In this decision, the European Patent Office refused to grant a software patent on an efficient spam filter. Here are the practical takeaways of the decision T 2147/16 of September 7, 2021 of Technical Board of Appeal 3.4.03:
Key takeaways
A further technical effect must be proven and specifically and sufficiently documented in the disclosure of the invention.
The invention
The Board in charge summarized the invention of the application underlying the present decision as follows:
2.1 The present invention has as object to provide an efficient spam filter. Spam messages present the inconvenience of "cluttering" the user's email box, such that the user may easily overlook an important message in the flow of numerous spam messages. Spam messages take up a substantial volume of the email traffic. The share of spam includes more than 70% of global mail traffic. The spam messages accumulate in user mail boxes and take memory space and time to clean out (page 1, line 10ff of the description as filed).
2.2 Among the spam messages there are messages with computer viruses leading to harm of computer hardware/software and messages which lead to phishing resources that can be a cause of theft of passwords and personal data. Prior methods of spam detection, which typically involve grouping of messages by various criteria, often result in false positives, i.e., when the spam message ends up in the group of legitimate messages or when the legitimate message is grouped as spam.
To overcome these drawback, the application suggests a specific algorithm, inter alia including steps of hashing, clustering, weighting etc.
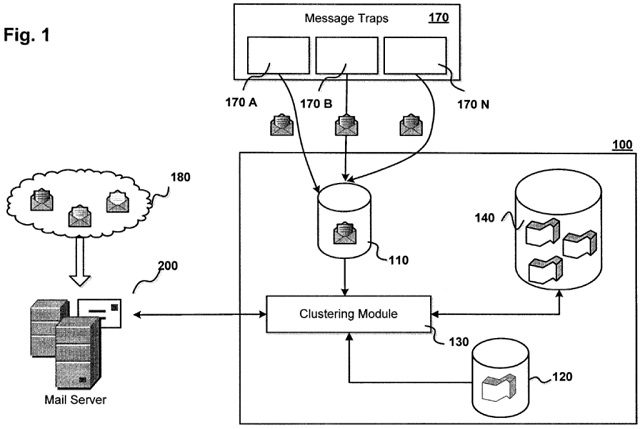
Fig. 1 of EP 2 811 441 A1
Here is how the invention is defined in claim 1:
Claim 1 (main request)
(A) A computer-implemented method for classification of electronic messages being e-mail messages as spam or legitimate on a client mail server (200), the method comprising:
(B) receiving (510), by a computer processor (15) of the client mail server (200), all electronic messages (180) directed to different users who have email addresses registered on the client mail server (200);
(C) classifying (515) the received electronic messages (180) as legitimate or spam messages;
(D) identifying (535) unknown messages that could not be classified as legitimate or spam;
(E) obtaining (550) metadata (860) of the unknown messages,
(F) the metadata (860) including at least a set of hash sums (830) for an unknown message and an IP address of a sender of the unknown message;
(G) placing (553) the metadata (860) of the unknown messages into one cluster of a plurality of clusters forming a cluster index tree based on a degree of similarity between a newly-arrived set of hash-sums {h1; h3 ... hk} from the metadata (860) and existing sets in the cluster index tree
(H) in accordance with: D = Sigma wj /k ,
(I) wherein the sum is formed over all weighting factors wj corresponding to hash sums in the cluster index tree that are matched by hash sums in the newly-arrived set {h1; h3 ... hk};
(J) rating (590) each unknown message in accordance with a rating of the cluster where the metadata (860) of the unknown messages was assigned to,
(K) wherein the rating of the cluster is based, at least, on a number of similar hash sums (830) of unknown messages received from different IP addresses of message senders contained in said cluster; and
(L) classifying (560, 565) unknown messages as legitimate or spam based on message ratings.
Is it technical?
The first instance Examining Division refused the application due to the following reasons:
(a) a spam filter did not serve a technical purpose;
(b) it did not produce a relevant technical effect;
(c) it did not imply technical considerations.
Besides some minor inadmissible amendment and clarity issues, the Board in charge was mainly concerned with the assessment of technicality and inventive step. In this respect, the Board indicated that it agrees to the arguments provided by the Examining Division that the claimed method, particularly the distinguishing feature, lack technical character.
To defend its application, the appellant argued that the claimed method facilitated an improved performance of a computer and computer network and decreased on the end user computer the memory volume of the hard disk required for the legitimate electronic messages due to decreasing an amount of spam. Furthermore, the appellant stated that the method decreased a volume of the email traffic to the end user computer and that it decreased a load for the processor at the end user computer:
5.3.6 The Appellant argued that in the proposed algorithm rather than processing all received electronic messages on each individual user computing device, the invention used a client mail server. Design and implementation of innovative algorithms and data structures went beyond a particular mathematical formulation of the task of classifying electronic messages. The invention utilised a cluster rating system to obtain and analyse metadata of the unknown messages and classify these unknown messages using a cluster index tree data structure. The cluster rating was dynamically changing during the course of the filling of all clusters with various metadata of incoming electronic messages. The invention analysed mass messages sent by various sources over time and updated cluster ratings and therefore allowed to classify unknown messages more accurately. The method therefore facilitated an improved performance of a computer and computer network. Therefore, the method achieved the technical effects mentioned in section VIII above.
In response, the Board agreed to the appellants arguments in so far that the claimed algorithm may be optimized for the computer hardware and may thus have technical character. However, this would only be of speculative nature:
5.3.7 The Board agrees in so far with the arguments of the Appellant as the combination of comparing digital text content by similarity preserving hashing and dynamic cluster rating may be considered an algorithm optimised for the computer hardware and may have a technical contribution. However, this mere assumption is not sufficient. ...
According to the Board, to be patentable, an algorithm must fulfill the following three criteria:
(a) the implementation of an algorithm in a method for filtering spam messages must have a proved further technical effect or specific technical considerations;
(b) such further technical effect must be specifically and sufficiently documented in the disclosure of the invention and be reflected in the claim wording;
(c) the algorithm must serve a technical purpose.
Concerning criterion (a), the Board stated that specific details as to how an algorithm is implemented in practice and how the load is reduced must be provided in order to give evidence that the algorithm has any further technical effect. However, the present application did not do so:
5.3.11 The present invention, page 19, lines 1 to 8, discloses that the cluster size has to be optimised in order to reduce the load on the computer. However, further details are not provided, for example, the range of the optimal cluster size, relevant parameters, the amount of memory saved or the ratio of increased speed.
With respect to criterion (b), the Board arrived at the conclusion that the application failed to provide any details how the alleged further technical effect is achieved:
5.3.14 However, the present invention does not provide sufficient and specific disclosure, such as parameters, how the algorithm is optimised for the computer, nor is this reflected in the claim wording.
5.3.15 The Board is of the opinion that any further technical effect has to be specified and sufficiently disclosed in the invention and that the claims must comprise the specific features which contribute to the further technical effect of the invention.
Finally, also the third criterion (c) was considered not to be fulfilled since the claimed method fails to serve a technical purpose:
5.3.18 The Board is of the opinion that, if the algorithm claimed in the present invention depends on the preferences of the user, the purpose of the claimed method may be considered non-technical. Spam filters in general need a human conditioning for training an algorithm which kind of emails should to be classified as spam messages and which kind of emails should be kept in the mail box. This depends on the individual user preferences, ...
Against this background, the Board concluded as follows:
5.4.2 According to G 1/19 (reasons 121) algorithms first of all define (non-technical) constraints to be considered in the context of the COMVIK approach (T 0641/00). Depending on whether they contribute to any technical effect achieved by the claimed invention, they may or may not in fact be taken into account in the inventive step assessment.
5.5 Obviousness
5.5.1 As discussed above a special technical effect related to the algorithm as defined in the independent claim is not sufficiently documented in the present application and is not reflected in the claim wording. The claim therefore defines a mere implementation of an algorithm without any additional special technical effect. This mere implementation of an algorithm cannot be considered involving an inventive step.
At the end, the Board dismissed the appeal due to lack of inventive step.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


