- within Cannabis & Hemp, Privacy, Media, Telecoms, IT and Entertainment topic(s)
- with readers working within the Insurance industries
This HIPAA Update provides a detailed description of the new breach notification requirements for HIPAA covered entities and business associates as required by interim final rule issued pursuant to the HITECH Act of 2009. The interim final rule (Breach Rule) published by the U.S. Department of Health and Human Services (HHS) on Aug. 24, 2009 became effective Sept. 23, 2009. It requires business associates and covered entities to notify individuals, HHS, and in some cases, the media, upon discovery of a breach of unsecured protected health information (PHI).
The rules set out a three-part test for: determining whether a breach has occurred, further clarifies the definition of "Unsecured PHI" and establishes requirements for when a breach must be reported, who must make the report, and how the report must be made. The agency also clarified what role business associates have in reporting breaches of PHI. The new rule also requires covered entities and business associates to develop policies and procedures, train workforce members regarding the new breach provisions, and to implement reasonable systems for discovering breaches of unsecured PHI. Entities can now submit breach reports to HHS online at http://transparency.cit.nih.gov/breach/index.cfm .
The HHS rule became effective on Sept. 23, 2009. However, the Secretary of HHS has delayed enforcement of the new regulations until Feb. 22, 2010 to give entities time to implement procedures necessary to comply with the new rule.
ANALYSIS OF THE NEW BREACH RULES
I. The Definition of "Breach"
The Breach Rule expands upon the HITECH Act's definition of the term "breach," creating a threepart test for determining whether a breach has occurred.
Step 1: Was There a Violation of the Privacy Rule?
Under the Breach Rule, a "breach" is defined as: "the acquisition, access, use, or disclosure of protected health information in a manner not permitted [by the HIPAA Privacy Rules] which compromises the security or privacy of the protected health information." This definition clarifies that a use or disclosure of PHI is not considered a breach unless such use or disclosure violates the HIPAA Privacy Rules. For example, a disclosure of PHI that is incident to an otherwise permissible use or disclosure, which occurs despite reasonable safeguards and proper minimum necessary procedures, would not be a violation of the Privacy Rule and, thus would not qualify as a breach. A violation of the HIPAA Security rule does not, per se, constitute a breach.
However, if a violation of the Security Rule results in the use or disclosure of PHI that is not allowed under the Privacy Rule, such use or disclosure may fall within the definition of a breach.
Step 2: Was There Harm to the Individual?
The Breach Rule distinguishes between harmless or harmful disclosures. A disclosure does not qualify as a breach unless it causes some harm to the individual. To qualify as a breach, the harm must pose "a significant risk of financial, reputational, or other harm to the individual." Covered entities and business associates will need to perform a risk assessment to determine if there is a significant risk of harm to the individual as a result of the impermissible use or disclosure of PHI. HHS lists several factors to consider in performing the risk assessment:
- Who made the impermissible use or to whom was the PHI impermissibly disclosed?
- Did the covered entity take immediate steps to mitigate an impermissible use or disclosure?
- Was the impermissibly disclosed PHI was returned prior to access for an improper purpose?
- What type and how much PHI was involved?
For example, a covered entity may obtain a written confidentiality agreement with the recipient that the information will be destroyed or not further used or disclosed. According to HHS, if such an agreement eliminates or reduces the risk of harm to the individual to a less than "significant risk," the security and privacy of the information has not been compromised, and therefore, no "breach" has occurred. HHS also indicated that impermissible uses or disclosures of limited data sets that include dates of birth and zip code identifiers may cause a pose a risk of significant harm, while limited data sets that do not contain birth dates or zip codes may pose less of a threat and therefore may not trigger a breach if used or disclosed impermissibly.
Step 3: Is there an exception?
The Breach Rule contains three exceptions to the definition of breach. The first exception provides that an unintentional acquisition, access, or use of PHI by a workforce member or person acting under the authority of a covered entity or business associate, if done in good faith and within the scope of authority, and which does not result in further use or disclosure in a manner not permitted under the Privacy Rule, is not a breach. "Workforce member" is defined under the HIPAA regulations to include employees, volunteers, trainees, and other persons whose conduct, in the performance of work for a covered entity, is under the direct control of such entity, whether or not they are paid by the covered entity.
Under the second exception any inadvertent disclosure by a person authorized to access the PHI at a covered entity or business associate to another person authorized to access the PHI at the same covered entity or business associate, or organized health care arrangement (OHCA) in which the covered entity participates, and the PHI is not further used or disclosed in a manner not permitted under the Privacy Rule. This exception essentially provides some flexibility to the minimum necessity standard and does not require reporting of uses or disclosures within an entity, business associate, or OHCA.
A third exception provides that any disclosure in which a covered entity or business associate has a good faith belief that an unauthorized person to whom the disclosure was made would not reasonably have been able to retain such information.
The three-part test to determine whether a breach has occurred can be summarized as follows:
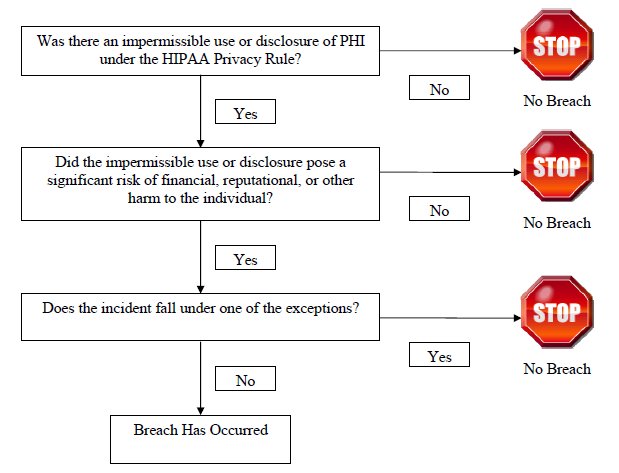
II. Unsecured Protected Health Information
The HITECH Act only requires notification when there has been a breach of "Unsecured PHI," which is defined as PHI "that is not secured through the use of a technology or methodology specified by the Secretary." The HITECH Act requires that HHS specify the technologies and methodologies that render PHI unusable, unreadable, or indecipherable to unauthorized individuals. The Breach Rule provides this additional clarification. It defines "Unsecured PHI" to mean PHI that is not rendered unusable, unreadable, or indecipherable to unauthorized individuals through the use of a technology or methodology specified by the Secretary in guidance.
This reference relates back to the guidance issued by HHS on April 27, 2009 (Technology Guidance), which specified encryption and destruction as the technologies and methodologies for rendering PHI "secured"; i.e. unusable, unreadable, or indecipherable to unauthorized individuals.
It is important to recognize that HHS's Technology Guidance on secured/unsecured PHI does not modify a covered entity's requirements under the HIPAA Security Rule. Currently, the Security Rule does not require encryption. Therefore, if a covered entity chooses to encrypt PHI in accordance with the Technology Guidance as a way to comply with the Security Rule, and the covered entity subsequently discovers a breach of that encrypted information, the covered entity will not be required to provide notification, even if there is a breach, because the information is not considered "unsecured PHI." On the other hand, if a covered entity uses a method other than encryption, or uses an encryption algorithm that is not specified in the Technology Guidance, then although that covered entity may be in compliance with the Security Rule, if there is a breach of the PHI, the covered entity would have to provide breach notification to the affected individuals.
HHS also clarifies several terms used in its Technology Guidance. The term "data in motion" includes data that is moving through a network, including wireless transmission, whether by e-mail or structured electronic interchange, while "data at rest" includes data that resides in databases, file systems, flash drives, memory, and any other structured storage method. "Data in use" includes data in the process of being created, retrieved, updated, or deleted, and "data disposed" includes discarded paper records or recycled electronic media. HHS also clarified that covered entities and business associates should keep encryption keys on a separate device from the data that they encrypt or decrypt.
HHS specifically rejected redaction as an accepted alternative method to secure paper-based PHI. As a result, if paper documents are lost or stolen, are not redacted appropriately, and include PHI, the covered entity will likely be required to follow the notification requirements.
III. Notification Requirements
Notification to Individuals
The HITECH Act requires a covered entity to notify each individual when the covered entity discovers or reasonably believes there has been a breach of unsecured PHI. The Breach Rule clarifies that a covered entity is deemed to have knowledge of a breach if such breach is known, or if by exercising reasonable diligence, the breach would have been known to any person who is a workforce member or agent of the covered entity, other than the person committing the breach. The federal common law of agency controls in determining who is an agent of the covered entity.
HHS explained that "reasonable diligence" means the "business care and prudence expected from a person seeking to satisfy a legal requirement under similar circumstances." Therefore, HHS expects covered entities and business associates to implement reasonable systems for discovery of breaches. Because knowledge of a workforce member or agents such as a business associate will be imputed to the covered entity, covered entities should adequately train their workforce and agents to timely report impermissible uses or disclosures of PHI.
Notice is to be provided to the individual without unreasonable delay, and in no case later than 60 calendar days following discovery of the breach. The time for notification must be calculated beginning on the date that the breach is first discovered, not on the date that that a covered entity has completed an investigation of a possible breach.
The Breach Rule mirrors the HITECH Act with respect to the contents of the notice required:
- A brief description of what happened, including the date of the breach and the date of the discovery of the breach, if known;
- A description of the types of unsecured PHI involved in the breach;
- Any steps individuals should take to protect themselves from potential harm resulting from the breach;
- A brief description of the covered entity's actions to investigate the breach, mitigate harm to individuals, and protect against any further breaches; and
- Contact procedures for individuals to ask questions or learn additional information, which must include a toll-free telephone number, an e-mail address, web site, or postal address.
The HHS comments indicate that in providing notice, covered entities may be obligated to comply with other laws, such as Title VI of the Civil Rights Act of 1964 and the Americans with Disabilities Act, which could include providing the notice in languages other than English or alternate formats such as large print or Braille.
The HITECH Act includes provisions for actual and substitute notice to the individual. The Breach Rule adopted this statutory language and requires a covered entity to provide notice in written form by firstclass mail to the last known address of the individual or by electronic mail, if the individual agrees to receive electronic notice, and such agreement has not been withdrawn. HHS also clarified that if the affected individual is a minor or otherwise lacks legal capacity, the covered entity may send notice to the individual's personal representative. If the individual is deceased, notice must be sent to next of kin only if the covered entity knows the individual is deceased and has the address of the decedent's next of kin or personal representative. The covered entity is not required to obtain the deceased's contact information if it does not have the information at the time of the breach.
If the covered entity does not have sufficient contact information for some or all individuals, substitute notice must be provided. If there are fewer than ten individuals involved, the covered entity may provide substitute notice through an alternative form of written notice, such as electronic mail (even if the individual has not specifically agreed to electronic notice) or by telephone or other means. If the covered entity lacks any current contact information for the individuals, posting such notice on the internet may be appropriate, as long as the posting is done in a manner that is reasonably calculated to reach the individuals.
If a covered entity has insufficient or out of date information for ten or more individuals, then substitute notice must be provided through a conspicuous positing on the home page of its website or conspicuous notice in major print or broadcast media, for a period of 90 days. The substitute notice must be provided in a manner that is reasonably calculated to reach the affected individuals. HHS interprets the term "home page" to include the home page for visitors to the covered entity's website and the landing page or login page for existing account holders, or a hyperlink on the entity's home page that links to the substitute notice. In addition, the substitute notice provision requires the covered entity to have a toll-free phone number for 90 days so individuals can obtain more information about the breach.
Notification to the Media
If a breach of unsecured PHI involves more than 500 residents of a state or jurisdiction, the HITECH Act requires a covered entity to provide notice to a prominent media outlet in addition to providing the individual notice described above. HHS expects that most covered entities will provide notice to the media under this section in the form of a press release. However, a press release will only satisfy the substitute individual notice requirement if the press release is actually run by the media outlet.
In the Breach Rule, HHS clarified that the term "jurisdiction" is a geographic area smaller than a state, such as a county or town. HHS declined to define "prominent media outlet" and stated that what constitutes a prominent media outlet will differ depending on the state or jurisdiction affected. For example, if a breach affected individuals across an entire state, the appropriate media may be a major, general interest newspaper with daily circulation throughout the state. On the other hand, if the breach involved only individuals in the same city, the appropriate media may be a general interest newspaper with daily circulation throughout the city.
Notification to HHS
The HITECH Act requires a covered entity to notify HHS "immediately" if there is a breach of unsecured PHI involving 500 or more individuals. HHS interprets the term "immediately" to mean that a covered entity should send notice to HHS concurrently with the notification sent to an individual (without unreasonable delay but in no case later than 60 calendar days following discovery of a breach). The HHS notification requirement differs from the media notification requirement. A covered entity must notify HHS of breaches involving 500 or more individuals, even if the 500 individuals were not located in the same state or jurisdiction. For example, if a covered entity discovers a breach involving 300 Maryland residents and 300 District of Columbia residents, notification must be provided to the individuals and concurrently to HHS, but not to the media.
The HITECH Act requires covered entities to maintain a log of all breaches involving less than 500 individuals, and to submit the log to HHS on an annual basis. HHS has specified that the annual report must be submitted to HHS no later than 60 days after the end of each calendar year.
In addition, pursuant to the HIPAA Privacy Rule, covered entities must maintain the log or other documentation for six years. The Breach Rule also provides that the notification to HHS must be submitted in a manner to be specified on the HHS web site. HHS has also noted that for calendar year 2009, the covered entity is only required to submit information to HHS for breaches that occur after Sept. 23, 2009, the effective date of the regulation.
In October 2009 HHS established a new Web site that permits online reporting of breaches to HHS. Breaches may be reported at http://transparency.cit.nih.gov/breach/index.cfm .
IV. Business Associates
Under the HITECH Act, when a business associate discovers a breach of Unsecured PHI, the business associate must notify the covered entity so the covered entity can notify affected individuals. The Breach Rule clarifies that if a business associate maintains PHI for multiple covered entities, the business associate only needs to notify a covered entity regarding the relevant breaches. However, if the business associate cannot determine which covered entities were included in the breach, the business associate may need to notify all potential covered entities.
The Breach Rule clarifies that a breach shall be treated as discovered by a business associate on the first day on which the breach is known to the business associate, or would have been known to the business associate by exercising reasonable diligence. Like covered entities, business associates are assumed to have the knowledge of their employees, officers, or other agents. Thus, business associates, like covered entities, should establish policies and procedures and train their personnel to report impermissible uses and disclosures.
Generally, a business associate must provide notice to the covered entity without unreasonable delay, and in no case later than 60 days following discovery of a breach. If a business associate is acting as an agent of a covered entity, the business associate's discovery of the breach will be imputed to the covered entity. Accordingly, the covered entity must provide notification based on the time the business associate discovers the breach, not from the time the business associate notifies the covered entity. On the other hand, if the business associate is an independent contractor of the covered entity, the covered entity must provide notice based on the time that the business associate notifies the covered entity of the breach.
In the Breach Rule, HHS recognized that business associates may not be able to provide the identity of each individual whose unsecured PHI was breached. Therefore, the rule indicates that such identification must be provided to the covered entity "to the extent possible." The Breach Rule also requires the business associate to provide the covered entity with any other available information that the covered entity is required to include in the notification to the individual. HHS emphasized that a business associate should not delay the initial notification to the covered entity in order to collect information needed for notification to the individual.
HHS specifically noted in its comments that the Breach Rule is not intended to interfere with the relationships between business associates and covered entities, and that both entities will continue to have the flexibility to determine their respective obligations. HHS encouraged the parties to consider which entity is in the best position to provide notice to the individual, depending on the circumstances of the relationship.
V. Administrative Requirements and Burden of Proof
The Breach Rule requires covered entities to comply with the administrative requirements of the Privacy Rule with respect to the breach notification requirements. This means that covered entities and business associates must develop and document policies and procedures, train workforce members, and impose sanctions for failure to comply with the breach notification procedures. In addition, when a covered entity or business associate knows of an impermissible use or disclosure of PHI, it should maintain documentation that all required notifications were made, or, alternatively, that it conducted the three-part test and determined there was not a breach.
Preemption
HIPAA preempts contrary state law, with certain exceptions. HHS indicates in the interim final rule that such exceptions do not apply to the breach notification regulations. Therefore, contrary state law will be preempted by the breach notification regulations.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


