitigate risks to prevent incidents;
- minimise the impact of realised incidents; and
- implement effective governance and oversight procedures relating to security.
Failing to adopt, maintain or comply with a critical infrastructure risk management program can result in a maximum penalty of 200 penalty units (currently $44,400).
Government powers
The SOCI Act also now includes additional government powers which are seen by the Australian Government as being vital for maintaining the security of Australia's critical infrastructure. In particular, from December 2021, the Government can exercise the following powers to respond to a cyber security incident that is affecting a critical infrastructure asset:
- an information gathering direction -
requiring a responsible entity to provide information in relation
to a cyber security incident;
- an action direction - where the Home
Affairs Minister can direct an entity to do, or refrain from doing,
any action deemed reasonably necessary, proportionate and
technically feasible to respond to a cyber security incident if the
entity is unwilling or unable to resolve the incident; and
- an intervention request - which provides the Australian Signals Directorate a 'last resort' power to take control of an asset where an entity is unwilling or unable to resolve a cyber security incident.
The Government may also privately declare a critical infrastructure asset (which may potentially comprise the whole or a large component of the business of an entity) to be a System of National Significance (SoNS). Once declared as forming part of a SoNS, the Government may then provide a written notice requiring the relevant responsible entity for the SoNS to comply with the following enhanced cyber security obligations:
- Develop and maintain cyber security incident response
plans.
- Undertake cyber security exercises.
- Undertake vulnerability assessments.
- Provide access to system information.
Responsible entities will be specifically notified and consulted with by the Government if these additional powers are exercised in respect of their critical infrastructure assets.
Key takeaways
There are a number of immediate steps to be taken by organisations that may be impacted by the SOCI Act, including:
- Gathering asset information to identify whether they
are captured as the owner, operator or direct interest holder in
critical infrastructure assets. This assessment is
sector specific and will be a more complex assessment for
organisations in some sectors than others. An asset audit should be
undertaken to ensure that critical infrastructure assets are
properly identified and, where relevant, ensuring that reporting
and other obligations are complied with in relation to those
assets.
- Ensuring existing cyber incident
response plans include processes for quick identification of cyber
incidents and their impact on critical infrastructure
assets. This step is especially important for
responsible entities for asset classes that have been 'switched
on' so they can comply with the obligation to report relevant
incidents to the Australian Cyber Security Centre within 12 hours
and 72 hours (as applicable) by no later than 8 July 2022 and take
appropriate action to address the incident.
- Considering internal processes and procedures to be
followed if the organisation were to receive a request for
information or a direction from the Government in response to a
cyber security incident. For example, how will the
request or direction be handled and to whom within the organisation
will it be escalated.
- Considering existing risk management processes relating
to critical infrastructure assets. It should be noted
that the risks to be managed are those arising
from all hazards (including supply
chain, people and natural and physical hazards), not just cyber
hazards and whether they are likely to require uplift once the Risk
Management Program Rules are finalised and come into effect.
- For responsible entities that engage third parties to assist with the operation of their critical infrastructure assets, review these arrangements. Where necessary, a responsible entity should seek to uplift those contracts to include contractual obligations on third parties to ensure that they will support the organisation's compliance with its obligations under the SOCI Act (including by the provision of information and co-operation with the security requirements).
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.
 |
 |
| Lawyers Weekly
Law firm of the year
2021 |
Employer of Choice for Gender Equality
(WGEA) |






