Ransomware is extortion software aimed at profiting from the ransom paid by the victim. But why should a ransomware victim pay, and what happens if they don't? I will try to answer these questions in this article and then briefly show you what such an attack might look like.
Ransomware is malicious software, or malware, that can enter your computer through fraudulent sites, phishing e-mails, downloading and running infected files and applications, or even simply using unknown flash drives. However, ransomware targets companies rather than individuals. It is usually much more sophisticated than regular Trojans and viruses. After infecting a computer, ransomware usually spreads to organisations to infect major servers, all computers, and most importantly, backups! Once a company's network (including its backups) is compromised, the chances of a simple resumption of operations are extremely slim. You can recognise the attack by the screen making the ransom demand to stop this attack. The attackers usually seek payment in cryptocurrency, to ensure anonymity. What this unwelcome message may look like is shown in the following visual.
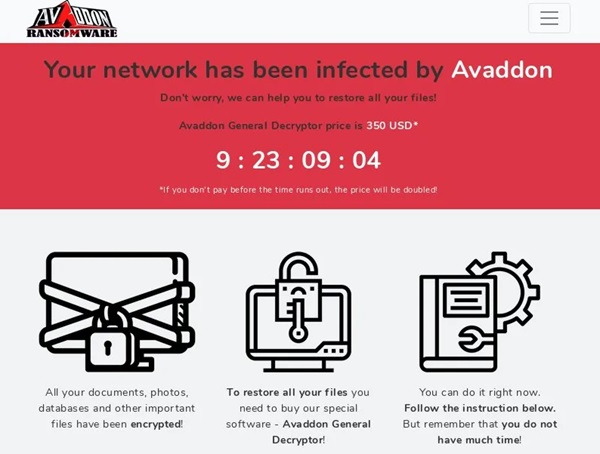
(Source: https://howtoremove.guide )
If this or a similar screen appears in your company, there are several ways to proceed. The first is to pay the ransom to the attackers by the deadline according to their instructions and hope that they will keep their word and provide you with a decryption program. Another option is to decide to fight. This includes trying to restore systems from backups, reconfiguring and cleaning. This process can be very lengthy and for a large company, a failure of a few days can mean huge losses. It should be noted that the ransom prices are not negligible and can be in the order of millions of crowns.
Avaddon ransomware
Avaddon is a cryptolocker ransomware (file encryption program) written in C ++ that is best known for encrypting files and changing the file extension to .avdn. Ransomware also removes shadow copies of volumes and other system backups and usually requires a ransom in the range of USD 150 – 900, i.e. approximately CZK 3,000 – 20,000. The victim usually has 240 hours to pay the ransom. Because the ransomware uses strong encryption algorithms such as AES256 and RSA2048, there is no known decryption program and it is not possible to decrypt the file without the key that was used to encrypt it. This ransomware is sold, like other ransomware, as a service (RaaS - Ransomware as a Service). Therefore, even someone with limited technical expertise can become an "affiliate" to the spread of malicious software. In return, the profit is shared between the instigator of the threat and the affiliate.
Avaddon ransomware specialises in customer privacy, financial information, databases, credit card information and more. However, encrypted files are not the main problem. Companies usually do not understand the risk of information leakage, especially private information. Such leaks lead to client losses, fines and litigation. Of course, this information can also fall into the hands of competitors.
What can happen if the victim decides not to pay the ransom?
As soon as a company is attacked by Avaddon ransomware, the details of the attack are published on the Avaddon website via a dark website. The first thing you will notice is the part showing the currently attacked company together with the deadline for paying the ransom. The image below shows several companies with currently active Avaddon ransomware, but as of the date of this writing, this list numbered 27 companies!
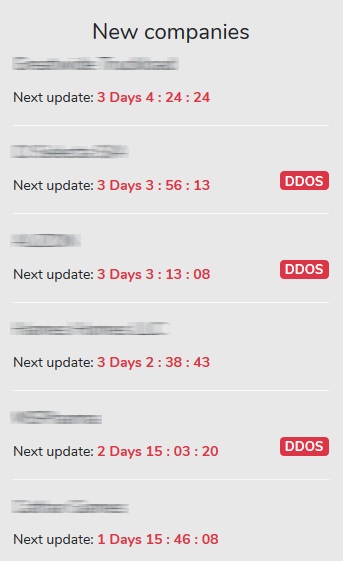
(Source: Avaddon Ransomware – dark web)
Along with this, the details of the company with a sample of stolen documents are also shown here, which can be seen in the picture below. Here you can see the name of the company, its address, website, the date for payment of the ransom and brief information about the data obtained.
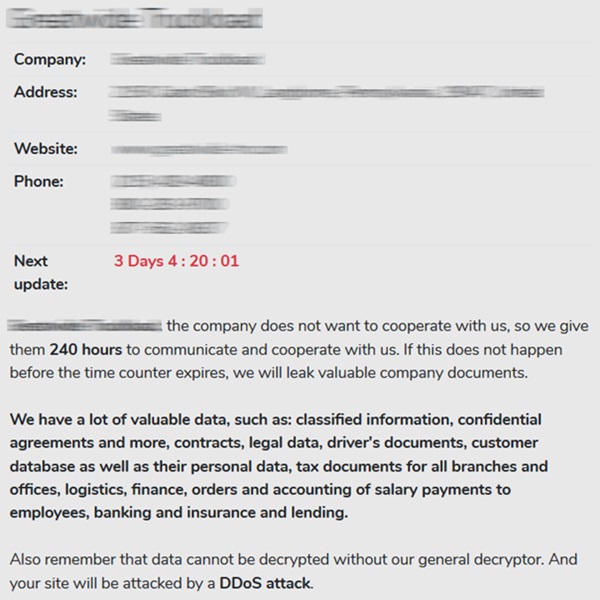
(Source: Avaddon Ransomware – dark web)
If the victim decides to pay the ransom, there is a good chance that this information will disappear from the site and they will be provided with a decryption program to recover their data. Otherwise, this program will not be provided and sensitive company documents may be disclosed. Information on more than 60 companies is available on the Avaddon ransomware website at the time of writing. You can also download sensitive information from these companies, which number hundreds of gigabytes. A fragment of this list can be seen in the image below. This data can be easily downloaded by anyone in the form of a .zip file.
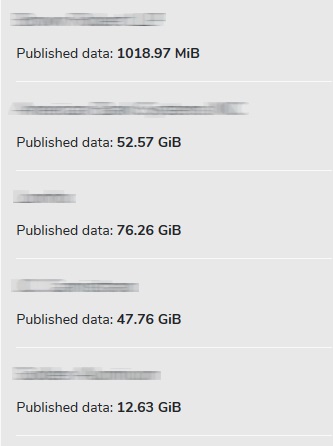
(Source: Avaddon Ransomware – dark web)
Recently, several Czech computer and telecommunications companies also fell victim to Avaddon ransomware, resulting in a breakdown of their services for at least several days. It is therefore important not to take this threat lightly. Small and large companies must constantly work to improve their cybersecurity!
How to prevent ransomware attacks?
To avoid being infected with various malware, it is generally recommended that you keep applications up-to-date, install security system updates, and back up regularly. It is important (for the reasons described above) to keep these backups outside the company's location, ideally without direct remote access to them. It is important to have IDS / IPS systems deployed that can detect malicious network operations, a properly configured firewall on the outer perimeter of the network, and properly set up and require security policies inside and outside the company. Another important aspect is regularly training employees in the field of cybersecurity.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

