- within Technology topic(s)
- in United States
- with readers working within the Technology and Retail & Leisure industries
- within Cannabis & Hemp, Coronavirus (COVID-19) and Insolvency/Bankruptcy/Re-Structuring topic(s)
Key Takeaways
- Manufacturing supply chains have become high‑value targets for cybercriminals, facing relentless attacks as the industry remains the most targeted sector for the fourth consecutive year. Supply chain-related attacks have surged 431% since 2021 and are among the costliest and slowest to resolve.
- Insufficient vendor oversight creates critical cybersecurity gaps. Many manufacturers fail to adequately monitor third- and fourth-party suppliers, allowing threat actors to exploit trusted network connections and infiltrate primary targets through weaker links in the supply chain, expanding the scope of a cyberattack and amplifying supply chain cyber risk exposure.
- Cyber resilience strengthens manufacturing supply chains and market edge. Integrating security‑by‑design principles, robust vendor due diligence, and Cyber Supply Chain Risk Management (C‑SCRM) practices into operations empowers manufacturers to build secure, agile, and sustainable supply chains, enhancing both business continuity and market competitiveness in today's threat‑intensive digital landscape.
The manufacturing industry remains the most targeted sector for cyberattacks for the fourth year in a row.1 Over 26% of cyber occurrences worldwide target the manufacturing industry. Supply chains are often the target as they become more digitized and interconnected. The threat landscape shifts rapidly, with increasingly sophisticated attacks targeting every link in the supply chain ecosystem, from software vendors and logistics providers to manufacturers and distributors.
As manufacturers build out their U.S. supply chains, they're not just expanding operations—they're laying the foundation for long-term resilience. By integrating cybersecurity best practices from the start, companies can turn risk management into a competitive advantage for their operations and ensure their growth is both secure and sustainable.
Cyberattacks on Supply Chains Continue to Rise
Supply chain cyberattacks have surged dramatically in terms of prevalence, cost, and resolution timelines. Between 2021 and 2023, the number of supply chain-related attacks increased by 431%.2 Last year, they became the second most prevalent attack vector (accounting for 15% of all breaches last year).3 They are also the second costliest type of attack. The average cost of a breach in the U.S. continues to rise as it increased by 9% in 2025 to $10.22 million USD (based on data pertaining to 2024-related breaches) and even higher for supply chain compromises.4 Supply chain attacks also take the longest to resolve. Last year, cyber-related compromises to the supply chain took a combined 267 days to detect and contain.5
Why? Research suggests that businesses do not adequately oversee their vendors, which leads to latent detection and increased costs and resolution horizons when cyberattacks are finally detected. For instance, a 2024 survey conducted by Gartner – the world's leading research and advisory company – reveals that while 95% of organizations saw a red flag associated with their third-party vendors in the past 12 months, only around half of them escalate it to compliance teams.6
Attackers exploit these trusting relationships and expansive networks. As detailed below, attackers take advantage of the established trust between suppliers, vendors, manufacturers, and customers and their computer-to-computer communications.7] They also target links further down the supply chain like third- and fourth-party suppliers. Attackers know that customers and their immediate suppliers often do not maintain adequate oversight of, and undertake efforts to ensure compliance from, those providers further down the chain.8
This trend is unlikely to slow down, as we see attackers continuing to refine their techniques. The first step in combating these attacks is better understanding their common tactics in order to implement institutional best practices.
Supply Chain Cyberattacks: Evolving Technology but Familiar Tactics
How They Work
A supply chain cyberattack takes advantage of trusted relationships between supply partners. All organizations have a level of implicit trust in other companies as they install and use the company's software within their networks or work with them as a vendors. Hackers often opt for the path of least resistance, targeting the weakest link in a chain of interconnected ecosystems and software, due to their ability to infiltrate multiple organizations through a single point of compromise.
Thus, even if your organization is well-defended and has a strong cybersecurity program in place, in the event one of your trusted vendors is not secure, attackers will target that vendor to bypass whatever security is in place in the vendor's organization. They launch phishing schemes or social engineering attacks to compromise the credentials of a vendor's employee.
Once the attackers gain a foothold within a vendor's system, we have seen them explore and exploit vulnerabilities by moving laterally across the network. For example, they may exploit unpatched software vulnerabilities, weak access controls, or misconfigured systems to escalate their privileges and further deepen their penetration to use it as a launchpad to deploy malware or malicious code or otherwise gain access to the networks of the primary target organizations. This weak-link pathway bypasses otherwise extremely difficult security measures to attack directly.
These threats have global implications. We have seen hackers – intentionally or unintentionally –gain control over any organization's entire infrastructure, even if it has not been directly targeted. Also, as mentioned above, it is not just immediate suppliers that organizations must worry about; the risks could run much deeper into the supply chain with third- and fourth-party suppliers, as the impact of a single supplier being disrupted can affect multiple parties down the chain.
Some Common Types of Cyberattacks Impacting Supply Chains
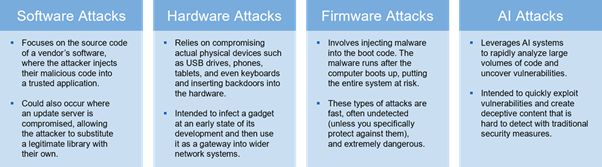
While tactics like phishing, ransomware, and malware remain widespread, the rapid evolution of artificial intelligence (AI) is making the cybersecurity landscape even more challenging. In fact, 16% of data breaches already reported in 2025 have involved some form of AI.9 Threat actors are now leveraging AI to generate highly convincing deepfake impersonations, craft realistic phishing campaigns with unprecedented speed, and identify and exploit vulnerabilities across complex supply chains.10 For instance, threat actors may use AI to quickly scan publicly accessible profiles of the target company's executives and use such information to create phishing emails, tailored to each recipient's role and communication style, directing unknowing employees to click malicious links that reveal their login credentials to unauthorized third parties.
Three high-profile cybersecurity incidents to supply chains illustrate these tactics in action.
- Ransomware Attack Impacting in the Energy Sector (January 2024): A multinational energy management corporation suffered a substantial ransomware attack after threat actors, believed to be associated with the Cactus ransomware gang, gained initial access to its systems by exploiting a vulnerability related to a VPN device. The attackers claimed to have exfiltrated 1.5TB of sensitive data, and leaked 25 MB of this data, which included copies of non-disclosure agreements and scanned passports of American citizens. To date, the cost of this attack and the number of customers affected is not currently known. However, it is likely significant given the corporation serves more than 2,000 customers worldwide.11
- Cloud-Based Data Platform Hack (April 2024): A popular cloud-based data platform experienced a significant data breach when a software engineer used credentials stolen through infostealer malware to infiltrate the network. This breach compromised the data of 165 customers, who collectively process data for over 500 million individuals. As of the date of this writing, the total cost of the breach remains unknown.12
- Ransomware Attack on a Global Logistics Provider & Freight Forwarder (Aug. 2024). A major global logistics and freight forwarding company experienced a ransomware attack, causing technical disruptions and impacting service delivery. Customer service, billing, payment systems, and data integration with customers' and vendors' systems were all impacted. The central operations system, and customer-facing portal were offline for several days (with the effect of the latter preventing customers from tracking their shipments in real time, creating logistical challenges globally).As of the date of this writing, the total cost of the incident remains unknown.13
Best Practices for Mitigating Cyber Risks Across Your Supply Chain
Be proactive. Supply partners must adapt to these surging threats by managing and preparing for supply chain risks and cyber-related disruptions rather than merely reacting to problems as they occur. Your supply chain is only as strong as its weakest link. Think internally and across your supply chain to implement security protocols.
- Security by Design. Implement security by design principles during the product development and implementation phases. By embedding security measures early, organizations can reduce exploitable flaws and help bolster the resilience of their supply chain systems.
- Risk Management Framework. Implement a comprehensive risk management framework that integrates Cyber Supply Chain Risk Management (C-SCRM)principles.14 C-SCRM is a systematic process for managing exposure to cybersecurity risk throughout supply chains and developing appropriate response strategies, policies, processes, and procedures. In addition, the National Institute of Standards and Technologies ("NIST")Cybersecurity Framework (CSF) 2.0provides a structured approach to managing cyber risks and can serve as a foundation for organizations of all sizes and sectors to develop their risk management strategies.15 CSF 2.0 also includes additional C-SCRM outcomes to help organizations address these risks. The subcategories within the CSF C-SCRM Category [GV.SC] serve as a bridge, linking cybersecurity-focused outcomes with broader C-SCRM objectives.
- AI and Software-as-a-Service ("SaaS") Governance. Catalog and control all use of all internal (e.g., employees) and external parties' (e.g., suppliers) AI solutions and SaaS tools to help minimize exploitable vulnerabilities throughout the supply chain. As AI evolves, organizations should update security training for AI-driven threats, assess third-party risks, and establish AI governance to maintain security. It's critical to remember that a governance program is only effective if employees understand how to correctly adhere to its policies and procedures.
- Vendor Due Diligence. Conduct thorough due diligence when selecting vendors, and assess their cybersecurity posture, incident response capabilities, resilience, and adherence to applicable laws, regulations, and industry standards in relation to data protection and security. This helps in identifying and mitigating potential risks associated with third-party vendors.
- Thorough Assessments of Existing Vendors. Regularly carry out security assessments and audits of existing vendors to evaluate the effectiveness of cybersecurity controls and practices and to ensure compliance with relevant security standards and other applicable legal and contractual requirements throughout the supply chain lifecycle. It is also recommended that you implement C-SCRM practices to identify and mitigate supply chain risks associated with third-party providers. In addition, vendor management requires effective communication throughout the organization to ensure that any material issues or security-related issues involving third-party vendors are properly escalated up the chain for remediation.
- Vendor Contracts. Ensure there are robust cybersecurity requirements in every RFP and contract with a key supply chain provider that covers or addresses, at a minimum, clearly defined responsibilities and liability allocation with vendors, resiliency of the providers' own systems, regular training of its personnel, prompt notice of security incidents and continued cooperation with your organization in connection therewith, periodic audits, subcontracting, and other related measures necessary for compliance with applicable laws and industry standards. Companies should also regularly review and update existing vendor contracts to ensure that sufficient cybersecurity requirements are in place and seek addenda where there are not.
- Continuous Monitoring and Detection. Implement continuous monitoring and detection mechanisms to identify and respond to cyber threats in real-time. For example, organizations should consider utilizing threat intelligence feeds, security information and event management (SIEM) systems, and intrusion detection/prevention systems to monitor for suspicious activities and anomalies involving systems and/or software used within your supply chain.
- Secure Access Controls, Encryption Measures, and Patch Management. Implement robust access controls and data encryption measures to protect sensitive information shared within the supply chain. Encrypting data both at rest and in transit helps in safeguarding it from unauthorized access or interception. Access controls (e.g., multi-factor authentication, role-based access controls, least privilege principles, etc.) help limit access to critical assets and systems by third-party providers. In addition, keep all software, including operating systems and applications, up to date with the latest security patches. Regular updates ensure vulnerabilities are promptly addressed.
- Incident Response and Business Continuity Plans. Develop or update existing incident response plans to include processes for responding to cyber incidents involving or otherwise originating from key third-party supply chain providers (and with relevant C-SCRM practices baked in to address supply chain-specific threats and vulnerabilities). In addition, it would be prudent to develop and regularly test business continuity and disaster recovery plans to ensure continuity of operations in the event of a supply chain cyberattack.
- Education and Awareness. Provide regular cybersecurity awareness training to employees, suppliers, and stakeholders to (i) educate them about the importance of common cyber threats and best practices, (ii) promote awareness about C-SCRM principles and the importance of supply chain security in mitigating cyber risks, and (iii) help them recognize and encourage them to report potential cyber threats.
Conclusion
For manufacturers expanding their U.S. footprint, now is the time to treat cybersecurity not as a compliance checkbox, but as a strategic enabler. A resilient supply chain isn't just safer—it's smarter, more agile, and better positioned for long-term success.
Otherwise, neglecting supplier risk management poses risks of significant financial loss, intellectual property theft, reputational damage, and societal impact. Although cyber threats are unavoidable, businesses can significantly minimize their effects by establishing a strong supplier risk management framework and enhancing security measures. In doing so, businesses will be able to better protect their valuable assets, reputation, and stakeholder relationships.
Footnotes
1 See IBM X-Force 2025 Threat Intelligence Index, available at https://www.ibm.com/thought-leadership/institute-business-value/en-us/report/2025-threat-intelligence-index (last accessed Aug. 17, 2025).
2 See Cowbell Cyber, Cyber Roundup Report 2024, p. 4, https://cowbell.insure/wp-content/uploads/pdfs/CB-US-Q4-CyberRoundupReport24.pdf (last accessed Aug. 17, 2025).
3 Id. at p. 17.
4 PonemonInstitute (sponsored, analyzed, and published by IBM), Cost of a Data Breach Report 2025 (Aug. 2024) (hereinafter, "Cost of a Data Breach Report"), at p. 4, available at https://www.ibm.com/reports/data-breach (registration required to access content) (last accessed Aug. 17, 2025).
5 Id. at p. 18.
6 Gartner, Gartner Says Compliance Leaders Need Consistent Communication with Relationship Owners to Effectively Manage Third-Party Risk (April 23, 2025), https://www.gartner.com/en/newsroom/press-releases/2025-04-23-gartner-says-compliance-leaders-need-consistent-communication-with-relationship-owners-to-effectively-manage-tihird-party-work.
7 See Cost of a Data Breach Report, at p. 18.
8 See id.
9 See id. at p. 38.
10 See id.
11 Secureframe, 20 Recent Cyber Attacks & What They Tell Us About the Future of Cybersecurity (Jul. 15, 2025), available at https://secureframe.com/blog/recent-cyber-attacks (last accessed Aug. 17, 2025).
12 Ravie Lakshmanan, Snowflake Breach Exposes 165 Customers' Data in Ongoing Extortion Campaign (Jun. 11, 2024), available at https://thehackernews.com/2024/06/snowflake-breach-exposes-165-customers.html (last accessed Aug. 17, 2025).
13 World Economic Forum, Why Cyber Resilience Should be a Top Priority for Freight Forwarders (Jun. 4, 2025), available at https://www.weforum.org/stories/2025/06/cyber-resilience-top-priority-for-freight-forwarders/.
14 NIST SP 800-161 Rev. 1 (2024), https://csrc.nist.gov/pubs/sp/800/161/r1/upd1/final.
15 NIST Cybersecurity Framework (CSF) 2.0 (2024), https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.



