- within Compliance topic(s)
In the ever-evolving landscape of cybersecurity, staying one step ahead of cybercriminals requires not just reactive measures but proactive strategies. One of the most effective ways organizations can enhance their cybersecurity posture is through dark web monitoring. This technique allows businesses to identify potential threats early and disrupt cyber-attacks that are in progress, thereby minimizing data breach risk and safeguarding sensitive information.
Understanding the Dark Web
The dark web is a part of the internet that is not indexed by traditional search engines and requires specific software, configurations, or authorization to access. It is often associated with illicit activities, such as the sale of stolen data, hacking tools, and other illegal goods and services. However, it also serves legitimate purposes, providing a platform for privacy-focused communication.
For cybersecurity professionals, monitoring the dark web is essential because it is a hub where cybercriminals frequently discuss, plan, and carry out cyber-attacks, as well as trade stolen data, credentials, and illicit services. By using experts to monitor these activities, organizations can obtain valuable insights into planned and ongoing threats that may target their assets.
Proactive Threat Identification
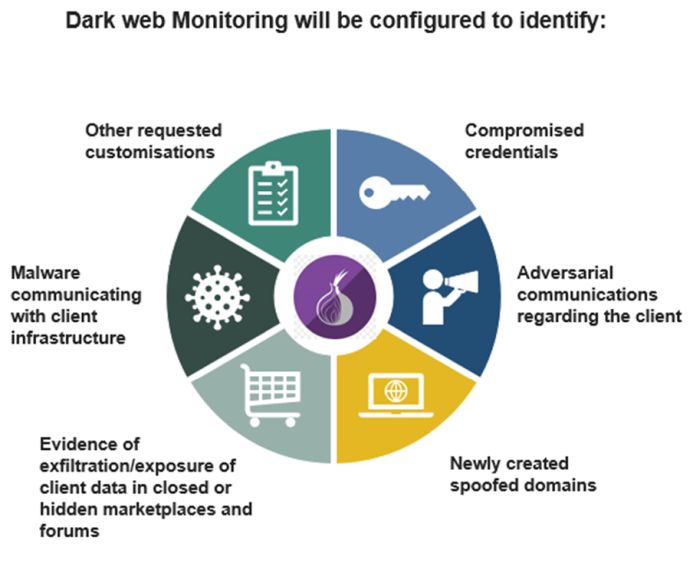
Dark web monitoring involves the continuous scanning of dark web forums, marketplaces, and other communication channels for signs of potential threats. This might include:
- Stolen Data: Detecting the sale or distribution of sensitive data, such as customer information, intellectual property, or employee credentials, can alert organizations to a breach they may not yet be aware of.
- Threat Intelligence: Monitoring discussions about specific vulnerabilities, exploits, or malware can provide early warning signs of an impending attack.
- Impersonation Attempts: Identifying attempts to impersonate your organization or its executives can help prevent phishing and other social engineering attacks.
By identifying these threats early, organizations can take pre-emptive action, such as patching vulnerabilities, enhancing security measures, or alerting affected parties to reset credentials and mitigate potential risks.
Enhancing Incident Response
In addition to identifying threats, dark web monitoring plays a critical role in incident response. When a breach occurs, understanding the scope and impact of the incident is vital. Dark web monitoring can aid in this by:
- Assessing Data Exposure: Quickly determining whether stolen data has been published or sold on the dark web can guide the response strategy and communication with affected stakeholders.
- Gathering Intelligence: Information gleaned from the dark web can provide insights into the tactics, techniques, and procedures (TTPs) used by attackers, helping to tailor the incident response and improve defenses.
- Tracking Stolen Assets: Monitoring for the appearance of stolen assets can help organizations recover them and prevent further unauthorized use.
Implementing Dark Web Monitoring
To effectively implement dark web monitoring, organizations can either build an in-house team with specialist tools, or a more cost-effective solution for many companies is to partner with cybersecurity firms specializing in threat intelligence. Key components of a successful dark web monitoring strategy include:
- Advanced Technology: Utilizing sophisticated tools that can navigate the dark web's complexities and analyze data efficiently and anonymously.
- Expert Analysts: Employing skilled analysts who understand the nuances of the dark web and can accurately interpret findings.
- Integration with Security Operations: Ensuring that insights from dark web monitoring are seamlessly integrated into existing security operations and incident response plans.
Case Study
Ankura actively monitors the dark web for regional cyber incidents and recently identified a known client's name on a ransomware leak site. In this instance, Ankura promptly alerted our client, who was unaware of the breach. The ransomware group had exfiltrated data from the client's cloud by exploiting a vulnerability in the service application programming interface. Since no encryption was applied, the attackers did not leave any ransom notes within the client's environment. Without Ankura's notification, the client would have remained unaware of the data theft.
Ankura's dark web monitoring swiftly detected the incident on the same day the leak site published the note, providing the client with timely intelligence to respond to this incident.
Conclusion
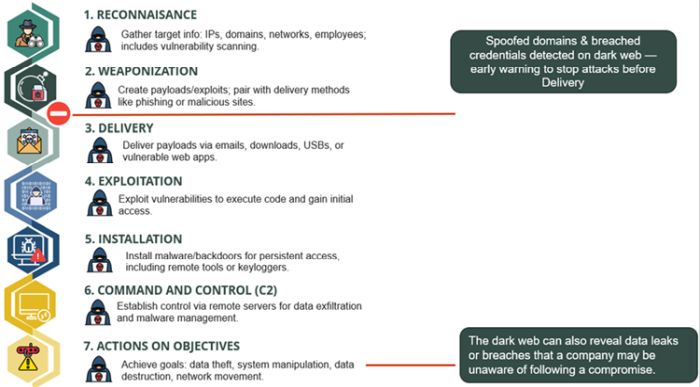
In today's digital age, where cyber threats are increasingly sophisticated and pervasive, dark web monitoring offers a valuable layer of defense. By proactively identifying potential cyber-attacks and enhancing incident response capabilities, organizations can protect their assets, reputation, and customers from the ever-present dangers lurking in the shadows of the internet. As part of a comprehensive cybersecurity strategy, dark web monitoring is not just a defensive measure but a proactive step towards a more secure future. Dark web monitoring and alerting services effectively break the cyber-attack kill chain, helping to stop bad actors breaching your network.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


