- within Strategy topic(s)
The U.S. Department of Defense (DoD) recently issued a memorandum signaling that defense contractors soon will be required to comply with new cybersecurity compliance requirements. The memorandum establishes "organization-defined parameters" (ODPs) in "preparation" for implementation of National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 Revision 3, "as the minimum requirement for contractors[.]" DoD's publication of ODPs for NIST SP 800-171 rev. 3 signals that DoD is looking to soon adopt and incorporate rev. 3 as the new standard for Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012, Safeguarding Covered Defense Information and Cyber Incident Reporting (DFARS 7012), as well as DoD's Cybersecurity Maturity Model Certification (CMMC).
Compliance with NIST SP 800-171 Is Required by DFARS 7012 and CMMC
DFARS 7012, required in all solicitations and contracts except those solely of the acquisition of commercially available off-the-shelf items, specifies the security controls contractors must abide by when processing, storing or transmitting Controlled Unclassified Information (CUI) on information systems.1 The clause adopts and incorporates by reference the security requirements in NIST SP 800-171, "Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations." Per the clause's text, contractors are required to implement the NIST SP 800-171 security requirements "in effect at the time the solicitation is issued or as authorized by the contractor."2
However, in May 2024, DoD issued a class deviation stating that contractors subject to DFARS 7012 were to comply with NIST SP 800-171 rev. 2 instead of the version "in effect at the time the solicitation is issued or as authorized by the contractor."3 DoD issued the class deviation shortly before NIST published SP 800-171 rev. 3, which includes several significant changes from the previous version.4 DoD's intent for issuing the class deviation was "to provide industry time for a more deliberate transition" to rev. 3.5
Thus, NIST SP 800-171 rev. 2, published in February 2020 and updated in January 2021, remains the standard under DFARS 7012 and CMMC (see 32 C.F.R. part 170) – at least for now.
Rev. 2 vs. Rev. 3: Key Changes
Though rev. 2 is the current standard, defense contractors and subcontractors should be aware of the differences between the two versions so they are ready to adopt once rev. 3 becomes the new standard. Key changes between NIST SP 800-171 rev. 2 and rev. 3 include:
- updated security requirements and families to be consistent with NIST SP 800-53, Revision 5, "Security and Privacy Controls for Information Systems and Organizations"
- eliminated the distinction between "basic" security requirements (obtained from Federal Information Processing Standards Publication 200, Minimum Security Requirements for Federal Information and Information Systems) and "derived" security requirements (taken from the security controls in NIST SP 800-53) and established NIST SP 800-53 as the "single authoritative source" to increase specificity and clarity
- increased the level of detail in the security requirement specifications to reduce differing interpretations and subjective application of the requirements, as well as align the security requirement language with the control language in NIST SP 800-53
- withdrew certain requirements and incorporated them into other requirements where direct relationships or logical associations existed for efficiency and increased understanding6
- introduced organization-defined parameters (which are used in NIST SP 800-53) in select security requirements to provide flexibility to federal agencies
The last change, the introduction of organization-defined parameters, is the subject of DoD's April 2025 memorandum.
Organization-Defined Parameters (ODPs)
So, what is an ODP? An ODP is the "variable part of a security requirement that is instantiated by an organization during the tailoring process by assigning an organization-defined value as part of the requirement."7 Basically, ODPs increase flexibility by allowing organizations to tailor security controls (through "assignment" and "selection" operations) to specific security requirements based on specific protection needs. Think of them as "fill-in-the-blank" options. For example:
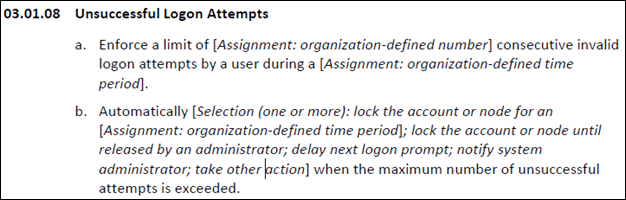
Source: NIST SP 800-171 Rev. 3 at 12
So, who determines ODP values? Not NIST. As explained by rev. 3, "The determination of ODP values can be guided and informed by laws, executive orders, directives, regulations, policies, standards, guidance, or mission and business needs."8 Thus, federal agencies are expected to formally establish or assign ODP values for selected security requirements.9 And, as of April 15, 2025, DoD has done just that.
DoD's ODPs for NIST SP 800-171 Rev. 3
DoD's April 2025 memorandum establishes and assigns ODP values for the security requirements in NIST SP 800-171 rev. 3.10 So what do these ODP values look like? Well, regarding the invalid logon attempts access control referenced above:
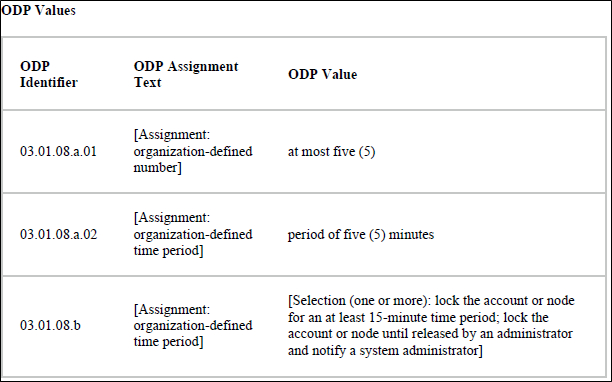
Source: DoD ODPs for NIST SP 800-171 Rev. 3 at 6
DoD's publication of ODPs should prevent hodgepodge implementation of the security requirements and ensure consistency. Defense contractors and subcontractors should take the time to start reviewing SP 800-171 rev. 3 in conjunction with the DoD ODPs.
Next Steps
Though rev. 3 is soon to be the standard, for now, defense contractors and subcontractors are expected to maintain compliance with rev. 2. Thus, compliance with DFARS 7012 and other DoD cybersecurity obligations11 should continue to track the security requirements in rev. 2. But DoD's publication of ODPs signals that compliance with rev. 3 is coming. Thus, contractors should start reviewing the updated security requirements now and prepare to update their System Security Plans and security controls accordingly.
Footnotes
1 DFARS 252.204-7012(b)(2).
2 DFARS 252.204-7012(b)(2)(i).
3 See DoD Class Deviation 2024-O0013, Safeguarding Covered Defense Information and Cyber Incident Reporting (May 2, 2024).
4 Helpfully, when publishing SP 800-171 rev. 3, NIST also published a change analysis of rev. 2 compared to rev. 3. This change analysis is available on NIST's website.
5 See DoD Press Release: Department of Defense Issues Class Deviation on Cybersecurity Standards for Covered Contractor Information Systems (May 2, 2024).
6 The net effect is a reduction in the total number of security requirements from 110 (rev. 2) to 97 (rev. 3).
7 NIST SP 800-171 rev. 3 at 90 (Glossary).
8 Id.a t 4.
9 Id.; see also NIST Frequently Asked Questions SP 800-171 Revision 2 and Revision 3 at 3.
10 See DoD Memorandum: DoD Organization-Defined Parameters for NIST SP 800-171 Revision 3 (April 15, 2024).
11 E.g., DFARS 252.204-7019, Notice of NIST SP 800-171 DoD Assessment Requirements (requiring contractors to conduct a NIST self-assessment according to NIST DoD Assessment Methodology and report self-assessment scores via the Supplier Performance Risk System (SPRS)) and DFARS 252.204-7020, NIST SP 800-171 DoD Assessment Requirements (notifying contractors that DoD reserves the right to conduct a higher-level assessment of contractors' cybersecurity compliance and providing that contractors must give DoD assessors full access to their facilities, systems and personnel).
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.



