PREFACE
Consultants, technology firms, and analysts have long been known for producing annual detail-by-detail lists of technology trends that will change the world, usually with "space age" glimpses of a magical new future. We have a different take – with an agenda designed to help CIOs in their efforts to solve their most pressing business problems.
This report shares the technology trends we see as relevant for 2010, clustered in two categories: Emerging Enablers and Disruptive Deployments. Emerging Enablers are core disciplines that have evolved within organisations – capabilities, skills, and philosophies that are critical for IT and the business to partner, innovate, and create more value. Most, if not all, CIOs will have addressed these topics in the past – perhaps multiple times. We think that they deserve another look this year due to specific factors in the technology and/or the business environment. Disruptive Deployments are trends that present significant new opportunities – offering new business models or transformative ways to operate in existing markets. The technologies individually may not be disruptive, but deployed as discussed, they may positively disrupt the cost, capabilities, or even the core operating model of IT and the business.
All these trends are relevant today, though some have not reached maturity. Each has demonstrated momentum and potential for impact – and we believe each is important enough to warrant immediate consideration. Forward-thinking organisations should consider developing an explicit strategy in each area, even if that strategy is to wait and see.
Depth Perception goes beyond headlines and broad definitions to a detailed look at new technology opportunities – how we got here, where we believe we're going, and what we think it means. Each topic follows the same formula. The introduction, "where to start," and "bottom line" sections of each topic should be beneficial to all audiences. Non-technologists may want to skim "history repeating itself" – and skip over the "technology implications."
But whatever you do, don't sit on the sidelines and wait for any of these trends to shape your business. Stay in control, and use them to your advantage. The future starts today.
For more information visit:
www.deloitte.com/us/2010technologytrends
www.deloitte.co.uk/technologyintegration
EMERGING ENABLERS
1. INFORMATION MANAGEMENT FINALLY GOES ENTERPRISE
Leaders Expect Confident Answers to Fundamental Business Questions. Step One is the Right Foundation.
Information is the heart of the business of IT. It's right there in the name. But the CIO doesn't own the information – the business does. IT is the caretaker – responsible for enablement, compliance, governance, protection, and optimisation. Years of investment and growing complexity of the underlying technology landscape have led to islands of business automation – which in turn have produced islands of information. The inability of most organisations to manage this complexity has created frustrations, as IT has been unable to confidently answer seemingly simple business questions. These questions range from tactical operational concerns to broader cross organisation and geography challenges. What do I ship to a specific customer location? How many items do I really sell in this category? What is the profitability of a given customer across lines of business? How much do I spend with a given supplier? How does a product perform across the globe?
Information management represents the collection of disciplines needed to help answer these kinds of questions – to control the information chaos and ready the playing field for the future. The scope can seem daunting: Managing the dimensions and lifecycles of data and information – including a strategy for measuring, monitoring, and controlling. Managing information quality, visibility, searching, semantics, structure, master data, privacy, federation, retention, and security. Ongoing processes and governance bodies for maintenance, stewardship, and controls.
The real trend is not the individual domains. In fact, we believe it is only by stepping away from these point solutions that you'll find the answer. Enterprise Information Management (EIM) is about developing an overall view of the dimensions of the challenge – then marrying tools and techniques with governance disciplines and changing business behaviour. Instead of being thought of as a technology tool, effective EIM embeds information quality and management into everyone's job description. Information management shifts from a back-office responsibility of skilled data analysts to an organic part of how business gets done at the point of business impact. Once an organisation's information management has gone enterprise, it finally has the opportunity to leverage information as the strategic asset it really is.
History Repeating Itself?
Various waves of information solutions have taken shape over the previous decades. While value has been created in silos, the overarching challenge of truly enterprise information remains.

Technology Implications
Business process revisions, organisational change management, behaviour/culture shifts, and overall business alignment represent the majority of the challenge. There are also key technology considerations that need to be addressed:

Where Do You Start?
EIM initiatives can easily turn into complex, technology-driven affairs – overwhelming in scope and delivering little tangible value. Some organisations have created value by implementing individual components, but it doesn't get them where they need to be.
The organisations most successful at implementing EIM have taken a bottom-up approach rooted in addressing their business problems – building out master data management, information quality, and process management capabilities through initiatives focused on specific business areas, such as customer care or supplier spend analysis. This can identify pain points with the opportunity for real value creation – while building out the foundational components of EIM.
Regardless of the function or process area initially targeted, based on our experience, successful EIM programmes share a number of characteristics. These include:
- Partnering with the business to become a change proponent as a part of an enterprise initiative. "Information management for the sake of information management" won't get the traction needed as a standalone effort.
- Creating a discipline and a culture around information quality – embedded in day-to-day operations with incentives.
- Taking a value-based, pragmatic approach to technology investments – in line with the magnitude of expected results.
- Identifying the incremental steps that will move them towards simplification and better governance – not large-scale transformation.
- An understanding of the assets that the organisation has – infrastructure, tools, people, and skills – as well as the actual business goals to rationalise the approach and achieve buy-in and support.
EIM is a long journey for 2010 – and beyond. The EIM leaders will be those who develop a strategic plan for EIM and take measured steps to improve their capabilities. Companies that over complicate their goals or wait for the next technology-based silver bullet will likely fail to generate business value or fall behind their competitors who take the path of step-wise improvement.
The concern for the long-term health of information management is not something new, and it's certainly not something that should lose priority anytime soon. Ignoring it will only make it worse.
|
Bottom line Master data cannot be isolated from business intelligence. Data conversion cannot be left to the devices of each individual project. And business units cannot be individually left to answer their "what do I need to know?" questions with whatever information they have at their disposal. The individual repositories of data and the supporting functions within an organisation are all reflections of the same fundamental source: The underlying dayto- day activity and health of your business. As data volumes continue to proliferate and stakeholders become more demanding, we believe owning the information space will shift from being a competitive differentiator to being a mandate for competitive parity, especially as businesses continue to rely on business partners and third-party operating models (think cloud computing) for pieces of their value chain. But either way, enterprise information management will be a key part of IT's responsibility – and one that organisations can no longer afford to treat as a collection of tactical concerns. |
As data volumes continue to proliferate and stakeholders become more demanding, we believe owning the information space will shift from being a competitive differentiator to being a mandate for competitive parity, especially as businesses continue to rely on business partners and third-party operating models (think cloud computing) for pieces of their value chain. But either way, enterprise information management will be a key part of IT's responsibility – and one that organisations can no longer afford to treat as a collection of tactical concerns.
2. CIO OPERATIONAL EXCELLENCE – BUILT TO RUN
Improving the "Business of IT" by Planning for the End-Game from Day One
The global financial crisis had a direct impact on a number of IT trends in 2009. With most IT budgets either slashed or stagnant, and an increased focus on cost reduction opportunities, IT operational excellence became top of mind for many organisations. Revisiting the basics in terms of process effectiveness and overall efficiency of the "business of IT," was one approach many organisations used to drive quick hits across the cost-cutting spectrum.
Post go-live concerns have become a strategic CIO topic in IT planning, design, implementation, and operations. Operational considerations – from enabling agility to optimising efficiency – are moving from project afterthoughts to key drivers for delivering on business goals.
"Built to run" now involves the full spectrum of CIO responsibilities:
- IT organisational issues such as formal IT and business alignment.
- Mature and robust requirements, risk, quality, and testing management.
- IT delivery model disciplines such as CMMI engineering principles, investments in tools, and processes.
- IT service management and ITIL, Green IT, and sustainability.
Forward-thinking organisations realise that these initiatives can strategically reposition their IT operational spend. Embodied by enterprise efforts like Green IT and IT Services Management, operational implications are starting to move from project after thoughts to disciplines embedded across the IT delivery model. Work is being expressed as IT services, with costs translated in business terms to IT's customers.
This "built to run" mandate affects every stage in the IT lifecycle – planning, requirements, design, build, test, and operate. In fact, many improvements are based on better understanding the touch-points and dependencies between activities along the lifecycle. Disciplined methods and tools can reduce the amount of effort required to return a desired result, while driving feedback for continuous improvement. Projects are balancing post go-live considerations with their expected business results, helping create more predictable and stable ongoing maintenance and management.
"Begin with the end in mind" has been a popular expression since it was first introduced by Stephen Covey in The 7 Habits of Highly Effective People. Now, more than ever, this approach is helping to drive IT operational excellence. Overall support expenses are being reduced by efficiency gains – allowing IT funds to be redirected towards strategic initiatives that create more value for the business. By providing clarity around the nature, cost, and expectations of services provided by IT, significant improvement are being made around business and IT alignment. The CIO supports the business of the business. Operational excellence addresses the business of IT. And it's up to the CIO to make sure IT is built to run.
History Repeating Itself?
Ever since information technology was adopted by businesses in the 1960s, the delivery and maintenance of IT has been a critical operational concern. Understanding the current focus on CIO operational excellence requires a view of previous attempts to improve the business of IT.
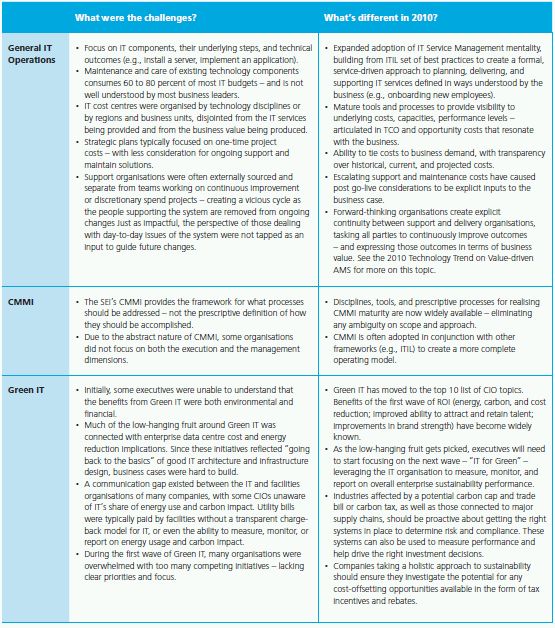
Technology Implications
CIO operational excellence requires a collection of process, people, and technology capabilities. The technology implications are listed below, but cannot be addressed without making simultaneous advances in disciplined governance, organisational and process considerations.

Where Do You Start?
The different dimensions of CIO operational excellence provide some flexibility about where to start. Individual initiatives should take steps towards embedding the "built to run" philosophy as a part of the muscle memory of the IT function. First, make sure any incremental movement across IT operations, IT organisational design, sustainability, or project/requirements/testing management is done with the overarching vision in mind. Effective best practices to consider as you proceed include:
- Focus on the Ends of the IT Lifecycle. It is tempting to immediately focus on the perceived core functions of IT – build and break-fix. But for most IT shops, the real bottlenecks are up and down stream. Upstream includes planning, demand/capacity management, requirements, and scoping/design improvements. Downstream involves quick hits in Green IT and improving lower-level IT service management. These have the potential to lower total cost of ownership and percentage of IT spend dedicated to maintenance and management of existing IT.
- It's All About Requirements. Requirements are an excellent place to start – including high-level business requirements to guide investment decisions, high-level technical requirements to guide solution shaping, and detailed functional and technical requirements to accurately drive cost, effort, and timing. With disciplined involvement of the business and a focus on steady-state operational considerations from the outset, estimates can be more realistic and costly scope changes or can be reduced or avoided.
- IT Services, Not IT Components. Instituting IT Service Management has the potential to lower total cost of ownership and percentage of IT spend currently allocated to ongoing maintenance and management. Organisations should consider:
-
- Building a portfolio of IT services – a catalogue of capabilities IT provides to the business and to itself.
- Creating an IT cost baseline – identify IT spend as the business sees it today, across budgets, cost pools, and allocations.
- Building an integrated IT service model – covering the people, hardware, and software required to deliver each service and capability.
- Identifying areas for service and cost improvements – create a roadmap of efforts to drive efficiency gains.
- Optimise your Data Centre. Recent advances in virtualisation enable cloud architectures and allow dramatically re-envisioned IT asset requirements across computers, network, storage, applications, facilities, and operations layers. Simplifying the infrastructure can not only help ease operating complexity, but can generate quick wins for the organisation's Green IT efforts by reducing energy and carbon footprints.
- Understand the End Game. Achieving the
"built to run" vision should reach every stage of the IT
delivery lifecycle. By moving from the outside in, improvements
will be more tangible and significant at each step.
|
Bottom Line Individual IT operations decisions ranging from delivery model to cloud-based management can be greatly simplified by structuring the IT organisation according to a "built to run" perspective. By proactively considering ongoing management needs and defining all the implications, the full magnitude of an investment can be weighed at its onset – positioning the organisation to make more informed decision-making and to better prepare for the end-game from day one. The "built to run" concept intentionally covers a broad focus area from Green IT to running IT as a factory. The unifying thread is an up-front focus on ongoing management of an organisation's IT solutions, which should help to couple efficiency goals with broader business and corporate strategies. We use the term "management" as opposed to "maintenance," which is focused solely on technical break-fixes and upkeep. The difference is an important one, and is the heart of the "built to run" mandate. |
3. CYBER-SECURITY
Moving from Background Technology to a Priority Business Discipline
With intellectual property now fully convertible to ones and zeros, it was only a matter of time before defending enterprise information assets became a key concern. For too many years, security has been relegated to the technology agenda and accorded only marginal attention and budget by many organisations. Most perceived the threat to be containable, where a protect-the-perimeter approach was deemed sufficient. Responses were reactive, both to incidents and compliance requirements.
In 2010, the world has changed – and not for the better when it comes to threats. The threat landscape has grown due to proliferation of technology, global networks, and the sophistication of criminals. According to recent FBI studies, cyber-crime – with over $1 trillion in annual revenues – has outpaced drug trafficking as the largest illicit global business.1
The threats are not limited to strangers lurking outside the gates. People within an organisation's trusted circle – employees, customers, contractors, and partners – can bring risk as well, both through inadvertent mishandling of information or corruption. This insider risk is growing with the increasing use of insecure social media, phishing and spoofing, and worse. Employees can be preyed upon by well-organised cyber-criminals who thrive on stealing personal and corporate financial information. With the battleground for security and privacy moving inside an organisation's walls, a soft interior defence is no longer acceptable.
The implications of security risks have also transformed. No longer simply matters of fraud, the costs of responding to information breaches can be staggering. Between legal fees, customer communications, good-will spend, and public relations efforts, the hard cost can be significant. Just as important, consumer trust and the company's brand and reputation are at stake.
Today, cyber-security must embrace both security and privacy as foundational elements of the business. An effective Cyber Threat Intelligence (CTI) programme is systemic, well-funded, enterprise-wide, and championed in the C-suite. Cyber-security must be a central component of any enterprise risk management strategy, not just a technology responsibility.
History Repeating Itself?
Security is hardly a new concern for IT. Pieces of identity management and access control have been in place since the beginning of system design. But the ability to manage and protect the enterprise across resources and players has changed dramatically.

Technology Implications
While security and privacy are moving beyond the domain of technology, the foundation for any protection strategy still rests within IT. The individual solution components have been in place for some time in organisations, but they need to be leveraged as integrated, enterprise assets to protect against 2010's cyber-security challenges.
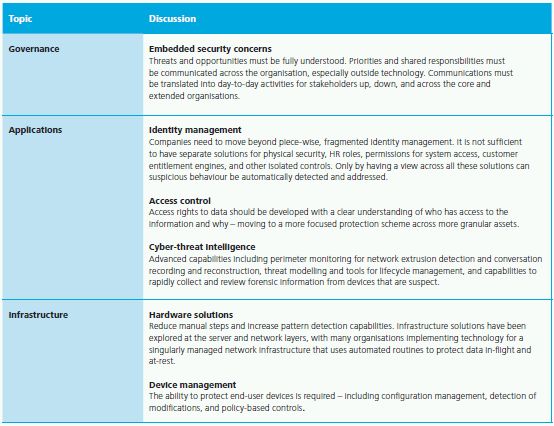
Where Do You Start?
Revamping enterprise cyber-security can seem like a daunting task. Luckily, there are ways to improve without unleashing a tsunami of change. Here are some simple steps to consider as you get started.
- Write the Business Case. The value of security must move beyond fear and doubt. Quantifying the potential implications is critical for making the shift from reactionary incident response to enabling new business and IT priorities. Frame security like this: "If we don't do X, we won't be able to do Y." That will help educate the organisation on the need for a new approach.
- Break the Misperception of Security as an IT Silo. Organisations that leave cyber-security as an IT concern will struggle with risk management. At a minimum, the CFO, CHRO, and business leads need to understand and support the business case. Some organisations have moved security into legal and enterprise risk, and some have it reporting into the CEO to reinforce its cross-discipline importance.
- Embrace Regulation, But Don't Use It as the Goal. Potential new standards could level the playing field – and help define a target for base-lining minimum response. Don't make that the end goal, but use it as an impetus to change behaviours.
- Reexamine the Role of the CISO/CSO. In many companies, this will require new organisational structures and skills from the chief security resource – and the need to reach-out across the extended enterprise.
- What You Don't Know Will Hurt You. Identify data at all areas of the value chain and develop a comprehensive risk profile. It's important to understand the value of an organisation's assets – especially how information is potentially monetised by cyber-criminals. Cyber-threat intelligence programmes include the creation of a cyber command centre and daily regimens to review and communicate emerging threat data, instituting two-way cross-industry intelligence sharing, and regimented threat briefings by line of business/delivery channel.
- First Things First. Without a robust identity,
credential, and access management strategy (ICAM), it is impossible
to protect the business. Look to automate wherever possible. Create
a repeatable, controls-based approach.
|
Bottom Line Cyber-security in 2010 is a forced necessity. The underlying idea hasn't changed much, but as threats have multiplied and become more complex, urgency has grown exponentially. The speed at which threats are evolving is outstripping enterprise security adoption – creating an imperative to protect company, customer, and partner information. After years of being asked to justify security's micro-level value to the business, the macro-level importance has become abundantly provable. Cyber-security can also play a role in growth; it is a key enabler for many technology-led innovations. Every one of the other 2010 Technology Trends has a direct dependency on a maturing cyber-security capability. From privacy controls between cloud providers and subscribers to managing access and entitlements across disparate user engagement channels, cyber-security is essential for any profitable future. Finally, remember this: Cyber-security is not a project with a beginning and an end point. It spans beyond the IT box, addressing enterprise risk across the business. It must become a part of the corporate genome through a sustained, disciplined approach. The mandate is clear. Business as usual is business at risk. Cyber-security is a discipline that can no longer be ignored. |
4. BEST-OF-BREED ENTERPRISE APPLICATIONS
Back to the ERP Future
Enterprise applications are enjoying a resurgence of sorts – but with a fresh focus on agility and innovation. The days of a single-stop behemoth package to fulfill all of a business' needs are fading fast. Instead, buyers are seeking to combine traditional packages for strategic standardisation in parts of the business, without compromising the ability to use best-of-breed solutions for selective differentiation. They're demanding the freedom to choose from legacy offerings, new custom capabilities, or other third-party products to satisfy their overall need for delivering results.
In 2010, companies are being driven by their own unique needs across business units and geographies, to explore alternatives to single global instances and universal process definitions. That's not to say global standard process definitions are obsolete – not at all. For record to report, procure to pay, or other mature process areas, they are just as important as ever. In fact, common processes and data in these areas can be a big part of the business case for enterprise transformation. But, it should not be the de facto answer – especially for organisations with complex structures operating across wide-ranging jurisdictions.
The vendors for commercial off-the-shelf (COTS) software have responded to this growing need. For example, they've been acquiring and developing competing modules within a single vendor's suite. They've also been developing and deploying sophisticated, service-driven integration capabilities. Finally, vendors are beginning to offer a hybrid approach to deployment – some parts licensed in the enterprise data centre, and other parts subscribed from cloud. This is important for two reasons. First, it allows buyers to split an enterprise application investment into smaller chunks – growing capabilities over time. And second, the focus of transformation efforts can more naturally be split between value creation and efficiency gains.
The efficiency of standardised COTS-based processes is well known. But the ability to innovate and drive incremental business value has not always been at the forefront when it comes to investments in packages like ERP. By enabling customers to innovate and customise their business capabilities, organisations adopting a best-of-breed enterprise application strategy are finding opportunities for true business transformation – met by a diversity of technical and operational solutions that make sense for their specific needs.
History Repeating Itself?
For organisations with a long history of ERP, any discussion of best-of-breed will feel like déjà vu. Way back when, things started with dedicated, discreet functional applications such as General Ledger, Accounts Receivable, Fixed Assets, and Inventory Control. This evolved to partially integrated systems such as Integrated Financials and MRP. As automation and integration continued to reach further across the business, companies adopted tightly integrated packages for ERP. Now the pendulum is swinging back to a collection of integrated, discreet functions or services. The difference today is in how they work together – within or across vendor suites – and the shared control frameworks that help maintain a consistent enterprise view of processes and information.

Technology Implications
Many of the critical needs for realising best-of-breed ERP fall outside the technology domain. Discipline and governance of the overall business and solution portfolio is essential. Most successful organisations name senior leaders as process owners – responsible not only for business capability and process definitions, but also for directing the supporting application footprint. That said, there are fundamental technology considerations that must also be addressed:
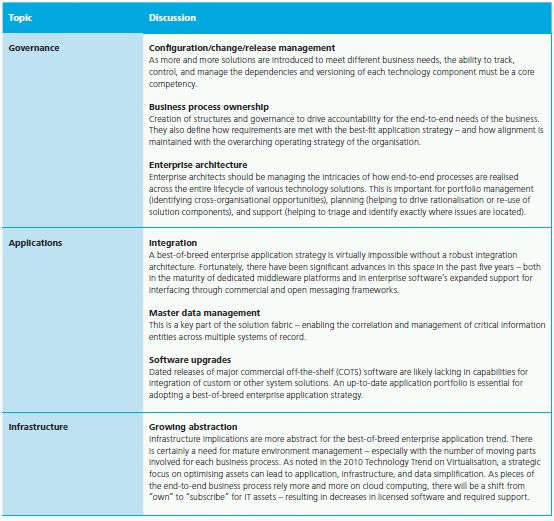
Where Do You Start?
Organisations can start the 2010 best-of-breed journey by taking stock of their current application footprint. Most companies will find themselves in one of two situations.
First is a "no vendor left behind" scenario – where years of investments have led to hundreds or thousands of solution piece parts that no one has the fortitude to inventory, much less try to fix. In this case, the best-of-breed approach is all about portfolio management. Focus on eliminating unnecessary uniqueness. Define strategic standards that rationalise and drive consolidation. Categorise assets by strategic disposition. Should it be sunset? Contained? Sustained? Grown? This assessment should not be defined just by technical underpinnings, but by how well applications can meet business needs. If you can't justify why something is unique, it should be targeted for retirement, consolidation, or replacement.
In the second situation, a large portion of an organisation's business processes are realised by a small suite of enterprise applications – either custom or package. The place to start here is by understanding where pain is being felt across the value chain. Areas where package constraints limit business capabilities or where differentiated functionality has been sacrificed in the name of standardisation form the basis of opportunity. Enhanced functionality in new versions of the software packages may come into play, as may new alternatives introduced since original scoping decisions were made. For custom solutions, advances in standards, patterns, and tools provide opportunities to simplify and extend functionality that was previously too complex or expensive. Organisations should investigate current offerings – both of existing licensed software and across the broader market. The cross section of areas with high business need and strong new potential functionality form the short-list of where to begin the best-of-breed enterprise applications journey.
The beauty of this trend is the ability to create a quick roadmap – with bite-sized iterative steps that lead to implementing pieces of functionality as subsets of the end-game solution. A multi-year programme implementing a behemoth system is no longer the only option. The 2010 Technology Trend on Services Thinking offers more insight into a capabilities-focused, services-oriented business architecture that is a powerful companion to this Best-of- Breed Enterprise Applications trend.
|
Bottom Line Many vendors like Oracle, SAP, and Salesforce.com have invested heavily in anticipation of the best-of-breed enterprise application revolution. Their efforts represent an entire technical stack focused on allowing any information or IT service asset to be used as part of an organisation's value chain – regardless of package or custom, internal or externally hosted. Many Software-as-a-Service (SaaS) vendors are building market segments based on the notion that a company's business needs can be met by a mixture of specialised solutions that are diversely sourced. As with most opportunities, the issue will not be the technology. It will be winning the hearts and minds of organisations to re-visit their enterprise application strategies and portfolios – and decide to revitalise those investments. From rationalisation to introducing innovative and differentiating piece-parts to the portfolio, there are huge opportunities ahead. The revolution is fully underway. |
5. WIRELESS AND MOBILITY
The Battleground for Innovation in the Untethered Enterprise
Mobility in the enterprise is going through a disruptive shift – precipitated by both technology and changing user demand. Ubiquitous wireless connectivity and capacity, powerful terminal devices, and a growing mobile application ecosystem lend themselves to previously unimaginable solutions.
Beyond laptops, Web books, and handhelds, the scope of what is considered a "terminal" device is expanding as more and different equipment is being connected to the network across the value chain. Smart power grids and meters can monitor real-time electricity usage by houses or businesses. Telematics in cars, for safety and security monitoring, automated service scheduling, and driver convenience – all delivered via the Internet. And even Asset Intelligence (another top trend), where real-world assets (e.g., shipping containers, shop-floor machinery, raw material pallets) can communicate events, execute rules, and automate countless tasks. Resources in the field now have access to the full suite of an organisation's IT solutions. They can capture information and provide feedback at the "point of business" like never before – serving the enterprise as sensor, signal, and actuator.
But device and infrastructure improvements are only the medium. The real impact comes from the ability to offer new business capabilities and to radically rethink business processes. Whether you're arming a mobile sales force with full visibility to customers and products, creating a hospital "trolley on wheels" for viewing medical records and images across patients, or automating cross-agency background checks from a police car during a traffic stop, organisations are creating innovative offerings with content and collaboration moving beyond the desktop.
Advances in mobile business scenarios are the most important part of this trend. They are the conduits for innovation, enabled by advances in devices, which then push the boundaries of existing infrastructure, leading to new rounds of advances. This has led to mobile application marketplaces and supporting ecosystems in a virtual supply chain of developers, publishers, store-fronts, and delivery systems – with an explosion of interest on both the consumer and supplier side. At Apple alone, there have been at least 115,000 apps downloaded more than three billion times – one billion in the last three months of 2009 alone.2 From Google and Microsoft, to Ford and Intel and beyond, many other players are offering similar capabilities. The "application" movement is also driving expectations inside companies to improve the capabilities being delivered to a global virtual workforce. It all adds up to wireless and mobility being one of the premier enabling 2010 Technology Trends.
History Repeating Itself?
The wireless revolution started in the 1990s – and has unfolded with starts and stops, fads, orphaned technology purchases, and outright failures. Many of the challenges presented below remain current in this highly complex, closed environment.

Technology Implications
Technology implications are large for enterprise customers, with the explosive growth in capabilities of the mobile Internet blurring traditional boundaries and creating new opportunities. Consider these fundamental technology issues that must be addressed:
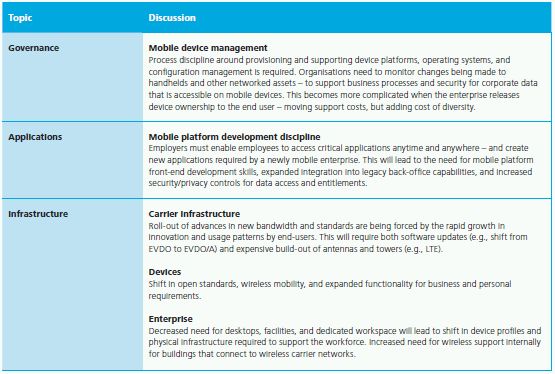
Where Do You Start?
We believe enterprise mobility will reshape the wireless value chain. Carrier operating models and infrastructure, handset devices, operating platforms, and software development are all likely to be affected.
But for most organisations, the greater impact will be the expanded importance of mobile solutions as part of their business operating model. Clearly defining the business requirements and user needs is the first step. That means determining the targeted use cases by identifying stakeholders that could benefit, the business scenarios that should be targeted, and the specific business process improvements and new capabilities that will be enabled. Specific questions to ask include:
- What business processes require – or could benefit from – interaction with employees, business partners, and/or customers away from their desktop?
- Where could these existing processes be improved by increased automation or access to information and services?
- How have competitors used wireless and mobile solutions? What are best practices across other industries that might be applicable to the organisation?
- What is the current technology footprint for different user types – including desktop, laptop, landline, handset, printers, voice/data plan, and other devices? Are all of these channels needed for typical day-to-day responsibilities? Are there opportunities for rationalisation?
- How can development communities or publically available solutions be leveraged – as point solutions or as inspiration for new solutions?
- What IT governance is in place today – and how can it be extended to mobile platforms?
- What is the organisation's enterprise vision –
and how does the wireless and mobility strategy align? Once the
scope and business scenarios have been defined, start making plans
to upgrade infrastructure and operations. The order is important:
Wireless and mobility must be understood in business terms
– and grounded in value related to real business
outcomes.
|
Bottom Line Too many companies think of wireless and mobility as plumbing – focusing only on infrastructure and the underlying technical challenges of security, privacy, platform standardisation, and legacy system integration. But we believe the real target should be the ability to drive business improvement, and that requires vision in scoping both tactical opportunities and boundary-pushing use cases. The business benefits are multi-faceted. There is a compelling story around IT cost reduction as end-user needs are more clearly understood and assets are simplified. However, soft gains around brand and customer loyalty also exist, especially as consumers demand innovation and broaden their usage of mobile devices. And there is the potential for making positive changes to daily business operations – allowing the business to tap talent wherever, whenever. Wireless is a fundamental enabler in Asset Intelligence (another top technology trend) – enabling non-traditional assets to play a role in the extended IT landscape as both sources of information and actuators of automated tasks. Wireless and mobility provides the foundation for innovation – we believe leaders in the next decade will be those who take advantage of it. |
6. VIRTUALISATION
How the Shift from Physical to Logical is Moving up the Value Chain – and Setting the Stage for a Potential (Cloud) Revolution
Virtualisation is in many ways a mature capability – with solid adoption across compute, storage, and network layers. It is not a top technology trend because it is new, but because its scope is growing across the stack and expanding to cover facilities, operations, and even business layers. Virtualisation is critical to many strategic goals of IT, including IT cost reduction, data centre consolidation, architecture rationalisation, and the migration from physical to logical that currently culminates in cloud computing. Few other emerging enablers have as much potential to help improve service management, reduce capital expense and ongoing costs, and positively affect every stage of the IT lifecycle.
The cost benefits of virtualisation are easy to understand. Reduced data centre footprint, optimised application instances, and shared computing resources allow companies to retire servers, redeploy system administrators, and reduce operating overhead. But other benefits are just as appealing. Virtualisation allows environments, applications, and data to be dynamically managed – enabling improved coverage and control of development and test environments for better quality assurance throughout project lifecycles. Data storage and structures can be revisited – removing redundancies, while introducing hierarchical storage to reduce spend on frames and spindles. And virtualisation promotes innovation – by providing elastic resources that can be borrowed or leased across the organisation based on business opportunity and demand.
The net result? IT is able to respond to business demand better, cheaper, and faster – and IT spend can shift from "keep the lights on" to driving outcomes meaningful to the business.
Virtualisation is also one of the technologies at the head of the cloud. A highly virtualised infrastructure is typically a first tactical step toward deployment of a cloud computing architecture – where "strategic" virtualisation allows fundamental changes to the business model, operating structure, and the way that business processes are enabled.
Multi-tenant stacks will become the norm in data centres, and a large portion of an organisation's IT assets may be virtualised in the cloud.
Virtualisation's impact is increasingly visible to end-users. Virtual desktops are finally gaining traction, allowing users to take their full machine configuration with them across locations and devices. Data virtualisation is becoming commonplace to make access available regardless of data or user location. Finally, there is the potential for virtualising at the workload level – load balancing and dynamically sharing CPU, memory, and storage resources. One hypervisor backing-up another, with automation tools able to shift workloads between resources. These are compelling possibilities for a concept more than 40-years-old – and exactly why virtualisation is a top technology trend for 2010.
History Repeating Itself?
The underlying technology of virtualisation is evolutionary in nature – representing decades of progress from the mainframe to minicomputers to Unix and distributed computing platforms. Foundational aspects of virtualisation can be traced back to the early days of the mainframe platform whereby virtual compute environments were first deployed.

Technology Implications
The use of virtualisation requires new approaches and technology architecture to fully realise the benefits and capabilities.

Where Do You Start?
Most organisations have made pointed investments in virtualisation, following a sound outside-in strategy through the non-production landscape and into non-critical applications. In 2010, we believe there will be a movement to consider higher-order virtualisation (operations, facilities, business functions) and core IT capabilities. From tactical storage virtualisation to strategic enterprise IT cost reduction, every virtualisation effort should consider the following order-of-operations:
- Simplify – eliminate unneeded diversity in environments, platforms, and applications.
- Standardise – establish reference architectures and play books for effective governance and delivery.
- Virtualise – get more logical per physical – compute, storage, network, facility, and operations layers.
- Automate – put technology to work in IT to reduce cost and error rates.
- Integrate – link people, processes, and technology for agility and scale.
- Innovate – SOA, Green IT, Web 3.0, cloud computing, ubiquitous access, and other business considerations.
- Repeat the cycle.
Aggressive virtualisation of the IT environment can reduce costs and increase effectiveness. It can also change the IT operating model. One example involves IT chargeback, where business and IT organisations can have different levels of virtualisation technologies deployed for servers, storage, and network. Each of these virtual platforms can be further broken down into smaller sets of services, such as CPU, memory, and data storage. Different levels have different chargeback models that will be deployed across organisations.
While technology challenges exist with virtualisation, we believe the bigger hurdles are organisational in nature. Strategies to provide support of virtual resources may require a realignment of technical resources and a fundamental shift in responsibilities. This is exacerbated by the need to shift mindsets around ownership and physical, dedicated devices. IT has been trained over decades that vertical integration of supporting infrastructure is the preferred model. The move towards logical IT services with leased or even "pay as you go" resources will require change management to get effective adoption. The C-suite should evaluate the benefits, costs, and risks of an organically enabled IT organisation that leverages virtualisation, cloud, and multi-tenancy capabilities – and whether those should be built in-house or sourced from a third-party vendor.
|
Bottom Line Virtualisation technology, specifically on the server, has become standard technology in the data centre. Data centres themselves are beginning to virtualise, morphing into cloud nodes with resource pools that span multiple sites, supporting on-demand computing needs and real-time failover. Every layer of computing resource is trending towards an aggregate consumption model – not managing individual servers, networks, and storage arrays. Organisations need to acknowledge all of the challenges introduced with virtualisation: Virtual environment sprawl, contentions over software licensing and chargeback models, impact on data centre resources, the need for improved change management techniques, requirements for incident management, and implications of security and regulatory compliance. That said, the benefits of a mature virtualisation base coupled with the promise of tomorrow's cloud-enabled vision should be more than worth the additional complexity. |
To read this report in full, please click here.
Footnotes
1.Cyber-crime Revenues Exceed $1Trillion Annually. (March 2009). Government Technology's Digital Communities. Retrieved from http://www.govtech.com/dc/628001
2. Jobs, Steve. "Apple's App Store Downloads Top Three Billion." Apple, Inc. January 10, 2010. Web. March 24, 2010. http://www.apple.com/pr/library/2010/01/05appstore.html.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

