In this article, we will briefly explore the increasing cybersecurity threat landscape, the various sources of threats, discuss the evolving regulatory environment and introduce some practical options that business leaders should be considering as they develop, enhance and refine their strategies to manage cybersecurity risks.
Over the last five years, cyber-attacks have become more sophisticated and increasingly coordinated. According to PwC's 2016 Global Economic Crime Survey, cybercrime jumped to the second most reported economic crime in 2015, with more than one in three organisations surveyed reporting being victimised by an economic crime. The financial services sector is a prime target and Cayman, along with the rest of the Caribbean should be acutely aware of the increasing threat.
Recently, there have been numerous news reports in Cayman of phishing and social engineering attempts aimed at customers across multiple industries. Businesses are evolving and are increasingly relying on connected technology and third-parties to meet customer expectations, deliver services and remain competitive in the market place. As a result, the number of target points for cyber threat actors is rapidly increasing and the potential points of weakness are becoming less obvious as connected infrastructures and use of third-party service providers proliferates.
Local and global regulators have taken notice and are actively introducing new regulatory measures to address the increasing risks. Financial services is the largest revenue generating industry in the local economy and is a prime target for cyber criminals. The Cayman Islands Monetary Authority (CIMA) is responding and announced the introduction of targeted cyber focused inspections for licensees in their May, 2016 Cybersecurity circular. Similarly, in January, 2016, the US Securities and Exchange Commission (SEC) announced cybersecurity as a top focus area for 2016 and beyond.
WHO ARE WE PROTECTING AGAINST?:
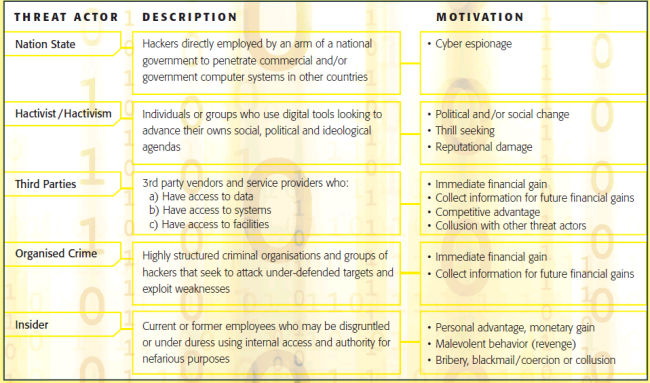
Broadly speaking, we define categories of threat actors that include: Nation States, Hactivist/Hactivism, Third- Parties, Organised Crime, Cyber Terrorists and Insiders.
The various threat actors have different motivations for their activities, which adds to the complexity of the problem and increases the need for comprehensive understanding of the risks at regional, industry, institutional and process levels.
PRACTICAL CONSIDERATIONS:
It's important to note that there is no one-size-fits-all solution for cybersecurity, and no silver-bullets.
Understand your current state, your risks and your assets
Consider performing an initial evaluation of where you are through a collaborative eff ort between IT and business. Identify and prioritise your "crown jewels" in order to determine the current risks and controls in place. On the technology side, consider performing assessments to determine if controls implemented follow leading practices. Ensure you are considering the end-to-end environment inclusive of all relevant third party providers.
Formulate a cyber-strategy and risk appetite
Once the current state has been established and the key assets identified, consider developing a cybersecurity strategy and define your appetite for cyber risk to help guide investment decisions and drive decision-making – it is important to understand what's at risk and how much can you lose to inform how much can you should be spending on protections.
Establish policy and governance
Establishing formal policies and procedures for managing cybersecurity and implementing a governance model with clear roles and responsibilities will enable more efficient and consistent decision-making. The responsibility for cyber risk is shared across the business, IT, Senior Management and the Board of Directors. It is critical to define the governance model to ensure you're able to proactively manage your infrastructure assets and to be able to respond to incidents. Many companies appoint a Chief Information Security Officer (CISO), who is responsible for providing direct oversight over the security function. CISO's generally have access to all parties in the governance framework and provide regular security updates to senior management and the Board of Directors. Integration is critical, cybersecurity should be considered as part of a broader operational risk framework that covers risks associated with people, processes, systems, data and external factors.
Adopt a framework
There are many industry accepted frameworks that can be leveraged and customised to your company's needs (e.g. NIST, COBIT5, ISO, COSO, etc.) The selection of a framework should be informed by your baseline assessment, risk appetite and governance model. Ensure that when implementing a framework you create linkages and integration with the governance model, risk appetite, strategic plan and the broader enterprise risk management functions. It is also important to consider the broader regulatory framework and environment to inform framework selection. For example, in a May 2016 Cybersecurity circular, CIMA indicated that they will be adopting the National Institutes Standards and Technology (NIST) cybersecurity framework.
Implement and monitor
The effectiveness of a cybersecurity framework and governance model is dependent on effective implementation and adoption. On-going monitoring and reporting provide management visibility into their cybersecurity risks and the effectiveness of their control environments. Consider providing targeted reporting to various stakeholder groups by defining and implementing Key Risk Indicators (KRI) and Key Performance Indicators (KPI) linked to business and operational objectives in alignment with a formal governance model. In addition to governance reporting, it is critical to monitor and report on cyber security incidents and threats to ensure both proactive management as well as effective incident response. Close the loop by learning from incidents and enhancing processes and framework elements as threats evolve and new threats emerge. Monitor internally as well as externally, there is a lot to be learned from incidents at other companies, and in other jurisdictions. Effectively monitoring your own end-to- end capabilities and external trends will create the greatest value.
IN SUMMARY:
Cyber criminals continue to become increasingly sophisticated and organised. Threats come in many forms with many underlying motivational factors. Increasing reliance on systems and interconnected infrastructure is driving the need for stronger controls and more formal management as threats emerge and evolve. Cybersecurity isn't just an IT issue, it's a business issue and everyone is a stakeholder. Multifaceted solutions that evolve to manage new threats will position you to weather the storm when it comes.
About the Authors
Isabel Gumeyi, CISA, CISM, ARM Isabel is a Senior Manager with PwC's Risk Assurance Group. She has over ten years of extensive experience assessing IT related risks, adding value to clients across various industries by providing advice on strategies to enhance their IT and business processes to address key risks and meet good practice standards. Her experience covers areas such as IT governance, Information Security and other IT general control considerations.
Assaad Sakha, CISM, CISSP, PCI-QSA Assaad is a Senior Manager with the Cyber Security practice at PwC. He has over twelve years of experience across various areas of Information and Cyber Security which includes security strategies, information protection, threat intelligence and vulnerability management, breach indicator assessments, digital identity and access management and compliance with various frameworks. Assaad has a number of cyber security publications including participating in the development of the ITU Toolkit for Cybercrime Legislation for United Nations Cybersecurity Programme in association with the American Bar Association's Privacy & Computer Crime Committee.
Robert Stanier, MBA Bob is a Partner with PwC Cayman Islands leading Risk Assurance services across the Caribbean region and Bermuda. Bob has more than 15 years of global executive level experience leading enterprise and operational risk organisations and engagements for some of the largest and most complex global companies in the fi nancial services, development fi nance and consumer and industrial products industries.
This content is for general information purposes only, and should not be used as a substitute for consultation with professional advisors. PwC refers to the Cayman Islands member firm, and may sometimes refer to the PwC network.
Each member firm is a separate legal entity. Please see www.pwc.com/structure for further details.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.




