ACSC's 2016 Threat Report contains important cyber security insights for both Government and the private sector.
Certain sectors are at greater cyber risk, and the nature of the risks is evolving, according to the second Threat Report issued by the Australian Cyber Security Centre (ACSC).
Similar to last year's report, it also gives helpful mitigation and remediation advice for both Government and private sector organisations seeking to prevent, and respond to, cyber threats.
Types of malicious cyber activity
In the report ACSC shares its experiences of the various types of malicious cyber activity:
- cyber attack: the Australian Government has defined this narrowly as "a deliberate act through cyberspace to manipulate, disrupt, deny, degrade or destroy computers or networks, or the information resident on them, with the effect of seriously compromising national security, stability or economic prosperity". ACSC confirms that Australia has not been subjected to a cyber attack as defined, and a cyber attack against Australian Government or private networks by another state is unlikely within the next five years.
- cyber espionage: ACSC indicates that Australia continues to be a target of persistent and sophisticated cyber espionage. ACSC is aware of diverse state-based adversaries attempting cyber espionage against Australian systems to satisfy strategic, operational and commercial intelligence requirements.
- cybercrime: while the extent of cybercrime is a significant concern, ACSC notes that high levels of misreporting and underreporting make it difficult to assess accurately the prevalence and impact of cybercrime.
- cyber terrorism: ACSC considers that terrorist groups that seek to harm Western interests currently pose a low cyber threat. Terrorist cyber capabilities generally remain rudimentary and show few signs of improving significantly in the near future, and it is unlikely terrorists will be able to compromise a secure network and generate a significant disruptive or destructive effect for at least the next two to three years.
Threat to Government
ACSC reports that Australian Government networks are regularly targeted by the full breadth of cyber adversaries. Between 1 January 2015 and 30 June 2016, ASD, as part of the ACSC, responded to 1,095 cyber security incidents on government systems which were considered serious enough to warrant operational responses. On any view that is a significant number.
However, ACSC notes that as cyber security awareness and capability has increased, the number of incidents requiring an operational response has decreased, and ACSC expects to see this trend continue.
Threat to the private sector
ACSC acknowledges that its visibility of cyber security incidents affecting industry and critical infrastructure networks is heavily reliant on voluntary self-reporting, and that many cyber security incidents across the private sector are undetected or unreported.
Nevertheless, ACSC is making a dedicated effort to engage industry on cyber threats and associated mitigation strategies through a process of sustained engagement.
ACSC reports that between July 2015 and June 2016, CERT Australia - the Government contact point for cyber security issues affecting major Australian businesses - responded to 14,804 cyber security incidents affecting Australian businesses, 418 of which involved systems of national interest and critical infrastructure. ACSC provides a breakdown by sector:
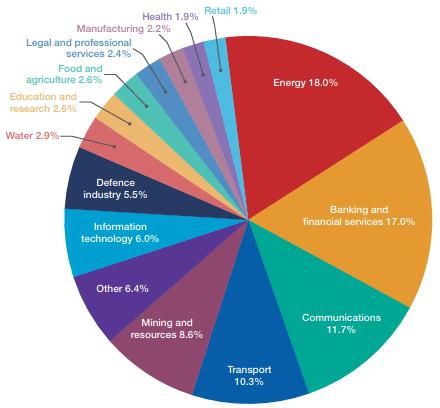
Source: ACSC 2016 Threat Report. Reproduced with
permission.
In CERT Australia's experience, the energy and communications sectors had the highest number of compromised systems, the banking and financial services and communications sectors had the highest incidence of DDoS activity, and the energy and mining/resources sectors had the highest number of malicious emails being received.
Trends in targeting and exploitation techniques
ACSC also reports on how the variants of malicious cyber activity are evolving. Among other insights:
- spear phishing: ACSC is aware of an increase in the prevalence of socially engineered emails designed to elicit company information, and adversaries are improving their social engineering techniques.
- ransomware: these campaigns are constantly changing and highly successful. They target a broad range of sectors including government, resources, business, educational institutions and home users. ACSC notes that the ransom has typically ranged from $500-$3,000 in bitcoins, however businesses have been hit with more targeting ransoms of tens of thousands of dollars.
- Microsoft Office macro security: adversaries are increasingly using Microsoft Office macros to circumvent security controls that prevent users from running untrusted applications. ACSC has seen an increasing number of attempts to compromise organisations using social engineering techniques and malicious Microsoft Office macros.
- DDoS extortion: ACSC reports that DDoS extortion against Australian businesses, including some of Australia's largest financial institutions, has increased. Over a three month period, CERT Australia received 15 reports of this activity from different companies.
What do you need to do
The Australian Government Information Security Manual requires Government agencies to report cyber security incidents to ASD. Equivalently, major businesses are encouraged to report cyber incidents to CERT Australia. However, as ACSC points out, when it comes to cyber security, prevention is better than a cure.
There are various resources available to Government agencies and businesses with guidance on practical steps to mitigate the risk of malicious cyber activity, including ASD's Strategies to Mitigate Targeted Cyber Intrusions, the Information Security Manual and guides published by CERT Australia.
RELATED KNOWLEDGE
Clayton Utz communications are intended to provide commentary and general information. They should not be relied upon as legal advice. Formal legal advice should be sought in particular transactions or on matters of interest arising from this bulletin. Persons listed may not be admitted in all states and territories.
