The opposed patent relates to a hearing device and related method. The patent propieter argued that the interrelated claim features provided a credible technical effect of secure, resource-efficient hearing device communication, supported by expert declarations. However, the Board disagreed and held that the alleged technical effect was not credibly achieved across the claim scope.
Here are the practical takeaways from the decision: T 1465/23 of June 24, 2025, of the Technical Board of Appeal 3.5.05.
Key takeaways
The problem-solution approach may be terminated at this stage if the distinguishing features do not credibly achieve any technical effect over the whole scope claimed.
The introduction of a distinguishing feature having no credible technical effect may then be considered to be no more than an arbitrary modification of the design of a known subject-matter which, being arbitrary, cannot involve an inventive step under Article 56 EPC.
The invention
The Board summarize the invention as follows:
1.1 The opposed patent addresses the problem of securing wireless communications for hearing devices. The background section of the opposed patent explains that, as hearing devices become more advanced, they increasingly communicate wirelessly with external devices like fitting apparatuses or smartphones. This use of open standard-based communication interfaces poses, according to the opposed patent, security challenges, making the hearing device vulnerable to attacks that could cause malfunction or battery exhaustion. A further challenge in that regard is that hearing devices are resource-constrained in terms of computational power and memory, i.e. that complex, "off-the-shelf" security algorithms and protocols cannot be readily implemented.
1.2 To solve this problem, the opposed patent proposes a hearing device and a corresponding method for establishing a secure communication session between the hearing device and a client/fitting device. The claimed solution is based on a specific authentication protocol, which is best illustrated by the signalling diagram depicted in Figure 4 of the opposed patent...
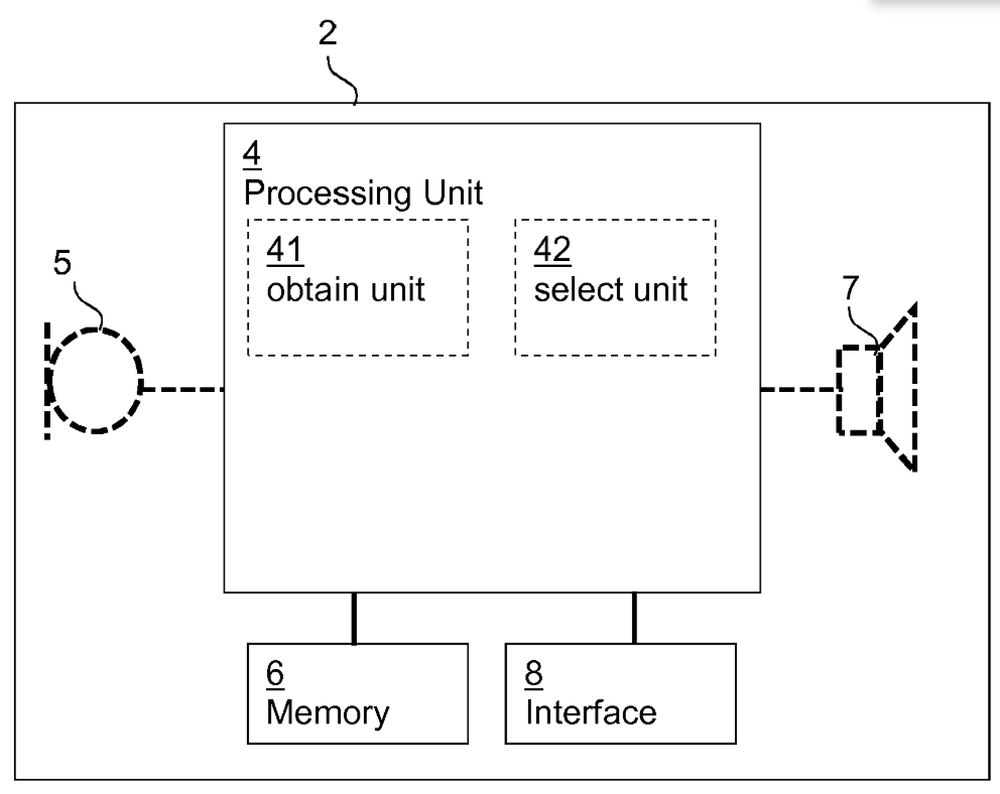
Fig.2 of EP3113515
-
Claim 1 of the main request reads as follows (board's feature labelling):
(a) "A hearing device (2) comprising – a processing unit (4) configured to compensate for a hearing loss of a user of the hearing device (2); – a memory unit (6); and – an interface (8), characterised in that the processing unit (4) is configured to: (b) – receive a connection request (410,411) for a session via the interface (8); (c) – obtain a session identifier (180); (d) – transmit, via the interface (8), a connection response (412) comprising a hearing device identifier (112) and the session identifier (180); (e) – receive, via the interface (180), an authentication message (420,421) comprising an authentication key identifier (166) and client device data (109); (f) – select a hearing device key from a plurality of hearing device keys in the memory unit (6) based on the authentication key identifier (166); (g) – verify the client device data (109) based on the selected hearing device key; and (h) – terminate the session if the verification fails."
Is it patentable?
The patent propieter argued that the distinguishing features provid the following effect:
2.2 The respondent submitted that the technical effect of features (b) to (h) was to provide a hearing device that was "capable of performing various levels of authentication of a communicating party and received messages as well as deriving keying material for securing communication, e.g. against eavesdropping and modification attacks as illustrated in the application as filed, page 2 lines 15-19". During the oral proceedings before the board, this was refined to providing protection against "modification attacks" (cf. page 2, lines 12 to 14 of the application as filed).
However, the Board disagreed:
2.3 The board is not satisfied that the technical effects mentioned by the respondent are credibly achieved by the claimed features, especially by the combination of features (b) to (h), over the whole scope of claim 1 as granted. In particular, this claim is silent on any "levels of authentication" and its features do not necessarily imply protection against attacks such as "eavesdropping" or "modification". Instead, as the appellant argued during the oral proceedings before the board, the features of claim 1 as granted constitute a mere aggregation of functionally disconnected security-related jargon, i.e. a collection of "islands of cryptography" without a clear and reliable interrelationship. The respondent's counter-argument that these features were all causally interrelated was not substantiated beyond a mere reference to the use of definite articles (e.g. "the session" and "the verification"). The board finds that, while this use of definite articles may arguably create a linguistic link between the features, it fails to establish a technically meaningful, functional interrelationship that would in fact be required to produce the alleged security effect. As will be detailed in point 2.4 below, claim 1 remains fundamentally ambiguous as to how these "islands" are actually connected.
2.4 For the purposes of claim construction regarding claim 1 as granted, the board, in accordance with the finding of the Enlarged Board of Appeal in G 1/24 (see its Order and Reasons 12 and 18), has "consulted" and "referred to" the present patent description and drawings to define the skilled reader from whose perspective or view point a claim is to be interpreted (see e.g. T 1924/20, Reasons 2.7). In view of, for example, paragraphs [0001] to [0007] of the patent description, the technical field of that skilled reader is apparently "hearing device security". Such a skilled reader of present claim 1 would however be faced with fundamental ambiguities that militate against the presence of a credible technical effect over the whole scope claimed. In the relevant technical field, terms relating to communication protocols have typically a stable and well-understood meaning. Therefore, contrary to the approach taken by the respondent during the oral proceedings before the board, these terms are not to be re-interpreted or understood in a more limited way in the light of the specific embodiments of the patent description, which, in addition, contain subject-matter that is more limited than that claimed (see e.g. also T 1999/23, Reasons 5.6).
Specifically, the board points to the following deficiencies in the claim's definition of the underlying subject-matter for which the respondent seeks to derive a technical effect:
2.4.1 Claim 1 as granted fails to define any necessary link between the "connection request" of feature (b), the "session" of feature (b) and the "session identifier" of feature (c). It is not even apparent that a "session" must be established for the steps underlying features (b) to (g) to occur.
2.4.2 According to the wording of claim 1, the "hearing device identifier" transmitted within the meaning of feature (d) is not required to be an identifier of the "hearing device" performing the method. It could, for instance, well be the identifier of a contralateral device in a binaural system, rendering it irrelevant for authenticating the party at the other end of the connection.
2.4.3 Present claim 1 does not require that the sender of the "connection request" in feature (b) is the same party that receives the "connection response" in feature (d) and sends the "authentication message" in feature (e). Instead, the process steps underlying features (b) to (h) could in fact involve multiple, different devices.
2.4.4 Furthermore, claim 1 as granted fails to specify what is actually being "authenticated" by the "authentication key identifier" in feature (e). The board notes that the respondent's own expert witness (see declaration E2) implicitly assumed that this authentication step related to "the authenticity of a message" and highlights that this particular purpose of the "authentication" mentioned in feature (e) is not apparent from the claim itself.
2.4.5 The terms "based on" and "verify" used in features (f) and (g) are fundamentally ambiguous, leaving their technical implementation open to a myriad of interpretations:
– The term "based on" used in feature (f) does not require a direct functional or causal link between the "authentication-key identifier" and the selected "hearing-device key". Rather, the selection could be mediated by a series of indirect look-ups, meaning that there is no guaranteed, technically meaningful constraint between the identifier received and the key selected.
– Feature (g) suffers from a similar ambiguous definition. While the verification of the "client device data" must be "based on" the selected key, this term, as established for feature (f), is itself vague. More fundamentally, the nature of the "verify" operation is undefined. As the appellant argued, it could range from a robust cryptographic check to a technically trivial, non-cryptographic comparison, such as confirming the presence of a data field or checking a message length. Claim 1 as granted therefore does not necessarily imply any cryptographic operation that would provide "various levels of authentication" or security against "modification attacks".
2.4.6 The condition for termination according to feature (h), i.e. "if the verification fails", is equally ambiguous. This is because a verification could "fail" for many non-security-related reasons, such as a processing timeout or a user error.
2.5 Due to these deficiencies, the asserted technical effects of providing multiple "levels of authentication" or protecting against "modification attacks" are not credibly achieved over the whole scope of claim 1.
2.6 Given that the alleged technical effect is not credibly achieved and the board cannot identify an effect either, it is not possible for the board to formulate an objective technical problem that is directly and causally related to the claimed invention, in particular to the alleged distinguishing features (b) to (h).
2.7 Following the principles established in G 1/19 (cf. Reasons 49, 82 and 124; see also points 3.1 and 3.3 below), the problem-solution approach may be terminated at this stage if the distinguishing features do not credibly achieve any technical effect over the whole scope claimed. This emanates from settled case law according to which, if a technical effect is not obtained over the full breadth of a claim, at least a subset of the claimed subject-matter is not to be seen as a technical solution to a technical problem and hence cannot be acknowledged as an "invention" involving an inventive step within the meaning of Article 56 EPC (see e.g. T 939/92, Reasons 2.7; T 176/97, Reasons 4.4, last paragraph; T 1294/16, Reasons 26.2). Hence, the introduction of a distinguishing feature having no credible technical effect may then be considered to be no more than an arbitrary modification of the design of a known subject-matter which, being arbitrary, cannot involve an inventive step under Article 56 EPC (see e.g. T 939/92, Reasons 2.5.3; T 72/95, Reasons 5.4; T 746/22, Reasons 1.5). The rationale behind this is to avoid irrelevant and thus superfluous comparisons between claim features which, after all, may be selected by the skilled person in an arbitrary way, and the prior art. In other words, the comparison between a claim, whose subject-matter cannot credibly solve any technical problem, and the technical teaching of a prior-art document can only lead to an artificial and superfluous exercise, i.e. looking for incentives, hints or a motivation comprised or implied in that prior-art document for arriving at a solution which falls within the terms of such an ill-defined subject-matter. This exercise may be likened to a search for a black cat in a dark room that is actually not there. Similarly, searching for an alternative way to cause a technical effect that is not credibly achieved by the claimed subject-matter does not help either; as also looking for a grey cat in the same dark room does not appear to be useful (see also point 3.3.2 below). In such a case, the distinguishing features which have no effect are considered to be an arbitrary and/or non-functional modification of the prior art, which cannot support an inventive step (see T 72/95, Reasons 5.4; T 1294/16, Reasons 26.2; T 287/23, Reasons 2.8.2 and 2.8.3; T 1580/23, Reasons 2.2.8).
2.8 In the present case, for the above observations, the board concludes that features (b) to (h) represent such arbitrary and non-functional modifications.
Therefore, the Board considered that the subject-matter was not inventive.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


