1 Introduction
In today's digital world, many organisations collect and maintain data about their customers. Organisations are also outsourcing many of the costly components of their data storage and IT infrastructure to the "cloud". As they do so, are they ensuring compliance with data privacy laws and that their customers' data is appropriately secured, protected and managed?
Are organisations pushing critical business functions and customer data into the cloud, oblivious to the risks and paying little regard to its content, just to take advantage of reduced IT storage costs? In this move to the cloud, who in the organisation can attest to:
- what specific customer data has been collected?
- how is it used and by whom?
- the legal and regulatory requirements that apply to that data
- the accuracy of the data
Are organisations simply creating a data cloud or heading for a data storm?
With the increased sale of data between organisations, and the recent examples of accidental release of personal customer information by companies such as AAPT and Telstra (as discussed in this article), data privacy is an issue that must be taken seriously.
In part one of this article, Ronald Holtshausen from our Perth office considers the key risks regarding data privacy and the cloud, including the impact of recent amendments to the Australian Privacy Act.
Part Two of this article (which will be published in the following weeks) will discuss how data which is being stored in the cloud can be used in investigations or litigation.
Cloud computingCloud Computing is the practice of using a network of remote servers hosted on the Internet to store, manage, and process data, rather than using a local server or a personal computer. Through the use of cloud infrastructure, organisations are potentially able to:
|
2 Australian Data Privacy Laws
Breaches of the Privacy Act
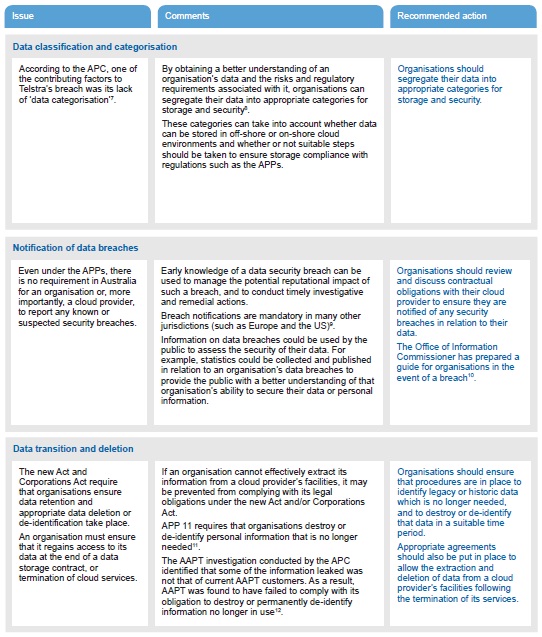
In 2012, following the release of various customers' personal information, including names, telephone numbers, birth dates, drivers licence numbers and even credit card details, both AAPT and Telstra were found by the Australian Privacy Commissioner ('APC') to have breached the Commonwealth Privacy Act 19881.
AAPT's release of personal information came as the result of the hacking of data held by AAPT's IT provider, while Telstra inadvertently made customers' personal data publicly available via a link on their website. In each case, an investigation conducted by the APC found inadequate security and controls around the management of personal information.
The APC made a number of recommendations to AAPT including:
- implementing regular training for staff in relation to data retention and destruction
- ensuring all IT applications are subject to vulnerability assessment and testing
- ensuring effective lifecycle management
- conducting regular audits of AAPT's IT security framework.
A further breach by Telstra occurred between February 2012 and May 2013, when the information of 15,775 Telstra customers from 2009 and earlier was accessible on the internet. In a report issued on 11 March 2014, the APC found that Telstra had:
- " failed to take reasonable steps to ensure the security of the personal information it held
- " failed to take reasonable steps to destroy or permanently de-identify the personal information it held
- " had disclosed personal information other than for a permitted purpose2.
However, under Australia's current privacy laws, the APC does not have the power to impose any penalties or seek enforceable undertakings from organisations investigated on its own initiative3.
New Privacy Principles
On 12 March 2014, the Privacy Amendment (Enhancing Privacy Protection) Act 2012 ("the new Act"), came into effect, which amends the Privacy Act 1988. The new Act introduces 13 Australian Privacy Principles ('APPs') which will replace the existing National Privacy Principles and Information Privacy Principles4.
Under the new Act, organisations will retain their responsibilities over their data (including sensitive customer information) when outsourcing IT infrastructure or data storage, including when they use remote or cloud infrastructure.
The new APPs require organisations to take reasonable steps to protect any personal information contained in their data and will regulate the handling of personal information by both Australian government agencies and businesses5.
New Penalties
Under the new Act, there will also be heavy consequences for those who get it wrong. Agencies and organisations can now be fined up to $1.7 million (or $340,000 for individuals) per breach6. This is on top of the reputational issues, and associated costs that may arise from such breaches.
These penalties underline that data protection and management must be taken seriously by organisations. We consider in the next section some key actions which organisations should take to protect their data in the cloud.
3 Better practice for organisations
In the context of the previous breaches of privacy laws and the introduction of the new APPs, we suggest the following key issues for organisations to consider when storing data in the cloud:
4 Conclusion
The APPs in the new Act go some way to helping organisations achieve good data management practices. However, we believe that the new Act has not gone far enough. We suggest that cloud providers and organisations that experience data breaches should be forced to disclose them to both the regulators and the affected parties (including customers). This would encourage people to assess who they give their data to, based on the data security performance of a particular organisation.
Organisations need to consider the qualitative aspects of data, and ensure the basics are in place to manage data. They must take data seriously. With the introduction of fines in the new APPs, and given the reputational damage that breaches cause, organisations should consider their data, and their customers' data, as a valuable asset (albeit one not recorded in their balance sheet), and act to protect it. Ignoring these risks and moving data to the cloud without adequate planning can produce negative outcomes which outweigh infrastructure savings very quickly.
Part Two of this article (which will be published in the next few weeks) will discuss how data which is stored in the cloud can be used as part of investigations or litigation.
Endnotes
1See article
http://www.oaic.gov.au/news-and-events/
media-releases/privacy-media-releases/aapt-breachedprivacy- act and
http://www.oaic.gov.au/news-and-events/
media-releases/privacy-media-releases/telstra-breachesprivacy-
act
2See
http://www.oaic.gov.au/news-and-events/mediareleases/
privacy-media-releases/telstra-breachesprivacy-
of-15-775-customers
3AAPT were also given a formal warning by the
Australian Communications and Media Authority (ACMA). http://
www.acma.gov.au/Industry/Telco/Reconnecting-thecustomer/
TCP-code/acma-issues-formal-warning-to-aapt. In March 2014, it was
reported that Telstra were fined $10,200 by AMAC.
4See article http://www.oaic.gov.au/news-and-events/
media-releases/privacy-media-releases/aapt-breachedprivacy-
act
5See
http://www.oaic.gov.au/privacy/privacy-act/privacylaw- reform
6See article
http://www.oaic.gov.au/privacy/privacyresources/
privacy-fact-sheets/other/privacy-fact-sheet-
17-australian-privacy-principlesSee http://www.oaic.gov.
au/news-and-events/media-releases/privacy-mediareleases/
aapt-breached-privacy-act
7See
http://www.oaic.gov.au/news-and-events/mediareleases/
privacy-media-releases/telstra-breachesprivacy- act
8For example, customer data should be identified and
marked for particular protection
9See article https://www.privacyassociation.org/
publications/eu_data_breach_notification_rule_the_key_
elements
10See http://www.oaic.gov.au/privacy/privacy-resources/
privacy-guides/data-breach-notification-a-guide-tohandling-
personal-information-security-breaches#_ Toc301281671
11See
http://www.comlaw.gov.au/Details/C2012A00197
12See
http://www.oaic.gov.au/news-and-events/mediareleases/
privacy-media-releases/aapt-breached-privacyact
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

