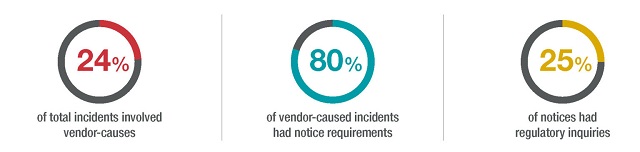
As reflected in our 2021 Data Security Incident Response Report 2020 saw a sharp spike in the number of incidents involving vendors, which amounted to over 25 percent of the total incidents handled in 2020, and the trend is continuing well into 2021. This spike resulted from companies' increased reliance on vendors to carry out tasks involving personal information, along with an increased focus by threat actors on such high-value targets. Vendor incidents involved entities in all industry segments but were particularly pronounced in the education and healthcare sectors.

Vendor incidents involved phishing schemes and inadvertent disclosures but primarily resulted from ransomware attacks. These ransomware attacks typically involve malware that spreads from the vendor to the customer's environment by utilizing the vendor's own credentials or the theft of customer data from a vendor's environment - a continuation of the general rise of ransomware extortion that BakerHostetler saw throughout the year. In some ransomware attacks, if a vendor did not pay the ransom, a threat actor would contact the vendor's clients to disclose what data was taken.
Key lessons to be learned from vendor incidents
Timeline from discovery to client notification. The amount of time it takes vendors to notify their customers of an incident varies greatly from a few days to several months after discovery. For the more than 200 incidents caused by vendors that BakerHostetler worked on in 2020, the median time to client notification was 160 days, though the timelines varied widely across matters. Some clients were notified by their vendors within only a few days, particularly where there was a contractual obligation to notify. In many incidents, the initial notice provided by the vendor was incomplete or inaccurate, requiring customers to repeat or expand their assessment of notification obligations.
Vendor vetting is more important than ever. Before engaging new vendors that will be given access to their environment or data, companies must properly vet them to make sure that they have the proper technical and security safeguards in place and that they practice good data hygiene. Not only will proper vetting potentially reduce the likelihood of a data security incident, but it could help protect the company in data breach litigation where the plaintiffs allege that the company was negligent in its choice of vendor. Some vendor types - such as in accounting, legal services and government - are prone to have personal information without their clients realizing the risk.
Contractual terms and conditions matter. When a vendor experiences an incident that involves thousands of clients, the language in the vendor contracts will be critical to dictating what those clients' rights are. During 2020, we saw significant variance in the services and compensation offered by vendors, depending on their contractual obligations. Vendor contracts should include obligations to notify the customer and set out clearly the vendor's liability for a breach.
Understand what data is collected and with whom it is shared. Many of the clients whose vendors had data security incidents were unaware of the nature and scope of the data that they had shared with their vendors. To avoid situations like this, companies need to understand what data is being collected, by whom and for what purposes; how that data is being stored and for how long; and which vendors have access to that data and through what means.
Limit the amount of and access to personal information. Some clients that experienced vendor incidents found they had notification obligations for information that was not needed by the vendor. As with internal policies and procedures, the amount of personal information provided to vendors should be narrowly tailored to only what is required for their services. Vendor access to a client environment should also be limited - or even excluded if unnecessary to their services.
Ongoing due diligence of vendors is critical. Vendor vetting cannot stop at engagement. To help prevent an incident involving their data, it is essential that companies continue to monitor their vendors to ensure that vendors are implementing the proper safeguards to protect companies' data and systems. Ensure that vendors that have access to a company environment do so through credentials unique to the company that are protected through multifactor requirements and secure connections.
Beware of fourth-party risk. When companies engage professional services firms such as accounting or law firms, it is also important to understand how data will be transmitted to the firms and how that data will be stored, as those firms engage vendors for data management systems, which could also experience data security incidents.
Regulators will still investigate, even if the incident occurred at a vendor. While regulators will often focus primarily on the vendor that experienced the incident, they can and will also investigate a vendor's customers, most often with regard to the notification timeline and the sufficiency of control the customer had over the vendor's security measures. Forty-four of 321 vendor-caused incidents in 2020 had regulatory inquiries, most predominately from the Office for Civil Rights and state attorneys general.
Work with knowledgeable attorneys. Experience is crucial when it comes to incident response matters. BakerHostetler clients that experienced vendor data security incidents that involved multiple companies benefited significantly from both BakerHostetler's incident response expertise and from the information we gathered from working with other clients involved in the same incident.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

